Zharoznizhuvalny for children is recognized as a pediatrician. Allegedly, there are situations of inconvenient help for feverish women, if the children are in need of giving innocently. Todi dad take on the versatility and constipation of fever-lowering drugs. How can you give children a breast? How can you beat the temperature of older children? What are the best ones?
Federal Agency for Health of the Russian Federation
"Petrovsky College"
from the discipline "Computers and Telecommunications"
Topic: "Designing a new local numbered framing"
Vikonav: Kurilovich N.G.
Revision: Markulov Yu.P.
Saint Petersburg 2010
Entry
Stage 1.Infological information about automation
Stage 2. Design stage
Stage 3. Razrakhunok of the configuration of the hem
Visnovok
Entry
Our hour is characterized by a burgeoning development of telecomunication technologies.
The unification of computers at the hedgehog made it possible to significantly improve the productivity of practice. Computers vikoristovyatsya yak for virobniki (or office) needs, so navchannya.
A local net is a whole group of interconnected computers, servers, printers, roztasvanih at the boundaries of the buddy, office and office. Local fingering gives the ability to trim spilny access up to to separate folders, files, possession, new programs, etc.
Victory of resources in the local scale gives the opportunity to reduce the financial performance of an enterprise, to raise the level of safety in securing important tributes, to speed up the hours of business in the field of business development
Computers can be connected with oneself, vicarists and middle-class people can be accessed: twisted pair), optical conductors (optical cables) and through a radio channel (non-mobile technologies). Dropped calls are established via Ethernet, drowned - via Wi-Fi, Bluetooth, GPRS, and others. Orema is a local numbered netting, it can be a gateway with other local nets, as well as a part of a globally numbered netting (for example, the Internet), because it is connected to it.
LAN (Local Area Network) - a local fencing, designed for connecting territorially grouped fencing attachments. All wall attachments on the central LAN can display information about the MAC addresses of the stand-alone network adapters and exchange data on another (channel) equal seven-world OSI model.
Main LAN passes:
1. Decrease of navantazhennya on the hem
a. Determination of working people of corystuvachіv at the functional group, even if there are unfortunate unsanctioned data exchanges on the channel channel.
b. Razmezhuvannya access to servers and printers.
c. Intermediate access to the Internet
d. Reciprocating the isolation of segments in the hedge, but also the vicorist hedge of the netting of the protocols (for example: the virtual hedge of the IPX coristors, the virtual hedge of the Apple coristuvacs)
3. Reduction of vitrates for exploitation
a. Low rate of change, changes and additions of knitted coristas
b. Change of number of non-corrosive ports of commutators
4. Adjustment of the requirements and improvements of the cost
a. Isolation of broadcast-storms
b. Localization of faults has been accelerated
c. Greater control over traffic
d. Effective vikoristannya ip address
LAN shortcomings:
1. Stirring cob vitrates
2. The need for additional support for personnel.
Stage 1. "Informatization of information about automation"
Cіlі and zavdannya
The main staff of the course project is the design and development of peer-to-peer primary LOM on the topology "Zirka" and "Zagalna bus" OIPTS Petrivskoe College.
Computers will be vikoristovuvat students with the method of teaching, carrying out practical to occupy. Merezha is guilty of failing to function without interruption in the interplay of the development of the new generation, which is found in the middle of the net.
List of basic disciplines
Table 1. List of primary disciplines and PZ, required for them
The skin working station will be equipped with a 32-bit operating system Window 7 HomeBasicDVD (RUSDVD). Such a vibration will be explained by the way, that before the warehouse of Windows 7, there were no projects that were switched on from Windows Vista, as well as innovations in the interface and in the programs and there are many more possibilities, depending on the alternatives. Windows versions that is more optimized.
Part of one license OS MS Windows 7 Home Basic 32-bit Rus 1pk OEI DVD to become one PC (working station) 3799 rub. Otzhe, for 34 working stations the foreign part becomes 129166 UAH.
Workstation security software
In addition to the operating system, at workstations it is necessary to install a basic package of utilities application programs to display the LOM software.
1. MS Office 2007 Professional Win32 Rus AE CD BOX (for newbies)
Table 3. System vimogues up to MSOffice Professional
2. KOMPAS-3DV12
Table 4. System vimogs for KOMPAS-3DV12
3. Acronis Disk Director 11 Home
Table 5. System options for Acronis Disk Director 11 Home
Typical configuration of a robotic station
Table 7. Role of the working station
| Completing | Product Description | Partnership |
| Frame | InwinEMR-006, microATX, Minitower, 450W, Black / Silver | 2290 bunk |
| Motherboard | Gigabyte GA-H55M-S2H, iH55, Socket 1156, 2xDDR3 2200MHz, 2 x PCI Express x16 + Integrated Intel HD Graphics, 6 x SATA II, LAN 1 Gbit, microATX | 3290 RUR |
| Processor | Intel Core i3 530 2.93GHz, 2х256 kb, 4 Mb, LGA1156 BOX | 4390 RUR |
| Operational memory | Kingston HyperX (KVR1333D3N9K2 / 2G) Kit of 2, DDR3 2048Mb (2x1024), 1333MHz | 1590 p. |
| Hard disk | Western Digital WD5000KS / AAKS, 3.5 ", 500Mb, SATA-II, 7200 pro / hv, cache16Mb | 1840 p. |
| Video card | Inbuilt video adapter | 0 bunk |
| Optical drive | Asus DRW-24B3ST, DVD RW, SATA, Black | 1090 bunk |
| LAN | Wired 1Gbit adapter | 0 bunk |
| Monitor | Samsung EX1920, 18.5 "/ 1366 х 768 pix / 16: 9, 1000: 1, DC - 5,000,000: 1/250 cd / m² / 5 ms, D-Sub / DVI, TFT Black | 5990 beds |
| Merezheviy filter | Vektor Lite, 1.8 m | 399 p. |
| Attachment introduction | Logitech Desktop MK120 Black Keyboard + Misha Set | 680 bunk |
| ONCE: | 21560 bunk |
At the same time, the part of one workstation became 21560 rubles. The heirloom was designed to be stored in 34 workstations, which costs around 733,000 rubles.
The type of configuration is given in the form of information on the website of the Computer Center KEY store. (http://www.key.ru/)
Visnovok on the first stage
After the completion of the robot on the first stage of the course project with computers and telecommu- nications, I have compiled a list of all software security installed on the working stations. The bucket is stacked according to the type of configuration of the robotic station with urahuvannya systemic vimogs, applied and systemic PZ, moreover, the necessary computation of memory on a hard disk was calculated by the method of computation of memory required for PZ. The operative memory of the processor is stored in the systemic devices with a margin of 30%.
Stage 2. Design stage
Cіlі and zavdannya
By another stage of the course project є the development of the specifics of communal ownership, the implementation of robots and plans of working primitives, which can be combined in the LOM, because of the intended rosetting of PCs and cable lines in them.
Before the skin attachment, it is necessary to specify the specificity of the communal possession, for which the lateral plan of all the primitives of LOM and the specificity of all possession is necessary.
Vibir cable systems
The vibration of the cable system is to keep up with the intensity of the cut-through traffic, it can help to get the information, the maximum visibility, and the characteristics of the cable, the rate of implementation.
Vita pair (twisted pair) is a type of cable connection, which is one or more pairs of insulated conductors, twisted between themselves and covered with a plastic sheath. The twisting itself allows for the detection of deyakim types of transcript, which can be guided on the cables. Name for Ethernet 10Base - T you can use a cable that can move your bets. One for transmission and one for reception (AWG 24).
Thin coaxial (RG-58 abo "Thin Ethernet") is an electrical cable that can be stored from a central provider and a screen, which can be used separately, and used to transmit high-frequency signals. Khvilovy opir 50 Ohm, diameter 0.25 inches, the maximum length of the cable segment is 185 meters. Rule 5.4.3. 10BASE2 standard . The coaxial cable is more efficient, extinguishing the signal in a new way less than the torsion of the pair.
Pasivne less possession LOM includes:
1) The cable itself
2) Wall sockets RJ-45
3) Patch panels
4) Repeat
5) Patch cords (subscriber cords) with RJ-45 roses (cable for connecting wall sockets with roses on a computer's adapter).
The laying of cable systems for working applications is based on a folded plan based on the specificity of the specific materials and components of this application.
When designing cable systems, it is necessary to provide the characteristics and interconnection of the existing cable systems:
1) The maximum amount of cable segment is of the same type
2) Cable throughput
3) Availability of the installation, which will secure the interaction with the Space with the other cable systems
Having analyzed the characteristics of different types of cable, physical rosetting of computers, the vibrating cable is "twisted pair" 10Base-T and thin coaxial.
Vibration topology
Merezheva topology - a way of describing the configuration of the framing, the scheme of rosetting and setting up the fenestration.
There are many options for topologies for designing and encouraging the heights. Below is a description of the actions of them.
Bus topology
The topology of the main bus is the transmission of one cable, which connects all computers of the mesh. As a matter of fact, it is necessary to be supervised by a working station, to expand on all computers of the fancy. The skin machine is revolving - to whom is it addressed? Specialists come in to get in so that the robots didn’t use the overhead cable for one hour to transmit and receive the data.
With such a connection, the computers can transmit information only if necessary, so that the line is connected. The information will be transferred to the іnshomu vipad will be controversial in any way (conflict, colossus).
Fig. 1 Topology Zagalna bus
Tires are not scary about new computers, fragments of all other computers can be processed normally. In addition, the splinters will lose one cable, and the robot will break down. Maybe you’re not scary, and having shaved the cable, splinters in a whole lot will be lost on two prints. However, through the special features of the extension of the electrical signals along the lines of the connection, it is necessary to transfer the inclusion on the tires of the special attachments - Termіnators.
When prompted great hedgehogs This is the problem of interfering with the connection between universities, in such a case, they break into segments, such as using small annexes - repeaters, hubs and hubs. For example, the Ethernet technology allows the driver to use the cable for the trocha connection more than 185 meters.
Fig. 2 Topology of the external bus with repeaters
Perevagi:
1) The small hour of the rise of the hedge;
2) Cheapness (it is necessary to use less cable and fenced attachments);
3) Simplicity of nalashtuvannya;
4) Going out of the fret of the robotic station does not match the robots.
Incomplete:
1) If there are problems in the framing, like shaving off the cable, going out of the fret of the terminator will increase the value of the robot to all the fences;
2) Foldable localization of faults;
3) With the addition of new working stations, the productivity of the hem will decrease.
Zirka topology
Zirka is a chain of topology with a clearly visible center, before which subscribers are connected. The entire exchange of information is carried out through a central computer, since such a rank is even more important, so none of them, except for the hedge, cannot be engaged.
As a rule, the central computer itself is needed, and all functions of exchange management are relied upon. There are still conflicts in the net with the topology of the "star" in the principle of unhelpfulness, some of the management is more centralized.
Going out of the fret of the peripheral computer doesn’t seem to be on the function of the part of the net, but if it’s like the central computer, it’s not going to be the case. That is why it is necessary to live special visits and to advance the reliability of the central computer and the same device. Shaved be-like cable abo short confusion With a new topology, "zirka" will interrupt the exchange with one computer, the protector of computers can normally feed the robot.
Fig. 4 Zirka topology
At the star on the skin line there are only two subscribers: the central one and one from the periphery. The most frequent way to get the job done is to get two lines of communication, the skin from which information is transmitted only in one straight line. In such a rank, on the skin line there is only one receiver and one gear. All the suttas will forgive less possession in the context of a tire and will relieve the need for pre-existing termi- nators. The problem of extinction of signals in the line of communication is also found in the "star" is simpler, lower in the "tire", even if the signal of one level is accepted.
Behind the topology bags "zirka" you can have different views and topologies, as well as expandable. For example, it is possible to add a concentrator, which is already obvious in the hem, to add a concentrator with a singular number of ports and by themselves to add new koristuvachiv in a hem.
The topology will be used on the Vita Pair cable system, if you want to install a hub with an additional port for connecting with an additional coaxial cable, you can use it. For example, it is possible to bring to a sleeping hedge more than a number of working stations from a topology, for example, a "bus". In this rank, from the center of topology, it is possible to build practically whether to change the topology.
Perevagi:
1) when going out of the way of one workstation, it doesn’t look like it’s on the robot all the way out;
2) good scaling of the hem;
3) a slight shake of iniquities and obrivіv at the festoon;
4) visoka productivity of the hem (for the correct design);
5) the flexibility of administration.
Incomplete:
1) going out from the fret of the central concentrator will turn into a non-proprietary hem (or a segment of a net);
2) for laying a net, more cable is often required, less for larger topologies;
3) the number of working stations at the hem (or segments of the hem) is surrounded by a number of ports at the central concentrator.
On the basis of all the information provided about the topology, encourage the hedge, its passages and shortcomings, as well as the characteristics folded festoon, vibrate topology "zirka-tire".
Obstezhennya opposite prim_shennya.
Usi ob'єkti (rooms 30, 36 and 39) are on the third stage for practical activities to take students on a PC. In cikh cabins, we carry out an informational systematic and flexible scheme, and a number of possessions are required.
Below is the plan of the first ob'єkta of the hem, room No. 30. There are 15 working stations in its warehouse.
Scheme 1. Plan of the office # 30
Table 8. Specification of the communal ownership of the office No. 30
| № | Naymenuvannya | Single vimir | Quantity | Price, rub.) | Price (rub.) | Note |
| I Vitrate materials | ||||||
| 1 | metri | 44 | 140 | 6167 | 3m on the go along the wall, | |
| 2 | Coaxial cable RG-58 C / U, coil 100m | metri | 43 | 14 | 619 | 3m on the go along the wall, |
| II Complementary virobi | ||||||
| 1 | bracket 19 "" 3U | Things | 1 | 638 | 638 | |
| 2 | Concentrator 16 xRJ-45, 1xBNC, 19 " | things | 1 | 2613 | 2613 | |
| 3 | BNC connector RG-58 (P) crimp | things | 31 | 16 | 496 | |
| 4 | BNC connector RG-58 ( M) stamped | Things | 1 | 25 | 25 | |
| 5 | BNCT connector (M-M-M) | Things | 15 | 67 | 1008 | |
| 6 | Cable BNC (R) - BNC (R) 1.5 m | Things | 15 | 84 | 1272 | |
| 7 | BNC terminator 50 Ohm | things | 1 | 32 | 32 | |
| III Installation | ||||||
| 1 | Meter | 35 | 58 | 2030 | ||
| 2 | Stacking the cable in the box | Meter | 34 | 14 | 493 | |
| 3 | Fitting RG-58 BNC-connector | things | 32 | 43 | 1392 | |
| 4 | Mounting the socket (BNCT-connector) at the box. | Things | 15 | 87 | 1305 | |
| 5 | Things | 1 | 725 | 725 | ||
| 6 | Installation of the Concentrator at the stiyku | Things | 1 | 435 | 435 | |
| 7 | Testuvannya LOM | Porti | 15 | 40 | 600 | |
| IV General Party | ||||||
| ONCE: | 19851 |
Another object of the design (room No. 36) includes 16 workstations. The plan is below.
Scheme 2. Plan of office # 36
Mindset:
Table 9. Specifics of the communal ownership of the office No. 36
| № | Naymenuvannya | Single vimir | Quantity | Price, rub.) | Price (rub.) | Note |
| I Vitrate materials | ||||||
| 1 | metri | 262 | 9 | 2599 | 3m on the go along the wall, | |
| 2 | Box 40x20mm rectangular, b_liy | metri | 43 | 140 | 6026 | 3m on the go along the wall, |
| II Complementary virobi | ||||||
| 1 | bracket 19 "" 3U | Things | 1 | 638,08 | 638,08 | |
| 2 | Things | 1 | 768 | 768 | ||
| 3 | Things | 1 | 4832 | 4832 | ||
| 5 | Things | 16 | 57 | 921 | ||
| 6 | Things | 32 | 25 | 819 | ||
| III Installation | ||||||
| 1 | installation of the box on the wall up to 50 mm | Meter | 35 | 58 | 2030 | |
| 2 | Stacking the cable in the box | Meter | 209 | 14 | 3030 | |
| 3 | Installation of an RJ-45 socket in a box | Things | 16 | 87 | 1392 | |
| 4 | Mounting Bracket 19 "" on the wall | Things | 1 | 725 | 725 | |
| 5 | Installation of the switch at the stiyku | Things | 1 | 435 | 435 | |
| 6 | Installation of patch panels in a box | Things | 1 | 435 | 435 | |
| 7 | Things | 16 | 87 | 1392 | ||
| 8 | Testuvannya LOM | Porti | 16 | 40 | 640 | |
| IV General Party | ||||||
| ONCE: | 26684 |
The third object of the project (room No. 39) is to take revenge on its own 3 workstations. The bottom can be a posteriori plan.
Scheme 2. Plan of office # 36
Mindset:
Table 10. Specifics of the communal ownership of the office No. 39
| № | Naymenuvannya | Single vimir | Quantity | Price, rub.) | Price (rub.) | Note |
| I Vitrate materials | ||||||
| 1 | Vita pair cable 8 pc. 5E cat. (PCnet), bay 305m | metri | 56 | 9 | 555 | 3m on the go along the wall, |
| 2 | Box 40x20mm rectangular, b_liy | metri | 22 | 140 | 3083 | 3m on the go along the wall, |
| II Complementary virobi | ||||||
| 1 | bracket 19 "" 3U | Things | 1 | 638 | 638, | |
| 2 | Patch panel 19 "16 ports, cat.5e, universal (PCnet) | Things | 1 | 768 | 768 | |
| 3 | PLANET GSW-1600 16-port 10/100 / 1000BaseTX 19 "switch | Things | 1 | 4832 | 4832 | |
| 4 | Socket 8P8C (RJ-45) category 5e, universal (PCnet) | Things | 3 | 57 | 172 | |
| 5 | Patch cord cat. 5e 0.5m (blue) | Things | 6 | 25 | 153 | |
| III Installation | ||||||
| 1 | installation of the box on the wall up to 50 mm | Meter | 17 | 58 | 986 | |
| 2 | Stacking the cable in the box | Meter | 45 | 14 | 652 | |
| 3 | Installation of an RJ-45 socket in a box | Things | 3 | 87 | 261 | |
| 4 | Mounting Bracket 19 "" on the wall | Things | 1 | 725 | 725 | |
| 5 | Installation of the switch at the stiyku | Things | 1 | 435 | 435 | |
| 6 | Installation of patch panels in a box | Things | 1 | 435 | 435 | |
| 7 | Crossed patch panels | Things | 3 | 87 | 261 | |
| 8 | Testuvannya LOM | Porti | 3 | 40 | 120 | |
| IV General Party | ||||||
| ONCE: | 14079 |
Home plan of the project LOM
Scheme 4. Home plan for LOM
Mindset:
Table 11. Specifics of the territory of the posture by the cabinets
| at | Naymenuvannya | Single vimir | Quantity | Price, rub.) | Price (rub.) | Note |
| I Vitrate materials | ||||||
| 1 | Vita pair cable 8 pc. 5E cat. (PCnet), bay 305m | metri | 130 | 9,92 | 1289,60 | 3m on the go along the wall |
| 2 | Box 40x20mm rectangular, b_liy | metri | 85 | 140,16 | 11913,60 | 3m on the go along the wall |
| II Complementary virobi | ||||||
| 1 | Commutator 5-port power supply | Things | 1 | 1285,76 | 1285,76 | |
| 2 | RJ-45 plug for round baguette cable | Things | 8 | 2,88 | 23,04 | |
| III Installation | ||||||
| 1 | Mounting the box (< 60 мм) на стену из легких материалов высота >2 m | Meter | 68 | 72,50 | 4930,00 | |
| 2 | Laying the cable in a box with a height> 2 m | Meter | 104 | 17,50 | 1820,00 | |
| RJ-45 connector crimp | Things | 8 | 43,50 | 348,00 | ||
| IV General Party | ||||||
| ONCE: | 21610 |
Visnovok of another step
Proceeding above another stage, the plans of the chiefs were folded, the plan of the LOM was laid out, and the tables of the vitratic materials were folded. Information about the number of cables, component cables, as well as about assembly robots and their part is shown in the tables.
The bulk of the vitratic materials, accessories and assembly robots became 82224 rubles.
Stage 3. Razrakhunok of the configuration of the hem
Cіlі and zavdannya
On this stage, it is necessary to lay down the plan for the size of the mesh, from the designations of the working stations, the size of the table, behind the folded plan, the table for the size of the mesh. So behind the folded table, lay down the structural diagram that behind the diagram, scatter the layout of the original design LOM.
Razrakhunok diameter of the hem
The method of measuring the diameter of the hedge can be formatted as tables. The numbers of rows and stubs from them are shown to the identifiers of work stations on the outside plan of the LOM, and the number of rows in the tables is shown by the number of the row and the number of work stations. With a lot of diagonal elements, do not revenge the meaning.
The maximum value in the table and for the size of the hedge in the domain of the number of the given LOM.
Table 12. Frames of the diameter of the hem
| WS1 | WS3 | WS4 | WS19 | WS20 | WS34 |
| WS1 | 29.10 m | 43.42 m | 76.15 m | 98.48 m | 128.41 m |
| WS3 | 29.10 m | 45.74 m | 78.47 m | 103.80 m | 133.73 m |
| WS4 | 43.42 m | 45.74 m | 32.73 m | 156.98 m | 186.91 m |
| WS19 | 76.15 m | 78.47 m | 32.73 m | 144.45 m | 174.38 m |
| WS20 | 98.48 m | 103.80 m | 156.98 m | 144.45 m | 29.93 m |
| WS34 | 128.41 m | 133.73 m | 186.91 m | 174.38 m | 29.93 m |
In order for the project to be designed by the LOM, it is necessary to correct correctly 3 minds:
1. The number of working stations is 1024 approx.
2. Subsequent reception of the PDV signal between two stations is not guilty of changing 575bt.
3. The speed of the inter-frame transition from the hour to the passage of all frames through all the repetitive images 49bt.
Structural diagram of LOM
A structural diagram is given for the description of the LOM with the diameter of the hedge from WS4 to WS34.
Scheme 5. The structure of the mesh between cabinets No. 30 and No. 36
Rozrahunok PDV
When rozrahunka PDV, it is necessary to register with a pre-table and data (footage, type of cable system, structural diagram).
Table 13. Previdkova PDV table
| Segment type | Base of the left segment | Base of the industrial segment | Base right segment | Covering the middle by 1 meter | The maximum amount of the segment |
| 10BASE-5 | 11,8 | 46,5 | 169,5 | 0,866 | 500 |
| 10BASE-2 | 11,8 | 46,5 | 169,5 | 0,1026 | 185 |
| 100BASE-T | 15,3 | 42 | 165 | 0,113 | 100 |
| 10BASE-FB | - | 24 | - | 0,1 | 2000 |
| 10BASE-FL | 12,3 | 33,5 | 156,5 | 0,1 | 2000 |
| FOILR | 7,8 | 29 | 152 | 0,1 | 1000 |
| AUI (> 2m) | 0,26 | 2+48 |
Rozrahunok PDV (from 1 to 4):
Livius Segment1: 15.3 +20.93 * 0.113 = 17.67 bt
Intermediate Segment2: 42 +50.96 * 0.113 = 47.76 bt
Intermediate Segment3: 42 +81.18 * 0.113 = 51.17 bt
Right Segment4: 169.5 +33.84 * 0.1026 = 172.97 bt
Rozrahunok PDV (from 4 to 1):
Livius Segment1: 11.8 +33.84 * 0.1026 = 15.27 bt
Intermediate Segment2: 42 +81.18 * 0.113 = 51.17 bt
Intermediate Segment3: 42 +50.96 * 0.113 = 47.76 bt
Right Segment4: 165 +20.93 * 0.113 = 167.37bt
So, if the value is less than 575bt, you can pass the criterion for the maximum possible response to the signal turnover, with the maximum increase in the amount of 186.91 m.
Rozrahunok PVV
Table 14. Table of byte intervals PVV
| Segment type | Transfer segment | Industrial segment |
| 10BASE-2 | 16 | 11 |
| 10BASE-5 | 16 | 11 |
| 10BASE-FB | – | 2 |
| 10BASE-FL | 10,5 | 8 |
| 100BASE-T | 10,5 | 8 |
Rozrahunok PVV (s 1 on 4 ):
Liviy Segment1: 100BASE-T - 10.5 bt
Intermediate Segment2: 100BASE-T - 8bt
Right Segment4: 10BASE2 - 16bt
Rozrahunok PVV (from 4 to 1):
Livy Segment4: 10BASE2 - 16bt
Intermediate Segment3: 100BASE-T - 8bt
Intermediate Segment2: 100BASE-T - 8bt
Right Segment1: 100BASE-T - 10.5 bt
Given LOM for the PVV criterion I do not change 49bt. This rank, designed by LOM, is represented by a structural diagram, based on . If you do not fix it, you will be able to secure the correctness of the LOM robot if you break the simple rules for configuring the hem.
Visnovok
Pracyuchi over the course project, making the whole cycle of the project and implementation of the given LAN. The boolean was designed by LOM for the primary attachments of one of the buildings of the Petrovsky College for the Ethernet standard with the Vita Para and Thin Coaxial cable for all the parameters, with the 10Base-T and 10Base standards.
Bully carried out the size of the LOM, and the size of the conversion of the local area network using the additional method of bit intervals. This method is used to show how the LOM has been designed and developed according to all criteria for the Ethernet standard.
State budgetary profes_yny navchalny mortgage “Arzamasky adaptable college imeni P.I. Plandina "
solidify
Director of DBPOU
"APK ім. P. I. Plandina "
___________ / S.A. Єrmolaєv /
ROBOCH PRACTICE PROGRAM
PM 02. Organization of the hemline administration
UP.02.01
behind the fach 02/09/02
Computers
Arzamas, 2016
Working program initial practice broken down on the basis of the Federal State Educational Standard for the specialty of the middle professional education09.02.02. "Computers", Regulations on the practice of scientists, which will master the basic professional education programs of middle professional education, approved by the Order of the Ministry of Education and Science of the Russian Federation dated 18.04.2013 No. 291.
Organizational development: DBPOU "APK ім. P.I.Plandina "
Retail distributors: Malova ЄV, vicladach DBPOU “APK ім. P.I.Plandina ".
Scrapped by the Methodical Council of DBPOU “APK ім. P.I. Plandina "
ЗМІСТ
2
RESULTS OF PRIMARY PRACTICE DEVELOPMENT ……
3
STRUCTURE І ZMІST PRACTICAL PRACTICE ...
4
THINK OF REALIZATION IN PRACTICE OF PRACTICE …… ..
5
CONTROL І EVALUATION OF RESULTS IN PRIMARY PRACTICE …………………………………………………… ...
1. ROBOCHO'S PASSPORT BY PRACTICE PROGRAMS
1.1. Program storage area
The working program of the initial practice є with a part of the training programs for the faculty of the middle Lanka (dal PPSSZ), up to the FGOS SPO for the fah02.09.02 Computers, development of the basic types of professional activity (dal - VPD).
1.2 Course of initial practice
I start to practice є Formulating the students ’mind, finding practical information on the cob, within the framework of the professional modules of the PPSSP, from the main types of professional activity for their further mastery of the out-of-town and professional competences from the other specialties.
First time practitioners є:
Providing a dermal student with a pre-professional, necessary and sufficient set of practical skills, important for the formulation of competencies;
The student has learned the understanding of the self-assessment of the power.
Vimogi to the results of mastering the initial practice.
During the course of the initial practice for the types of professional activity, the student is guilty of the mother of the first practical admission and mother vminnya:
Organization of software maintenance and operation of workstations and office equipment of computer fencesOrganization of software maintenance and operation of software maintenance of workstations and servers of computer mesh
Organization of software service and exploitation of active and passive possession of a computer net
Practical support of software service and operation of workstations, active and passive possession and general software safety computer fancy
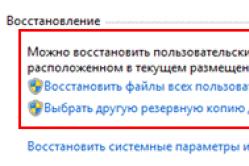
nalashtovuvati local edge in Windows 7;
Windows;
1.3. Number of years to develop robotic programs Initial practice:
Cody of professional competenceNaming a professional module
All years
Rozpodil years by semesters
Initial practice with software security for computers
Usogo
2. RESULTS LEARNED BY A ROBOCHO PROGRAMS OF PRIMARY PRACTICE
As a result of mastering the work programs of basic practice є mastering by students of professional (PC) and external (OC) competences from a new specialty.
OK 1The sense of the day and the social significance of your future profession, your interest in life
OK 2
Organize the efficiency, select the types of methods and methods of displaying professional works, assessing the effectiveness and efficiency
OK 3
Accept the decision of standard and non-standard situations and bear responsibility for them
OK 4
Zdijsnyuvati poshuk and vikorystannya information, necessary for an effective vykonaniya professional enterprises, professional and special development
OK 5
Vikoristovuvati Information and Communication Technologies for Professionals
OK 6
Pratsyuvati in the team and in the team, effectively combining with colleagues, kerivnistvom, supporters
OK 7
Take the responsibility for the work of the team members (pidleglich), the result is
OK 8
Independently from the beginning of the professional development and special development, engaging in self-understanding, it is assimilated to the plan of improvement of the qualifications.
OK 9
Orієntuvatisya in the minds of frequent changes in technology among professionals
3. THEMATIC PLAN І ZMІST OF PRACTICAL PRACTICE
3.1. Thematic plan and master of the initial practice
Code that nameprofessional
modules and topics
initial practice
obsyag
godin
Rivne development
Initial practice with software security for computers
See Rob:
Organization of software maintenance and operation of workstations and office equipment of computer fences
Organization of software maintenance and operation of software maintenance of workstations and servers of computer mesh
Organization of software service and exploitation of active and passive possession of a computer net
Installation and adjustment of applied software protection of working stations and servers. Last backup copy and update of data. Diagnostics of pracezdatnost, usunennya of faults and malfunctions of the operating system and applied software security. Installation, update and visible version of operating systems personal computers... Administration of operating systems; An updated version of the application software for securing personal computers. Updating and visualization of drivers for attachments of personal computers, peripheral attachments and possessions. Updating the microprogram security of components of computers, servers, peripheral attachments and possessions.
1. Installation of the WEB-server
2. Installation of the WEB-server
3. Installation of the WEB-server
4. Configuring the web server
5. Configuring the web server
6. Configuring the web server
7. Relationship with the databases of tributes.
8. Vzaєmodiya with the bases of tribute.
9. Vzaєmodiya with the bases of tribute.
10.Installation and adjustment of drivers
11. Installation of PZ: MS Office, special programs ARMIV.
12.Vikoristannya file manager FAR / those other alternative programs.
13. Servicing disks (defragmentation, cleaning, revision for the appearance of pardons, updating files)
14. Vstanovlenya and nalashtuvannya programs Kaspersky Anti-Virus.
15.Analysis and monitoring of the hedgehog.
16. Installing and configuring browsers Opera, Mozilla, Google chrome, Internet E xplorer
17.Installation and adjustment of postal utilities Microsoft OutLook, OutLook Express.
18.Copying the FTP service behind the browser add-on.
19.Nalashtuvannya ta vikorystannya FTP-kliєnta
20. Establishment of a special program for ARM.
21. Organization of uninterrupted robotic systems with backup and updating of information
22. Updating that vivid version of the operating systems of personal computers.
23. Listing of administrative systems of operating systems.
24. Updating and visualizing drivers for attachments to personal computers.
25. Updating and seeing drivers in peripheral annexes.
26. Updating and seeing drivers in peripheral annexes.
27. Updating and seeing drivers of ownership.
28. Updating the microprogram security of components in computers.
29. Updating the microprogramming of the server components.
30. Updating the microprogram safety of components in peripheral attachments.
31. Updating the microprogram provision of components in the installation.
32. Robot with BIOS. Main BIOS partitions. Computer recovery with by BIOS
33. Procedure BIOS update
34. Diagnostics for BIOS
35.Vstanovleniya software protection of the COP.Operation of software protection of the COP
36.. Differentiation of halls
Promіzhna attestation in formі dif.
4. THINK OF REALIZATION ROBOCHOЇ PROGRAMS OF PRIMARY PRACTICE
4.1. Vimogi to the minimum material and technical safety
Realization of robotic programs in the initial practice of transferring
1.Coating:
PC, PZ, okremі accessories, peripheral possession (microphone, speakers), office equipment (printers, scanners)
2.Instruments and attachments:
Computers - 24.
3. Get the chance to:
Electronic dovidnik "PC"
4.3. The headquarters of the organization of the lighting process.
Primary practice is carried out by the masters of the virobnicheskoy navchannya and / abo viclades of the professional cycle. Realized in a concentrated manner.
4.4. Personnel will be safe from the initial process.
Maystri virobnichego navchannya, vicladachi
4.5 Information security of the initial practice
Main dzherel:
Kelim Yu.M. Computational technology: handbook for students in the middle of professional education. - M .: Vidavnichy center "Academy", 2014. - 368 p. (electronic version)
Maksimov N.V. The architecture of the EOM and numerical systems. M .: FORUM-INFRA-M, 2013
Tanenbaum Ege. Computer architecture. SPb .: Peter, 2013
Dodatkov_ dzherela:
O. V. Kuzin The architecture of the EOM and numerical systems. M: FORUM-INFRA-M, 2006
Electronic version of the handlers:
B. V. Ilyukhin Hardware for the EOM. Tomsk: Tomsk educational institution. center of distances. coverage, 2005
Kolesnichenko O.V. The architecture of the PC. SPb .: BHV-Petersburg, 2010
Stepanov O.M. The architecture of computational systems and computer fences. SPb .: Peter, 2007
Internet resources:
ЕОР: electronic dossier "PC"
http://nn.nix.ru/
http://pusk.at.ua/publ/1-1-0-2
4. 6 Before organizing an attestation and assessing the results of the initial practice
The attestation of the initial practice is carried outat the form differentiated hall on the last day of the initial practice on the basis of the possessed cabinets of the college.
Students are allowed to qualify for certification generally The program of the initial practice is that of the schoolboy that is the name of the initial practice.
In the process of attestation, an examination is carried out of the formulation of practical skills and knowledge of the cob, practical information of the robot in part of mastering the basic type of professional activity, mastering of foreign and professional competences.
Assessment for the initial practice of visas
catching up lines and making up calls for a day of practice,
pay attention to protect the pratsi, the rules of the technology of safety and security,
for the wisdom of the day of the skin day in the general community,
demonstration nabootih umin,
an explanation of the algorithms for the viconanny nabutikh umin.
demonstration of the message of goodness and the introduction of the necessary information from the global grid on special resources and of the storage of the good during the demonstration of the practical mind;
demonstration of pratsyuvati at the team and individually.
5. CONTROL І EVALUATION OF RESULTS IN IMPLEMENTATION BY PRACTICE PROGRAMS
The control and assessment of the results of mastering the initial practice should be the standard of practice in the process of conducting the chiefs to take, independent performance by the students of the factory, the performance of practical conversion work. As a result of mastering basic practice within the framework of professional modules, the student undergoes an industrial attestation at the formhall / differential hall.
Expert assessment for skin dayExpert assessment of the written letter for the skin day
Expert assessment of the result of the skin day
Nabuty practical dosvid:
exploitation of working stations of computer fences
Nabuty vminnya:
select the program for configuring a personal computer, a server and peripheral possession, which is optimal for the creation of a koristuvach;
to prevent the confusion of components in personal computers and servers, peripheral attachments and possessions;
customize the parameters of the functionality of the software security;
diagnostics of software security;
usuvati malfunctions and malfunctions in the robots of software security;
select the software for configuring a personal computer, a server, which is optimal for all clients;
stand up and administer Operating systems on personal computers and servers, as well as adjusting the interface of the koristuvach;
assess the productivity of the calculating system;
vikonuvati optimization of the robot of a personal computer (workstation);
keruvati files of tribute on local, familiar annexes, as well as on disks of local computer fences in the Internet;
help navigate web resources to the Internet behind the aid of a web browser;
good news, sorting and analysis of information behind the addition of sound Internet sites;
pіdtrimka koristuvachі in hem;
nalashtovuvati local edge inWindows 7;
nalashtovuvati access to the Internet from local fences;
connect and set up a grid printer in the OSWindows;
Analyze the hemstitch traffic with the help of the hedgehog monitor
Zmist
Entry
Chapter 1 Understanding and Classification of Computers
1.1 Assignment of computer fences
1.2 Classification of computers
Chapter 2. Basic types of numbered fences
2.1 Local numbered fingering (LAN)
2.2 Global Computational Fringe (GWP)
Visnovok
List of Victorian literature
Entry
Entry of Russia in the light of information space is more difficult for itself with the best victorious new information technologies, and in the first place, computers. At the same time, it is very growing that it is clear that the power of the clerk is clearly visible in order to provide services to his customers, as well as in the case of new vigorous organizational-economic establishments.
Rurally, in terms of the current computer system, the ability of and the characteristics of such as a whole, quite simply outweigh the common indicators of the downtime of the sum of storage elements in the range of personal computers for the duration of their availability.
Reverses of computers' frizzy zoomed out wider information systems akhkreditno-financial sphere, bodies of sovereign management and self-assembly, enterprises and organizations.
Computer fences and framing technologies of processing and information became the basis for stimulating modern information systems. The computer slid not as an edge of the prism, but as a "wink" in the computer. hedge resources that іnshim koristuvachy weezh.
Over the last few years, the global netherness of the Internet has been reimagined on a light scale. Merezha, who until recently was victorious, was surrounded by a number of officials, state services and educational institutions at their professional performance, became available to the great and small corporations and to provide
By means of the given coursework robotics є learning about the basics to encourage the function of computer fences, organizing the robotics of computer fences. To achieve the delivered item, it is necessary to display a number of buildings:
Knowledge with computer fences, vision of their features and views;
Characteristics of the main ways to induce and fit (topology);
Vivchennya scientific-methodical literature for food
Chapter 1 Understanding the Classification of Computers
1.1 Appropriate computer fingering
The main feature of computer fences is the quality of resources and interactive communication, both in the middle of the same company, as well as behind the fringes. Resources - prices, accessories and peripheral attachments, such as a disk drive, printer, misha, modem or joystick.
Computers that enter the following functions before the screen display:
Organization of access to the hem
Information transfer management
Above the numbered resources and services to the bastards.
In this hour, the local computers (LANs) were numbered even wider. Tse viclikano kіlkoma reasons:
Ob'dnannya computers from the commonwealth permitsє significant economy penny koshty for replacing vitrates on computers (to add mother's disk space to the file server (head computer) with software installed on the new computer, so that the desktop can be used with workstations);
Local hedges allow you to send a screen for sending messages to your computers, which allows you to transfer documents from one computer to your computer in the shortest term;
Local hedges, due to the obviousness of special software security (PZ), serve for organizing special file records (for example, accountants on decile machines can process the wiring of the same book).
Apart from that, in some spheres of activity, it is simply uncomfortable to do without a crowbar. To such areas there are: banking on the right, warehouse operations of great companies, electronic archives of libraries and in. From these spheres of skin care, a working station is taken in the principle that all information cannot be taken (in the main, through a great deal).
A globally numbered net is a net that is from one computer to the other, geographically, one from another. It is transformed into a local network of larger communal services (satellite, cable, etc.). A global hedge is a single local hedge.
The Internet is a global hedge, which has served as a whimsical prelude and primary groups, whose interests dwelt right up to access to supercomputers, and is becoming more and more popular in the modern world.
1.2 Classification of computers
Behind the way of organizing the pattern, one is drawn to the real and the piece.
Piecemeal (pseudo-rehearsal) allow the connection of computers at once through the last or parallel ports and do not require additional attachments. One of the calls for such a hedge is called a null-modem call (the modem is not victorious). Self-service is called null-modem. Piecemeal fancy work, if it is necessary to transfer information from one computer to the other. MS-DOS and windows secured special programs for the implementation of a null-modem connection.
Real fathoms allow the connection of computers behind the addition of special attachments for communication and the physical middle of the transmission of tributes.
/> Lost widths of the pattern can be local, global, regional and local.
Local Area Networks (LAN) - a whole group (communal system) of a relatively small number of computers, which share the same socially victorious midpoint of transmission of dates, to be close to each other (call in the radio no more than 1 -2 km) with the help of a special victorious resource in our computers
Globally numbered wedge (WAN WAN - World Area NetWork) is a wedge that is from one computer, geographically large from each other. It is transformed into a local network of larger communal services (satellite, cable, etc.). Svitova framing is a single local framing.
Miska network (MAN - Metropolitan Area NetWork) is a network, which will serve as a service provider for the information consumers of the great place.
Regional - roztasvani on the territory of the city of the region.
So it’s itself, for the next hour, I’ll see this kind of hedge, like a bank, like a brand of a corporate hedge of a great company. Obviously, the specifics of bank performance are presenting the bank's information to the systems to retrieve information in the bank's computers. Not less important is the role in prompting the corporate net to display the need to secure the uninterrupted and uninterrupted robots, some of the short-time beats from the robots can be brought up to the gigantic beats.
For the proper development of the form and state of the net. Seems to have the same organization and to be spread on the territory.
Sovereign fences - fences, such as in sovereign structures.
For high-speed transmission of information, computers will go to low-, middle-and high-speed.
low-speed (up to 10Mb / s),
average speed (up to 100Mb / s),
visokoshvidkіsnі (monad 100 Mb / s);
The main reason for this is that the technical solutions can be used for different configurations (either, it seems, architecture, or topology).
In the case of the topology, information is transmitted by a closed channel. A skinny subscriber without any need to be tied up with two of the most suitable sousids, I would like, in principle, to call you a subscriber of a wedge.
At the zirkopodibniy (radio) at the center there is a central computer, which will call the subscribers one by one one after another.
At the bus configuration, the computers are connected to the channel (bus), which is connected to them, through which they can communicate with each other.
A tree-like computer has a "head" computer, which is ordered by computers of the offensive level, etc.
Besides, you can configure without a clear character of the sounds; boundary є povnoz'yazkova config, if a skin computer has a net without any ties with a be-like computer.
At a glance, the organization of interconnection of computers, the net to peer-to-peer (Peer-to-Peer Network) and the server (Dedicated Server Network).
All computers are peer-to-peer. Whether you are a clueless person, you can get access to the dues, which you can use on any computer.
Peer-to-peer hedges can be organized behind the aid of such operating systems as LANtastic, windows "3.11, Novell Netware Lite. Assigned programs to work with DOS, as well as Windows. Peer-to-peer units can be organized also on the basis of all 32 operating systems. Windows 9x \ ME \ 2k, Windows NTworkstation versions, OS / 2) and others.
Peer-to-peer heirlooms:
1) the easiest to install and operate.
2) DOS and Windows operating systems can use the necessary functions to enable peer-to-peer gridding.
There are not many peer-to-peer hedgehogs in the community, so it is difficult to communicate the information to the information source. That is how such a way of organizing the hedge is victorious for the hedge with a small number of computers and there, for the sake of the donation, we are not very important.
In the hierarchical grid, when you install a grid, you see one or more computers that manage the exchange of data according to the grid and the generated resources. Such a computer is called a server.
Be it a computer that can access the server's services, call it a client of a net or a workstation.
The server in the hierarchy is a chain of resources that can be distributed. The server itself can be a client only the server is bigger viskogo rivnyaієраrhії. To that, the "hierarchies" are called "fences" from the seen server.
The servers are equipped with high-performance computers, perhaps, from a number of parallel-working processors, from large winchesters, from high-quality fancy cards (100 Mb / s and more).
The Іnrarchichna model of a hemline is very beautiful, but only allows to create the most effective structure of a hemisphere and more rational development of resources.
It is also a triumphant heirloom є a great rivn for a tribute.
Until shortcomings in the hierarchical fences, in proportion to the peer-to-peer fences, there should be:
1) the need for additional OS for the server.
2) greater viscosity of the installation and modernization of the framing.
3) The need to see an outside computer yak a server.
Chapter 2 Basic types of numbered hems
2.1 Localized framing (LAN)
Local units (LZ EOM) unite a relatively small number of computers (change from 10 to 100, if you want to start up and start more) in the boundaries of one application (initial version), install the computer The traditional name - local numbered framing (LAN)) - shvidsh danin in that hour, if fencing in the main vikoristovyvayutsya and virіshennya numbered zavdan; The corridor of the LZ is explained by the fact that 60% to 90% of the required setting of the information of the circulating system is in the middle, it does not require the name input.
Great inflow on the LZ branch has celebrated the opening automated systems management of enterprises (ACS). Automated control systems include a number of automated working machines (AWP), control systems, control points. The best of the best in the field, in which LZ they brought their efficiency - the mainstream of the class calculating technology(KVPT).
Establishments for relatively small dinners have a line connection (as a rule, not more than 300 meters), it is possible to transfer information to digital viewer with high speed transmission. On larger sites, such a method of transmitting unacceptable through the inevitably extinguishing of high-frequency signals, in these drops, it is brought to the bottom of the advanced technical (digital-analogue conversions) and software (protocols for correcting pardons and etc.)
A characteristic feature of the LZ is the visibility of all subscribers in a high-speed channel, the transmission of information in a digital view.
Find the conductive and dull channels. The skin of them is characterized by the singing meanings of the suttas from the point of view of the organization of the LZ parameters:
Broadcast transmissions of tributes;
The maximum amount of food for the line;
Pereskodozachchenostі;
Mechanical engineering;
Ease and ease of installation;
Part.
In the given hour, call to stop the chotiri tips and festoon cables:
Coaxial cable;
Vita steam is unprotected;
Twisted steam is stolen;
Fiber optic cable.
The first three types of cables transmit the electrical signal to mid-range providers. Fiber optic cables transmit light over the fiber optic fiber.
Most of the heatsinks are tolerated by the number of cable options.
Coaxial cables are stored from two conductors, separated by insulating balls. The first shalizolyatsiyu otochen the central mіdniy provіd. A whole ball of braiding is the call of the call guide, who is the screen. Most extended coaxial cables are available and thin Ethernet cables. This design will prevent overshoot protection and less signal loss at the building.
The size of the cable (close to 10 mm in diameter) and thin (close to 4 mm) coaxial cable. Volodiyuchi passes on cross-codes, mtsnosty, dvzhiny ligoyu, this coaxial cable is more expensive and foldable in installation (it folds more easily through cable channels), it is not thin. Until the last hour, a thin coaxial cable is a clever compromise between the main parameters of the LAN connection and in Russian minds the most common way for organizing great LZ enterprises and installations. However, it’s more expensive to make cables, so I’ll reduce the transfer of tribute to a greater number of days and less sensitive to electromagnetical re-codes.
The bet bets are two leads, twisted at once by the width of an inch to protect the operator from the electromagnetical transitions and the utilization to the dance or the electrical support. For others, as a rule (we will live for such a dart, є "IBM type-3." telephone call... However, picking up a telephone dart, especially if there are changes in the future, can solve great problems. Crossover can also signal signals that are transmitted to a closed loop in telephone lines, so that the local cable passes through the cable.
It is also important to note that telephone darts do not have to be installed on a straight line. The cable, which has two orders for the distribution of the connection, can for some reason bypass half of the wake-up call. Underestimation of the cable's performance can lead to the fact that it is possible to change the maximum permissible amount of the cable.
The stolen twists of the paris are similar to those who are not stolen, for the blame of the fact that the stench of viciousness is more likely to be carried out and stolen from the outpouring of the insulator. The most widening is the type of such a cable, which can get stuck in local framing, "IBM type-1" twisted pairs uninterrupted wire. In the new booths, the most beautiful option can be a "type-2" cable, as it includes a complete line of transmission of given data, as well as an unprotected bet of an uninterrupted wire for the transmission of telephone conversations. In such a rank, "type-2" allows one cable to be used for transmission of both telephone conversations, as well as data on a local grid.
Determine the number of twisted pairs per inch to prevent theft of cable with twisted pairs above the cable systems. ”
Fiber optic cables transmit data from light pulses to "wires". Most of the systems of local hedgehogs in the given hour are available for fiber-optic cable production. Fiber-optic cable can be used for different types of cables. Optical fiber cables I find it transmission; the stench is more hopeful, so it’s not sick until the information packets are lost through the electromagnetical transfer. The optical cable is even thinner and dull, so it can be hassle-free to hassle your transport with more important small cables. However, those who only have an optical cable can handle the building enough, as in the future they are needed for large, flexible fences.
Poki scho price of fiber-optic cable is significant for the middle. With a small cable, the installation of an optical cable is more labor-intensive; Optical fiber sticking is successful.
Mouthless sound on LHF radios can be used for organizing fences near the boundaries of great hangars or pavilions; In addition, mouthless lines can ring out to the far distance segments of local fences at the sides of 3 - 5 km (with an antenna of the type Hvilyovy channel) and 25 km (with a direct parabolic antenna) behind the mind of direct visibility. Organizatsii childless hedgehog sutta in a dear, low-pitched manner.
For the connection of computers for an additional line, the connection of the LZ requires adapters of the hedgehog (or, as they name it, pay for it). Nyvidomishim є: adapters of the first three types:
From them, the remainder of Russia is more widespread. The hedgehog adapter is inserted directly into the main slot of the motherboard of a personal computer and up to the rear panel. system unit pidstykovu. The adapter, of its own type, implements the same strategy of access from one computer to the other.
In order to secure the transmission of donations in the fenestration of the transmission of the given data, it is necessary to use the communication protocols of the transmission of the given - set the rules that are responsible for the transmission of the transmission and acceptance of the parties for the purpose of the exchange of taxes. Protocols are a set of rules and procedures to regulate the order of communication. Protocols are the rules of those technical procedures that allow several computers, when combined into a net, one by one.
Isnu withoutlich protocols. I want all the stench to take part in the implementation of the connection, the skin protocol of the development, the visitor of the development, of the change and of the exchange.
Protocols are working on the latest models of interaction between OSI / ISO systems. The functions of the protocols start with the beginning, in which case it is called pratsyu. Several protocols can be very efficient. Tse so ranks stack, or a set of protocols.
Similarly, the functions of the protocol stack are similar to those of the OSI model, and the protocols are to the same level of the protocol stack. The level of the protocol stack is similar to those of the OSI models. At the same time, the protocols give a further description of the functions and capabilities of the stack.
The transfer of tribute according to the hem, from a technical point of view, is guilty of folding from the last crocs, to the skin of which they report their procedure or the protocol. With such a rank, strict decency of the victorious singers is ensured.
In addition, all of the acts are guilty of being in the same and the same end-date on the skin hemline computer. On a computer-based device, you can go straight from the top to the bottom, and on a computer-won up to the bottom of the mountain.
The submitter computer is based on the protocol of the vison of such projects: breaking the data into small blocks, called packages, with which you can use the protocol, before the package contains the address information, so that the computer receives the message itself, data prior to transmission through the board of the stitch adapter and dais - via the stitching cable.
The computer-won according to the protocol of the vikonuє sami deiї, albeit in the vortex order: accept packets and danikh s mesh cable; data transmission to the computer via the board of the matching adapter; I saw from the packet all the information provided by the compiler, the copy of the data from the packet to the buffer - for processing the data block from the output block, transferring the additional data block from the format, which is the result of the vicorist.
The first computer-editor, and the computer-acquiring need to visually display the skin in the same way, so they came through the edge of the file, they were sent with the updates.
Also, for example, two protocols will be broken down into packets in a simple way and given information (after packets, synchronization and rewrite of pardons), so the computer, which can be victorious one way, can іnshy protocol.
Until the mid-80s, most of the local fancy boules were isolated. The stench of the servants was around the company, and it was rather common for the great system. However, if the local hedges reached the highest level of development and the information they conveyed to them, the stench became components of the great hedgehogs. Dani, which are transmitted from one local network to one of the available routes, are called routing. Protocols that allow the transmission of data between fences along decal routes are called protocols that are routed.
Among the most advanced protocols are the following:
IPX / SPX and NWLmk;
· Set of OSI protocols.
2.2 Global Computational Fringe (GWP)
WAN (World Area Network) is a global grid that covers great geographic regions, including both local ones, as well as telecomunications and extensions. The WAN application is a frame relay, which can be used to "expand" any other computers.
For the current year, since the geographic framework of the wedge is being developed, there are only one number of people from different places and powers, LOM will be transformed into a globally numbered wedge [WAN], and a number of computers can be installed in as many as several
The Internet is a global computer for the whole world. The current Internet is close to 15 million subscribers in more than 150 countries of the world. Shomisyatsya size of hemispheres grows by 7-10%. The Internet will set up as a bi-core, so I will not get the links of the new information framing, so I will follow the different settings in all the light, one by one.
As soon as the fancywork was victorious, it was only the middle of the transfer of files and the occasion of electronic mail, then the folding of the established access to resources is growing. Closely three rocky in that, there will be a branch of the shell, so that the function of a fancy joke can be adjusted and access to updated information resources, electronic archives.
The Internet, which served as a whimsical prelude to primary groups, whose interests stretched as far as access to supercomputers, is becoming more and more popular with the dylovy world.
The company is fast, cheap global communication, quickness for carrying out business robots, available programs, a unique database of Internet connections. The stink of looking at the globally heirloom yak complementing his local hems.
With a low service charge (often the fee for a victorious line or a telephone is not fixed), you can deny access to the commercial and non-commercial information services of the United States, Canada, Australia and the Pacific. In the archives of free access to the Internet it is possible to know the information practically in all spheres of human activity, fixing new scientific displays until the weather forecast for tomorrow.
In addition, the Internet provides a unique opportunity for cheap, reliable and confidential global communication in all its light. The price is even more effective for companies that can show their own files in the whole world, for transnational corporations and management structures. Zazvychay, vikorystannya Internet infrastructure for international communication is much cheaper than a direct computer call via a satellite channel or via a telephone.
Electronic mail is the most popular service for the Internet. They send their address by e-mail about 20 million. Posilannya leaf by electronic cost significantly cheaper than posilaniya zvychay leaf. In addition, sometimes, an email message is sent to the addressee for a few years, so as an extraordinary sheet can reach the addressee a few days, or even a few days.
In a given hour, in the Internet network, it is practically possible to use all kinds of communication lines from low-speed telephone lines to high-speed digital satellite channels.
In fact, the Internet is stored from without local and global hedgehogs, it is necessary for small companies and enterprises, which have tied a ring between themselves with different lines.
Yak and in any kind of hedge in the Internet ісnu 7 rivnіv in relation to mods between computers: physical, logical, hedgehog, transport, rіven sessions of communication, representative applied rіven. As a matter of fact, up to the cutaneous ryvnya in the interaction of the modalities of the set of protocols (that is, the rules of interaction).
The protocols of the physical level are based on the characteristics of the link between computers. On the Internet, one can practically use all of them in a given hour to connect from a simple dart (twisted pair) to fiber-optic lines (FOLZ).
For the skin type of the line link, a separate protocol of the logical level has been broken down to handle the management of the transmission of information over the channel. The protocols SLIP (Serial Line Interface Protocol) and PPP (Point to Point Protocol) are used before the logical level protocols for telephone lines.
For the connection over the cable-local mesh - the whole package drivers of the LOM boards.
The protocols of the hedgehog line are responsible for the transfer of data between the annexes at the small hems, in order to deal with the routing of the packets at the hems. Prior to the protocols of the fusion line, there should be IP (Internet Protocol) and ARP (Address Resolution Protocol).
Transport protocols governing the transfer of data from one program to the next. Prior to transport protocols, there should be TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
The protocols of the session will indicate the establishment, reception and development of the available channels. At the Internet, the cymists are engaged in the same guessing of TCP and UDP protocols, and using the UUCP (Unix to Unix Copy Protocol) protocol.
The protocol of the representative Rivnya is engaged in the service of applied programs. Before the programs are representative of the rivnya, there are programs that run, for example, on Unix-servers, to provide new services to subscribers. These programs include: telnet server, FTP server, Gopher server, NFS server, NNTP (Net News Transfer Protocol), SMTP (Simple Mail Transfer Protocol), POP2 and POP3 (Post Office Protocol), etc.
Prior to the protocols of the applied rivnya, the grades of services and programs are introduced.
The Internet is a hedge, which is constantly developing, for which everything is in advance, we will support, that our country will progress.
/>/>/>/>/>/>/>/>/>/>/>/>Visnovok
Fingerprint computer is a combination of a number of EOMs for the social distribution of information, information, general and managerial staff.
The main feature of a computer's hem is the living of the resources and the functioning of the interactive communication as all the middle of the same company, so
the one behind її between.
The local computer of the net is the price of the computers, connected with the communication lines, so that the potential for the spillover of the resources in our computers will be saved. On the other hand, as simple as it seems, a computer of a net is the price of computers and small annexes, you will not be able to provide information exchange between computers in a blanket without any other information.
A globally numbered grid (GVS or WAN - World Area NetWork) is a grid that is from one computer, from a geographic perspective to each other. Svitova framing is a single local framing.
The Internet is a global computer for the whole world.
In fact, the Internet is based on the lack of local and global framing, which is appropriate for industrial companies and enterprises that interconnect with different lines.
List of Victorian literature
1. "Internet at Vasbudinku", S. V. Simonovich, V. І. Murakhovskiy, TOV "AST-Pres Kniga", Moscow 2002.
2. Gerasimenko V.G., Nesterovskiy I.P., Pentyukhov V.V. that in. Numbered hedgehogs that will be taken to the zahist: Navchalny posibnik/ Gerasimenko V.G., Nesterovskiy I.P., Pentyukhov V.V. that in. - Voronezh: VDTU, 1998 .-- 124 p.
3. Tizhnevik for entrepreneurs and faculty at the information technologies of ComputerWeek Moscow.
4. Magazine for koristuvach_v personal computers Svit PC.
5. Kamalyan A.K., Kulov S.A., Nazarenko K.M. that in. Computers of the fringe and help the information manager: Navchalnyy book / Kamalyan A.K., Kulev S.A., Nazarenko K.M. ta in - Voronezh: VDAU, 2003.-119s.
6. Kurnosov A.P. Workshop on Informatics / Ed. O. P. Kurnosova Voronezh: VDAU, 2001 .-- 173 p.
7. Malishev R.A. Lokalny numbered fantasies: Navchalny book / RDATA. - Ribinsk, 2005 .-- 83 p.
8.Olifer V.G., Olifer N.A. Merezhevi operating systems / V.G. Olifer, N.A. Olefer. - SPb .: Peter, 2002 .-- 544 p .: Il.
9.Olifer V.G., Olifer N.A. Computers Principles, technologies, protocols / V.G. Olifer, N.A. Olefer. - SPb .: Peter, 2002 .-- 672 p .: il.
10. Simonovich S.V. Informatics. Basic course / Simonovich S.V. that in. - SPb .: Vidavnitstvo "Peter", 2000. - 640 p .: il.
Computers Classification of computers. ……………4
Merezh Fast Ethernet. …………………………………………………………..5
Merezheva topology. ……………………………………………………...….eight
Provision of safety of robots at the Obchiluvalny center. ……….12
Computers Classification of computers.
Based on the principles of encouragement, computers go to the local and outward distance (Fig. 1).
Local hedges are set up, as a rule, in one organization or one primacy.
The simplest version of this kind of connection is to connect computers through parallel ports. In general, there is no need to consume it in any pre-existing setting. The guilty ones will be deprived of the extraordinary guides. Such a connection between computers will be established in the boundaries of one room. Vikoristovu to transfer data from one computer to the other. And here you can transfer data without the help of floppy disks. Whether the shell of the operating system is so lucky, the software can be used to transfer the tribute.
In local peer-to-peer fences, computers are connected to the framing through special adapters of the framing, and the function of the framing is adopted by the operating system of the framing. Application of such operating systems є: Novell Personal Net Ware, Net Ware Line, Windows for Workgroups.
All computers and operating systems in local peer-to-peer computers may be the same type. Koristuvachi tsієї hedgehogs can overpower one tribute, vikoristovuvati bedroom printers, magnetic optical discs etc.
At the local high-ranking computer fences, there is one hard-working computer, which is called a server, others; On servers vikoristovutsya special systemically insecure as a result of the system software security of workstations.
More computers are available on the regional and international levels. Regional situations occur in singular regions, for example, powers, and internationally they will not be able to connect your computer with the all-important computer. The application of such fences є Relcom (for the lands of the SND) and the Internet (for all the svitu). In principle, from regional computers, you can go to the Internet.
The connection of computers in regional fences is provided with extraordinary telephone fences and special visions when using special fences through special extensions, which are called modems. The modem converts the signals of two codes from sound signals of a wide range, and navpaki.
The computers of the region (place) are connected through modems and a line connection to a forced computer, which is called a provider. There are 100 providers in Ukraine at a time.
The skin computer koristuvachu, which is connected to the hem, needs requisites (addresses). Provide, vikoristovuyuchi requisites, provide the calls of computers koristuvachiv.
The connection between computers of the other continents is connected to the satellite channels.
Call for your vimogs on the topic "Computer fences. Classification of computer fences" can be substituted with the company "Diplomtime".
Add new version
JOIN
Practice cycle:
The consolidation of theoretical knowledge, taken into account in the educational disciplines: the organization of the EOM and systems, programmatically secure, base danikh, nether EOM and telecommunication, peripheral office;
Knowing about virobnic processes, including vicarious information technology and information technologies;
Vivchennya methods of forming, processing, accumulating and victorious in the viral process of information streams;
Finding a quick fix for the storage of autonomous and complex calculating systems;
Analysis of the amount of shortcomings in the organization's performance.
Practice topic:
Vivchennya principіv induce the function of local numbered hedge at a specific organization.
As a matter of fact, I learned about the virobnicho-technological practice by organizing the company "Snigovik Plus".
The structure of the enterprise: Director Masov Evgeniy Mykolajovych. This order has 20 people: accountant, vantazhniks, drivers, technicians,
Sellers.
MAIN PART
The main principle is inspired by the architecture of the EOM;
Principles, methods and ways of complexing hardware and software inputs when setting up calculating systems, complexes and framing;
Models of methods and forms of organizing the process of distribution software product, Technic virobi;
The main features of the systems for managing databases of data and vikoristannya.
In addition, win maє will appear:
Corrosive technical and pre-written literature, sets of standards for the distribution of a software product, a technical virob;
Vikoristovuvati otrimanі in the process of navchannya knowledge and vіnnya for the competent and technically rimmed distribution of a software product, a technical virob;
Proektuvati software product, technical virib;
Razroblyat programs modular structure;
Zastosovuvati methods that zasobi testuvannya and viprobuvan software product, technical virobu;
Koristuvatisya zasob nahgodennya;
TOV "Snigovik plyus" Zdіysnyu implementation of wholesale products near the metro station Ulyanovsk.
I was doing an internship at a technical education with a curriculum programmer
Vorlamova N.F. Managing the databases of data about the supply of the number of goods that are being processed in warehouses, looking for additional computers with the Operating System Windows 95 or Windows 98 .
In order to save an hour of transferring information from one computer to the other Director of the company, you can create a local border in your organization. Technic viddіl otrimav zavdannya proplast the hem to the skin computer fіrmі. Technical viddil rospochav vikonannya zavdannya.
Something we got on the mission with the project. Local framing from the central Server. Div Dodatok 1
The simplest version of this kind of connection is to connect computers through parallel ports. In general, there is no need to consume it in any pre-existing setting. The guilty ones will be deprived of the extraordinary guides. Such a connection between computers will be established in the boundaries of one chi kilkoh rooms. Vikoristovu to transfer data from one computer to the other. And here you can transfer data without the help of floppy disks. Whether the shell of the operating system is so lucky, I can program the software so that the transmission of the tribute can be guaranteed.
In local peer-to-peer fences, computers are connected to the framing through special adapters of the framing, and the function of the framing is adopted by the operating system of the framing. The application of such operating systems is: Novell Personal Net Ware, Net Ware Line, Windows for Workgroups.
All computers and operating systems in local peer-to-peer computers may be the same type. Cinnamon knots can transfer one to one tribute, vikoristovuvati spilny printers, magnetic and optical discs just.
At the local high-ranking computer fences, there is one hard-working computer, which is called a server, others; On servers vikoristovuyut special system security, as seen from the system software security of work stations.
The main parts of the hedgehog.
For our fusion we have a cable twisted pair or coaxial cable Twisted Pair 10BaseT.
Rosnimannya for Vitoi bet
Up to twist-and-loop welts, 10BaseT, 100BaseTX, 100BaseT4, and also even not hardened to the 1000BaseT standard can be used.
In the cut-out cards of computers, in the hubs and in the walls, sockets (jack) are flashed, at which plugs (plug) are inserted.
Rosnimannya for Vitoi bet
Eight-pin modular z'єdnuvach (Plug)
People's name "RJ-45"
1 - contacts 8 pcs. 2 - fixator rose 3 - dart fixer | |
Viglyad contacts Contact 1 Contact 8 | |
Side view of the cable | |
Front view On new non-corrosive wheels, the contacts go beyond the boundaries of the case. | |
In the process of obturating the stench, it will be drowned in the middle of the body, pierce the insulating (2) dart and penetrate into the vein (1). |
Fork with insert
Retail for 10Base-T
Eight-contact modular z'єdnuvach.
Jack and outlet
Socket є socket (rose) z'єnuvacha with attachments for fastening the cable and housing for easy installation. Until then, the plug will also turn on. Sockets, yak and cable, are of different categories. On the case of the socket, it is written what category of the won. When prompting a 10Base-2 hedge, it is necessary to use sockets of category 3 (Cat.3) or more beautifully 5 (Cat.5). And for 100Base-TX hemlines, you need to use Cat.5. Sockets of the 5th category are also distributed according to the method of installing the cable in the outlet. I have enough great number rishn, which is adapted to be a specific form, and to reach the most suitable ones - "type 110", "type KRONE". Slid means that KRONE is a chain of such form. |
Vzagal, let go of the free type of socket outlets, but for the house it is possible to bring the vicarists to the best prices - calls. Zvychana socket є a small plastic box, before which a screw and a double-sided sticker for mounting on the wall can be supplied. As soon as the wall is okay, it’s easier to use a sticker, but it’s not possible to drill a wall and screw the socket with a screw. On one side of the body, there is a rose seam for turning on the RJ-45 plug; before the speech, there are sockets in the building, two roses and more. | |
You need to take a crumb out of the box and go to the inside of the socket, you need to show the mass of patience and wine. Krishka trims on the inner claws, calls are niyak, which, as a rule, are not meaningful. On my dummy, the virobniks are zamagayut one by one і s koristuvach, like the socket is foldable to open. It is necessary to open the edges, far away from the two possibilities: the edges will appear either in the middle (more or less) or named. On the gaps, which are visible in the middle, it is necessary to press, and when they are displayed, it is called the number of pits. When you buy it, ask for it, and they showed you how the socket can be opened. If you are a novice, see what type of outlet you have, see the attachment of wires that rose. |
For information with a computer, vikoristovuyutsya fancy pictures.
Merezheva PCI card
Merezha card is combined (BNC + RJ45), PCI bus
One hour victorious two roses are unacceptable.
Roz'єm PCI
Also new bus is given by PCI (distribution of white color). Small cards designated for PCI must be inserted into PCI roses.
At the computer
Server setup.
Server
Windows95 Server Functions (Windows98)
Go to the "Control Panel" (Start-> Setup-> Control Panel) | |
Viber "Merezha" | |
At the tab "Configuration", add a button "Dodati". | |
Menu "Vibir to component type" Viber "Service" and print "Dodati". | |
Vibir: Network Service window. Vkazuєmo "Wirobniks" - "Microsoft", and "Merezhevy services" - "Service for access to files and printers from Microsoft". Steal, but on the cob the writing is not visible again, and it is necessary to scroll it to the left, so it will not be merciful. Find "OK". | |
If you want to add access to your computer for http (or www), then again go to the "Vibir: Network Service" window and select "Microsoft", "Special Web-server". Find "OK". | |
Vіkno "Merezha". Perekonayte, the distribution kit is available. Find "OK". | |
Show up at the end, show The process of copying files. | |
I nareshty you to get it Reload the system by pressing "Tak". | |
Pislya re-engaging, see the edge, and vibrate the pictogram (icon) "My computer". | |
At the window, press the mouse button with the right button on that disk, which you want to make available as a font. If you want to browse, not the entire disc is available, but the directory (director), having pressed on the disc with the left button, press the right button on the directory you need. | |
In the menu, select the access item. | |
Show up "Vlastivosti: ..." It means that it is a local resource. | |
Viberit "Home resource", weave im'yam will become the drive letter of the directory. You can see how you look like you, because of the urahuvannya of the deyekh obmezhen, you can impose on the signs that you are victorious. I, as a rule, will play yak є, so don't get lost by yourself. Here it is also possible to change the type of access and interconnect all with passwords. Onslaughtєmo "OK" | |
In a second, your resource will become available as you go. |
ANNIVERSARY OF PRACTICE
practice;
17 worms - Pidbirav literature on the topic of zavdannya, vivchav zabechennya software (Novell Personal Net Ware, Windows for Workgroups.);
VISNOVKI:
Overbought at this enterprise:
Dotrimuvavsya rules of protection and protection technology;
Having defined the rules established for the workers of the enterprise, including the nutrition of the labor order, security, confidentiality regime, prompting for the protection of mine;
Viviv chinni standards, technical umovi, landing gear, provision of the instructions for the operation of VT;
Vivchav the rules of operation and servicing of VTs, pre-slidnitsky installations, scho є at pidrozdilі;
Mastered okremi computer programs, how to get involved in professional spheres (Novell Personal Net Ware, Net Ware Line, Windows for Workgroups);
Having mastered the work with periodic, abstract and pre-informational information from computer science and VT;
Having completed the training, transferred to the practice program.
Don't let the Vikladachev robot be blocked!
Denmark is called from practice, you can easily write a name for your topic.