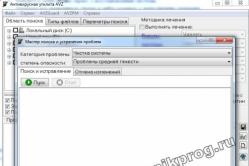
Antipyretic remedies for children are prescribed by a pediatrician. But there are situations of indispensable help for fevers, if the child needs to give faces negligently. Then the fathers take on themselves the resuscitation and stop the antipyretic preparations. What can be given to infants? How can you lower the temperature in older children? What are the most safe faces?
INSTUP
Purposes of practice:
Consolidation of theoretical knowledge, taking into account the development of disciplines: organization of EOM and systems, system software security, data bases, measures of EOM and telecommunications, peripheral office possession;
Familiarity with the manufacturing processes, which include the selection of enumeration techniques and information technologies;
Vyvchennya methods of molding, processing, accumulating and extracting from the production process of information flows;
Nabuttya novice iz zastosuvannya autonomous and complex accounting systems;
Analysis of the reach and shortcomings of the activities of the organization.
Practice topic:
The development of principles to encourage the functioning of local counting measures in a particular organization.
As a place for passing through the production and technological practice, I chose the organization TOV "Snigovik Plus".
Subsidiary structure: Director Masov Evgeniy Mykolayovich. Yogo has 20 specialties: accountant, vaulters, water, technicians,
Sellers.
MAIN PART
Zagalnі principle pobudovi that arhіtektura EOM;
Principles, methods and ways of complexing hardware and software tools in the process of compiling accounting systems, complexing volumes;
Models of methods and forms of organization of the process of development of a software product, technical development;
The main capabilities of data base management systems and their versatility.
Besides, I can learn:
Koristuvatisya technical and advanced literature, sets of standards for the development of a software product, technical development;
Vikoristovuvaty otrimani at the process of learning that knowledge for competent and technically grounded development of a software product, technical development;
Design a software product, technical design;
Expand the program modular structure;
Zastosovuvati methods and techniques for testing and testing a software product, a technical test;
Koristuvatisya with the help of nagodzhennya;
TOV "Snіgovik plus" Implementation of the sale of wholesale products near Ulyanovsk metro station.
I had an internship with a technical supervisor under a professional programmer
Vorlamova N.F. Managing data bases about the delivery of the number of goods that are rebuying in warehouses, looking for additional computers with an operating system Windows 95 or Windows 98 .
In order to save an hour of transferring information from one computer to another Director of a company, you need to improve the local network in your organization. Technіchniy vіddіl otrimіv zavdannya lay merezha to the skin computer of the company. Technіchny vіddіl rozpochav vykonanny zavdannya.
We have recently had a chance to design some kind of network on the site, we would rather build a local network with a central server. Div Addendum 1
The simplest variant of such a network is communication of computers through parallel ports. In this state of mind, there is no need for some kind of additional adjustment. Guilty buti is less than a daily guide. Such a connection between computers is built up in the middle of one of the few rooms. Victory for transferring data from one computer to another. And here you can transfer data without the help of floppy disks. Be it a modern shell of the operating system, it can be programmed to ensure the transfer of data.
In local peer-to-peer networks, computers are connected to the network through special adapters of the network, and the operation of the network is supported by the operating system of the network. An example of such operating systems are: Novell Personal Net Ware, Net Ware Line, Windows for Workgroups.
All computers and their operating systems in local peer-to-peer computer networks may be of the same type. Koristuvach tsієї merezhі can transfer one to one danі, vikoristovuvat sleeping printers, magnetic and optical disks, etc.
The local computer network has one harder computer, which is called a server, and others, less harder - work stations. On the servers vikoristovuetsya special system security yak vіdrіznyaєtsya vіd sistemnym software zabezpechennya roboshtsionnyh stantsіy.
The main parts of the mesh.
For our products, we twisted the cable with a twisted pair or a coaxial cable Twisted Pair 10BaseT.
Retail for twisted bet
Before torsion pairs, 10BaseT, 100BaseTX, 100BaseT4 lines can be seen, as well as even more approved to the 1000BaseT standard.
Sockets (jack) are installed at the edge of computer cards, in hubs and walls, and plugs (plug) are built into them.
Retail for twisted bet
Eight-pin modular plug (Plug)
Popular name "RJ-45"
1 - contacts 8 pcs. 2 - rose fixer 3 - dart retainer | |
View of contacts Contact 1 Contact 8 | |
Cable side view | |
Front view On the new, non-corrosive fork, the contacts go outside the interior of the case. | |
During the process, the stench will be sunk in the middle of the body, cut through the insulation (2) and embedded in the core (1). |
Plug with insert
Retail for 10Base-T
Eight-contact modular zadnuvach.
Nest (jack) and socket (outlet)
Socket - socket (rose) with a socket for fixing the cable and a case for easy installation. The plug is also turned on before it. Sockets, like and cable, are of different categories. On the body of the socket, it is written which category it should be. When using a 10Base-2 network, it is necessary to use sockets of category 3 (Cat.3) or less than 5 (Cat.5). And for 100Base-TX meshes, it is necessary to stop Cat.5. Sockets of the 5th category are also divided according to the method of installing the cable in the socket. Іsnuє enough large number solution, how to encourage them to be a specific company, and to reach out to the infamous - "type 110", "type KRONE". Please note that KRONE is such a company. |
Vzagali, impersonal different types of sockets are produced, but for the house it is possible to win the found ones - the best ones. The secondary socket is in a small plastic box, with a screw and a double-sided sticker for mounting on the wall. If you cover the wall, it’s easier to peel with a sticker, if not, you can drill the wall and screw the socket with a screw. From one side of the body there are roses for the inclusion of the RJ-45 plug; before the speech, there are rosettes at the building, two roses and more. | |
To take the lid out of the box and get inside the socket, you need to show a lot of patience and guilt. The lid is trimmed on the inner straps, the name is not, as a rule, not known. In my opinion, the pickers are swayed one by one and with a coryst, like a folding socket. It is necessary to make two cleats, give two possibilities: the cleats are either in the middle (which is closer) or in the name. It is necessary to press on the buckles, which are in the middle, and which are called, besides the letters. When buying, ask in a cordial way to be shown how the socket opens. After removing the cover, depending on what type of socket you have, you will see the wires attached to that socket. |
For s'ednannya z computer'yuterovuetsya merezhnі maps.
Merezheva PCI card
Merezha card combo (BNC+RJ45), PCI bus
One-hour chanting of two roses is unacceptable.
PCI socket
Another PCI data bus (different white color). Merezhev cards, recognized for PCI, need to be inserted into PCI sockets.
At the computer
Server setup.
Servers
Windows95 Server Functions(Windows98)
View in "Control Panel" (Start->Setup->Control Panel) | |
Select "Merezha" | |
At the "Configuration" tab, press the button "Add". | |
Menu "Select component type" Select "Service" and press "Add". | |
Exhibition "Vibir: Network Service". Indicatively, "Wizards" - "Microsoft", and "Merezhevі services" - "Service for access to files and printers in Microsoft". Wrath, what is written on the cob is not visible for the most part and it is necessary to scroll it to the left, so as not to have mercy. Press "OK". | |
If you want to add access to your computer for http (or www), then again go to the "Choose: Network Service" window and enter "Microsoft", "Web Server Features". Press "OK". | |
Vikno "Merezha". Perekonaytes, scho the distribution kit is available. Press "OK". | |
Show up at the end, what will you show The process of copying files. | |
I dare to preach to you Restart the system by pressing "Yes". | |
After re-advancement, see the merezh, and select the pictogram (icon) "My computer". | |
At the end, right-click on the mouse on that disk, which you want to make available as soon as possible. If you want to make available not the entire disk, but some directory (directory), having pressed the left button on the left button on the disk, right-click on the catalog you need. | |
From the menu, select the access item. | |
Appear at the window "Authority: ..." In yakomu it is assigned which local resource. | |
Choose "Great resource", merezhim im'yam Change the drive letter chi to the name of the directory. You can change it as it suits you, for the improvement of such borders, which are superimposed on the signs, which are victorious. I, as a rule, deprive yak є, so that I myself don’t stray. Here you can also change the type of access and surround all with passwords. Press "OK" | |
In a second, your resource will become available as soon as possible. |
PRACTICE CAP
practices;
17th week - Reading literature on the topic of work, learning software security (Novell Personal Net Ware, Windows for Workgroups.);
VISNOVSKI:
Perebuvayuchi on this undertaking:
Dorimuvavsya rules for the protection of practice and safety technology;
Vikonuvav rules established for business practices, including food for labor order, fire safety, confidentiality regime, vidpovidalnist for saving lane;
Vivchiv chinnі standards, tekhnіchnі umovi, posadovі obov'yazki, regulations and instructions for the operation of VT;
Vyvchav rules of operation and maintenance of the equipment of VT, doslidnitsky installations, which are in the pipeline;
Having mastered the field of computer programs, like in the professional sphere (Novell Personal Net Ware, Net Ware Line, Windows for Workgroups);
Having mastered the work with periodical, abstract and advanced information knowledge in informatics and computer science;
Vykonuvav zavdannya, transferring the program of practice.
Don't give in to the vikladach's robot!
Denmark calls from practice, you can easily write a call for your topic.

Department ____________________________________________________________
the name of the department, how to ensure the practice
I CONFIRM:
Head department ___________________________
"_____" _______________________ 20__ p.
REQUEST
Behind the practice
to the student(s) of the group ______ ____________________________________
P.v.o. student(s)
Specialty (direct)
Practice lines from _____20__ by _______ 20___
____________________________________________________________________
advanced formula
Calendar plan
| Name of the head (entering), what to establish the head of | Date of appointment date (come in) | Signature of the practice letter of the organization |
| 1 | 2 | 3 |
| Theoretical part | ||
| Practical part | ||
| Zakhist zvitu z practices |
Book of practice at the university
_________________ ___________________
signature P.I.B., settlement
Consumables at the corporate level 4
1.1 Significance of information, information technology 4
1.2 Opacity for the presence of LOM 4
1.3 Tasks that are violated in the presence of LOM 5
Description of the corporate organization 6
1.4 Topology of mesh 6
1.5 Line model 7
1.6 Protocol 9
Hardware and software 10
1.7 Server hardware and working computers 10
1.8 Merezhev region 12
1.9 Cable system 13
1.10 Software 14
1.11 Safeguarding the protection of information 17
Visnovok 18
List of vikoristani dzherel 19
Entry
Today, computerization at work is a rare sight. The presence of some computers in the office with a great flow of information and an obligation to work with documents improves the process of working with spivrobitnikov, creating ineptitude. The success of the activity is practical, whether it be a business enterprise, organization of povyazaniya chi lie down in the presence and consistency of the informatization system. Such systems are local accounting systems, which are now often called corporate measures.The creation of a corporate framework allows:
– to organize a high-level exchange of tribute among practitioners;
– speedy paper documenting of the middle organization;
- Increase the productivity of work;
- Change the hour for processing information.
They cease to be the necessary information for the exchange of data, there is no need to write on paper documents, with which it is necessary to recognize the sprat of coristuvachiv.
Merezha can have a merger printer, modem, scanner, merger server installed as an addendum server.
In addition, such fences are of a closed type, access to them is allowed only for a small stake of coristuvachiv, which stuns the defender of information. All these possibilities cannot be implemented for the help of only operating systems (OS) and application programs. That's why the majority of current enterprises are victorious.
^
Consumables from corporate companies
1.1 Significance of information, information technology
The editorial office of the newspaper "Robota u mistі" is engaged in the preparation (writing of materials, reception of voiceovers, design of advertising, layout) of the newspaper to the other hand. Tobto the activity of the organization is connected with the victories and generations of the great obligation of information. The least damage with її zberіgannі ta obrobtsі zagalom. Information is its own subject of practice, and even the organization of the process of managing information resources allows business to effectively conduct its activities and virishuvati set tasks at a lower level of risk. Using a local computer file allows you to save paper documents, increasing the productivity of work, shortening the hour for processing information.
From a variety of measures, the personalization of the calculation, the organization of automated work areas, which allow you to effectively complete the work of the day.
^
1.2 Non-transparency for the presence of scrap
The presence of the fence made the work of the spivrobitniks more difficult, called out to the unhandedness, caused the vitrati:
– transferring information from one computer to another computer, taking an hour to help you remember it;
- Access to the global network only from the computer that the modem can;
– Peripheral attachments (printers) possessed in a complete computer system (for using such an attachment, a portable memory, a computer, which is connected to an attachment, must be called for a day);
- Vitrati at the pribannya other outbuildings for skin computer (hard disk, printer, CD-ROM, modem) and expensive software.
^
1.3 Tasks that are violated by the presence of scrap
LAN ---– a set of hardware devices and algorithms that secure the installation of computers and peripherals small vіdstanі(one business, office) and allow you to quickly exchange money, fully win information resources, peripheral outbuildings.
Mozhlivostі, scho nadayutsya koristuvachami SCRAP:
- saving and archiving your work on the server, so as not to waste valuable space on the hard drive of the PC;
- Easy access to add-ons on the server;
- Splna work with documents;
- simplification of document processing (the ability to look over, correct and comment on documents without depriving the workforce, not organizing the gathering of people that take a lot of time);
- Relief sleeping victoria in organizations of expensive resources, such as printers, storage CD-ROMs, hard disks and programs (for example, text processors or database software).
^
Description of the corporate organization
1.4 Merezha topology
The topology of the enumeration measure is a way to connect four components (computers, servers, printers, etc.).
The LAN of the editorial office was inspired by the “star” topology based on the server: all computers behind the auxiliary segment are connected to the central component by a cable, information between the clients of the network is transmitted through a single central hub, as the central hub acts as a server. With this, two printers, installed in the office, are also connected to the server by the same ones.

Scheme of local editions (topology type "zirka")
"Zirka" vinyl at the dawn of computational technology, if the computers were connected to the central, head computer. The advantages of this topology are similar to those of the offensive:
- High swidkodiya merezhі, so zagalna proizvodstvennіst merezhі lie only in the productivity of the central university - the server;
- Internal client charges do not affect the speed of the server processor;
- Є єdina person, yak vіdpovіdaє for the administration of resources in the area;
– secure the possibility of fencing and access control to fencing resources;
– the duration of the data closure that is being transmitted, the data fragments between the working station and the server are transmitted over an open channel, without interfering with other computers.
Insufficiencies of the "star" topology:
– the superiority of the chains is determined by the superiority of the central node, if the central computer is out of tune, then the robot of all the ropes should be pinned down;
- Vytrati for laying high cables, especially if the central high school is geographically spread far from the center of the topology; with expanded counting lines, they cannot be broken earlier than cable ties: before a new working place, it is necessary to lay a cable from the center of the line.
The main criterion for choosing a given topology was the situation, which should have only one computer (a cable connecting it to the server), which computer could not transmit and receive data from the network, and other computers in the network tse vplin.
^
1.5Merge model
Type of analyzed LOM - client-server type, є one host computer - server. Nine computers and two printers are connected to the server. Main server tasks:
- Conservation of working data of coristuvachiv;
- Saving databases of accounting records, archives, etc.;
– saving of service data bases and programs;
- Keeping home folders of coristuvachs.
The design server in such a way as to give access to anonymous files and printers, ensuring that productivity and security are high at all times. Administration and management of access to data is centralized. Centralized allocation of resources to facilitate their search and support.

Scheme of the model of the "client-server" type
Advantages of this model:
- High shvidkodiya merezhі;
- Presentation of a single information base;
- Presentation of a unified security system.
Bo all important information it is distributed centrally, so it is stored on one server, it does not matter to ensure regular backup copies. Therefore, in the case of the time of the main area of data collection, the information will not be wasted - it is easy to speed up a duplicated copy.
Є ієї modelі і nedolіki. The main one is that the variability of the creation and maintenance of the client-server type is significant, for the account of the need to buy a special server.
Virishalnym argument pіd h vyboru merezhі s urakhuvannyam server becoming a high rіven zahistu danih. In such meshes, one administrator can deal with security problems: to form a security policy and zastosovuє її shkodo koristuvacha merezhі.
1.6 Protocol
Protocol - a set of rules and technical procedures that regulate the communication between computers at the border.The process of transferring data through the mesh is divided into sprats. At the same time, the blackness of vikonannya tsikh krokiv is clearly marked. To the heads of protocols for the appointment of such terms and control over their victories. The editorial team has won the Transmission Control Protocol/Internet Protocol – TCP/IP.
TCP / IP - pronouncements standard dial protocols, yakі zbezpechuyut zv'yazok y inhomogeneous medium, scho zbezpečuyut summіsnіst mіzh computers of different types. Sumіsnіst is the head of TСР/IP, more LOM supports yoga. Also, TCP/IP provides access to Internet resources, as well as the protocol that is routed for enterprise scale. Oskіlki TСР/IP support routing, vin sound like an inter-merge protocol.
TCR/IP has two main shortcomings: obligatory and insufficient security of work. Ale for merezhі editorial staff come.
^
Hardware and software security
1.7Hardware security of the server and working computers
There are two parameters that make the server look like the best computers. The first one is the most highly productive (the cost of effective exchange with peripheral attachments), to exhaust the hard disk drive system (importantly SCSI interface); the other one is promoted superiority (the server, as a rule, works as a whole).
Server productivity is often measured in transactions. Under the transaction, the sequence of three subsequent events is considered: reading of data, processing of data, and recording of data. Zastosovno, for example, before the file server, the transaction can enter the process of changing the record on the server, if the working station checks the modification of the file that is saved on the server.
Of great interest is the maximum amount of operational memory, which can be won on a given server, the possibility of installing more hard processor as well as another processor (as it is planned to change the operating system, which supports a dual-processor configuration).
It is also important to keep information about those, such as the configuration of the disk subsystem can be tested on this server, in the first line, which is the total number of disks, the maximum number of them.
An important role is played by the feasibility of expanding the system and the simplicity of modernization, the shards themselves allow you to secure the necessary productivity not only for the current hour, but also for the future. The situation at the robot server is important - it’s yakіsne that uninterrupted eating.
In our case, the implementation server is on a sizable standard computer, which can be configured with good characteristics.
To secure the request server, the processor is an INTEL processor based on Core 2 Duo dual-core technologies, which has high productivity, reliability of work, good energy savings and temperature indicators.
For hardware security of working stations, the advantage was given to AMD processors from the average productivity values and at a low price.
The server motherboard is ABIT P-35 on socket 775. It is optimal for the price-performance indicator, it has a good throughput building, a dual-channel architecture for operational memory, it is secured with a built-in merging card with a bandwidth of up to 1Gb / sec. Qia fee support a lot of modern processors like INTEL, which allow, if necessary, to increase the productivity of the system by replacing the processor. There are more slots for expanding the system.

Server Motherboard - ABIT IP-35
RAM for the server is implemented on two sets of OCZ Gold Series (4 strips 512 MB).
Vibirayuchi pristroї, scho to remember, attach special respect to yogo trust, tse especially worth the possession of the server. When designing the measure, the editors lied about the fact that the organization of the great data base is being transferred, they victoriously beat the RAID-array equal to RAID-5. Blocks of data and control sums in this array are cyclically recorded on all disks. The most popular of the peers, we are ahead of the hearts of our economy.
Additional resources are used to write information on a RAID 5 volume, which requires additional calculations, but when reading (equivalent to a hard drive) it wins, to which the data streams from the accumulated array are parallelized. The minimum number of disks that are victorious is three, so for the organization of the RAID three disks were selected from the original Segate disk drive, with a capacity of 150 Gb of leather.
For the working stations, the smallest hard drives were selected, from those available at the store - 80.0 Gb from the Hitachi company. Denmark obsyag enough for the installation of various professional programs and office programs. And the expansion of the cache memory of 8 MB will allow you to organize the robot without hiccups.
^
1.8 Merezhev possession
LOM editorial office has additional equipment installed: two printers and a modem.
Merezhevy printer will allow the need to purchase a large number of attachments to all spivrobitnik, as they require. Under the hour of the creation of the merezhі, the color laser was collected samsung printers CLP-300 A4.
The modem is connected to the LOM server. Vibrated Modem D-Link DSL-2540U.
The most important component of the computer network is the image map. Merezhevі maps act as a physical interface for communication with a computer that mesh cable. Main features of a lace card:
- Preparation of data, which should be taken from the computer, prior to transmission through the cable;
- Transferring data to another computer;
- traversing the flow of data between a computer and a cable system.
^
1.9 Cable system
Cable linesє folding design. The cable is made up of conductors, which have ball insulation: electrical, electromagnetic, mechanical. In addition, the cable can be equipped with roses, which allow you to quickly change the connection to a new different possession. At the looked out computer network, it is not necessary to lay the basis of a connection from a PC to a server at a distance of more than 100 meters, which is why the cable is twisted with a pair of UTP category 5e, which increases the speed of transmission of 100 Mb/s.

twisted pair cable
The cable "Vita Pair" is made up of pairs of wires, twisted side by side, one of one and one hour twisted over several other pairs, between one sheath. The leather pair is made up of a thread called the Ring and the Tip wire. Leather pair in obolontsi maє vlasny number. Curling the wires allows you to avoid electrical crossovers. The cable of screened torsion pari may have a mid-braid, so as to protect the additional protection of the wire. The maximum length of non-screened bet twists is 100 m.
Benefits of twisted bet:
- High productivity of data transmission speed;
- low varity;
- Easy installation;
- High shybleness;
- Expansion of the area allows to be included in the minimum effective length of the cable.
For connection of twisted bets to computers with RJ-45 connectors.
^
1.10 Software security
Today, the server versions of the Windows operating system are widely released, mainly the problems of the administration and the low quality of the volodinnya. The Windows Server 2003 family is looking ahead to the current warehouse of the Microsoft .NET Framework. Windows Server 2003 is available in several editions. The editors have written Windows Server 2003 Standard Edition. It is an inseparable operating system for the server part of the business solution, and it is insured for stagnation at small companies and subsidiaries. Here we have provided a shared resource and a centralized expansion of the add-ons for desktop computers, as well as implemented support for up to 4 GB of RAM and a symmetrical rich processor processing with a choice of two processors.
Robotic stations - all computers, like vikoristovuyut merezhevі resources, but do not use powerful resources with powerful forces. Such computers work under the supervision of the operating system. For the working stations of the edition, the operating system was installed Microsoft system Windows XP Pro. Tsya system can have a wider range of possibilities for customization, administration and work in local areas, lower Windows XP Home Edition. Windows XP Professional may have a lot of advantages:
- Stability. Peredumovoy nadіynostі system and those scho programs pratsyyut in the wet expanses of memory. Tse protect their types of conflicts and problems that blame the link with them;
- Mindfulness. Working with programs that were not specifically designed for the Windows XP Professional environment;
- system update . If the computer fails for an hour, go to Safe Mode (Bezpechny mode), the operating system will propagate the ability to name System Restore (System Restore). Tse allow koristuvachevi to turn to quiet settings, as if they were on the computer before the incident. So the name of the point of renewal (restore points) can be created at any hour. In addition, the operating system periodically creates hot spots during the skin installation of a new program. When the computer returns to the point of renewal of the operating system, the vicorist data is set to the hour when the system worked normally.
As an office software package OpenOffice.org, which can be used with extensions to do expensive Microsoft Office. Tsya to do the hard program may have a number of other brown authorities, and it is absolutely costless, both for the home and for the commercial victoria. This is a universal office software package that can be applied to all major operating systems.
The OpenOffice.org package includes six software add-ons. The Writer text editor has a friendly interface similar to that of the Word editor. To that, be a kind of koristuvach, knowing Word, it is easy to get used to Writer. The same can be said about the spreadsheet editor Calc, which is rich in what Excel thinks. There is also a program for creating and demonstrating presentations Impress, a vector editor Draw, a database management tool Base and an editor for creating and editing Math formulas. Nedolik OpenOffice.org - work swidkist: zavantazhuetsya that pratsyuє vіn deshcho appropriately, but generally pleasant.
The organization of safe robots of LOM is not possible without the installation of anti-virus software. Therefore, as an anti-virus protection for installations, Kaspersky Anti-Virus 7.0 is a really cheap system.
Anti-Virus of Kaspersky Volodymyr three steps to protect against new Internet threats: re-verification by signature databases, heuristic analyzer and behavioral blocker.
Defending Kaspersky Anti-Virus as a complex virus and includes:
- Defender of electronic mail. Kaspersky Anti-Virus allows anti-virus scanning of mail traffic based on the data transfer protocol (POP3, IMAP and NNTP for incoming support and SMTP for outgoing) independently from mail programs that are victorious;
- Checking the Internet traffic. Kaspersky Anti-Virus ensures anti-virus scanning of Internet traffic that follows the HTTP protocol, in real time and independent of the browser. Tse allows you to save the infection before saving the files on the hard disk of the computer;
- Scanning file system. Perevіrtsі can be pіddanі be-yakі okremi files, directories and disks. In addition, you can run a recheck of only critical areas of the operating system and objects that are zavantazhuyutsya under an hour to start Windows.
Kaspersky Anti-Virus protects your computer against Trojans of all types keyboard pushers, zapobіgayuchi transfers of confidential data to malefactors.
^
1.11 Safeguarding the protection of information
Looking at the problem of zahistu data from the merezhі, we see all the possible failures and damage, which can lead to the aggravation of the unimportant modification of the data.
Among such potential "threats" can be seen:
- Problems of possession: problems of the cable system; power outages; failure of disk systems; failure of data archiving systems; zboї robotic servers, work stations, merging cards, etc.;
- Spend information through an incorrect robot PZ: spending or changing data when pardoning PZ; spend when the system is infected computer viruses;
- Spend, due to unauthorized access: unauthorized copying, loss or disclosure of information; awareness of confidential information, as to become a mystery, third-party errors;
- Pardons of koristuvachiv: vipadkove iznischennya or change of data; incorrect software and hardware security, which leads to the destruction of data.
For zabezpechennya nadіynostі zberіgannya danih that zapobіgannya vtratі Informácie in rezultatі zboїv in energozabezpechennі in redaktsії vstanovleno dzherelo bezperebіynogo zhivlennya (UPS) Ippon Back Office 600. Yogo nayavnіst dozvolyaє in razі zniknennya naprugi in elektromerezhі prinaymnі korektno completed the robot system is the operatsіynoї vimknuti server.
To defend against viruses antivirus program Kaspersky Antivirus.
Visnovok
The result of the internship was:- Detailed knowledge of the local dimension of the organization;
– acquisition of new knowledge about the work and maintenance of the scrap;
- vivchenі programs, like the organization.
Following the development of a measure and analysis of the work of the editorial office, it was requested to create a new work place - staff system administrator. Scattered at the same time, the problems of the robots, which they blame today, the computers themselves, do not reveal all the necessary knowledge and rely on their direct obov'yazkiv.
^
List of vicorists dzherel
Akulov O. A. Informatics: basic course [Text] - M .: Omega-L, 2004. - 552 p.
Olifer V. G., Olifer N. A. Computer measures [Text]: a handbook for universities. - St. Petersburg, 2007, 960 p.
P'yatibratov O.P., Gudino L.P., Kirichenko O.A. ed. A. P. P'yatibratova. M.: Financial statistics, 2001. - 512 p.
Federal Agency for Education of the Russian Federation
"Peter's College"
from the discipline "Computer networks and telecommunications"
Topic: "Designing the initial local enumeration measure"
Vikonav: Kurilovich N.G.
Revised: Markelov Yu.P.
St. Petersburg 2010
Entry
Stage 1. Infological information about the automation object
Stage 2. Design stage
Stage 3
Visnovok
Entry
Our hour is characterized by a booming development of telecommunication technologies.
The association of computers at the merezhі allowed to significantly increase the productivity of work. Computers vikoristovuyutsya as for general (or office) needs, so navchannya.
Local border - a group of connected computers, servers, printers, roztashovanih at the borders of budivl, office and room. Local networking gives you the ability to get full access to shared folders, files, possessions, and other programs as well.
The use of local resources gives the opportunity to reduce the financial costs of business, improve the security of saving important data, speed up the timing of the interviews for the achievement of a different kind of manager, as well as improve the efficiency of robotics.
Computers can connect with each other, with different access mediums: copper conductors (twisted pair), optical conductors (optical cables) and through a radio channel (droneless technology). Dart calls are installed via Ethernet, wireless - via Wi-Fi, Bluetooth, GPRS and others. A local numbering network can also be a gateway to other local networks, as well as a part of a global numbering network (for example, the Internet) or a connection to it.
LAN (Local Area Network) - local fencing, recognized for the unification of territorially grouped fencing outbuildings. All devices in the middle of the LAN store information about the MAC addresses of the neighboring network adapters and exchange data on another (channel) peer seven-layer OSI model.
Main advantages of LAN:
1. Reduced cost per yard
a. The association of working positions of employees of the functional groups, among some of the impossibly unauthorized exchanges of data on the channel level.
b. Razmezhuvannya access to servers and printers.
c. Separation of access to the Internet
d. Mutual isolation of the segments in the meshes that vicorize different meshing protocols (for example: IPX virtual meshing, Apple virtual meshing)
3. Reduced operating costs
a. Low variance of relocation
b. Change in the number of non-standard ports of switches
4. Promotion of reliability and strength of measure
a. Isolation of broadcast storms
b. Accelerated localization of faults
c. Greater control over traffic
d. Effectively recover ip address
LAN shortcomings:
1. Cob vitrates
2. The need for additional training for staff.
Stage 1. "Infological information about the automation object"
Tsіlі i zadannya
The main task of the course project is the design and development of a peer-to-peer primary LOM on topology "Zirka" and "Zahalna bus" OIPTS Petrovsky College.
Computers will be tested by students with a method of learning, carrying out practical activities. The merezha is responsible for ensuring the uninterrupted functioning and the interplay of various distributions of supplements that are found in these merezhas.
List of primary disciplines
Table 1. List of primary disciplines and PZ required for them
The skin working station will be equipped with 32-bit Window 7 HomeBasicDVD (RUSDVD) operating system. This choice is explained by the fact that before the warehouse of Windows 7, the deacons of the distribution, turned off Windows Vista, so the innovations in the interface and in the programs and there are more possibilities, similar to the previous versions of Windows and more optimized.
Variety of one licensed OS MS Windows 7 Home Basic 32-bit Rus 1pk OEI DVD one PC (working station) to become 3799 r. Also, for 34 working stations, the total cost is 129166 UAH.
Software security of workstations
For the operating system, it is necessary to install the main package of application programs and utilities on the working stations, which is used to support the LOM.
1. MS Office 2007 Professional Win32 Rus AE CD BOX (for starters)
Table 3. System support before MSOfficeProfessional
2. KOMPAS-3DV12
Table 4. System support for KOMPAS-3DV12
3. Acronis Disk Director 11 Home
Table 5. Acronis Disk Director 11 Home System Help
Typical configuration of the working station
Table 7
| Accessories | Product description | Vartist |
| Frame | InwinEMR-006, microATX, Minitower, 450W, Black/Silver | 2290 people |
| Motherboard | Gigabyte GA-H55M-S2H, iH55, Socket 1156, 2xDDR3 2200MHz, 2 x PCI Express x16 + Integrated Intel HD Graphics, 6 x SATA II, LAN 1 Gbit, microATX | 3290r. |
| Processor | Intel Core i3 530 2.93GHz, 2x256 kb, 4 Mb, LGA1156 BOX | 4390r. |
| Working memory | Kingston HyperX (KVR1333D3N9K2/2G) Kit of 2, DDR3 2048Mb (2x1024), 1333MHz | 1590 r. |
| hard drive | Western Digital WD5000KS/AAKS, 3.5", 500Mb, SATA-II, 7200 pro/hv, Cache16Mb | 1840 p. |
| Video card | Wake up video adapter | 0 out. |
| optical drive | Asus DRW-24B3ST, DVD RW, SATA, Black | 1090 people |
| LAN | 1Gbit merged adapter | 0 out. |
| Monitor | Samsung EX1920, 18.5" / 1366 x 768 pix / 16:9, 1000:1, DC - 5000000:1 / 250 cd/m² / 5 ms, D-Sub / DVI, TFT Black | 5990 people |
| Merezhevy filter | Vector Lite, 1.8 m | 399 r. |
| Additions of introduction | Logitech Desktop MK120 Black, keyboard + mouse set | 680 people |
| TOGETHER: | 21560 nar. |
Together, the number of one working station was 21,560 rubles. Designed merezha warehousing of 34 working stations, in stock 733,000 rubles.
The typical configuration was selected from the selected information for the site of the store Kom'yuter-tsentr KEY. (http://www.key.ru/)
Visnovok at the first stage
After completing the work on the first stage of the course project with computer and telecommunications, I have compiled a list of all the software installed on the working stations. It was stocked with a typical configuration of the working station with improvements system wimogs, applied and system software, moreover, the necessary memory on the hard disk is calculated by the method of adding the memory required for the software. Operative memory and the processor are used to improve the system's capabilities and add-ons with a margin of 30%.
Stage 2. Design stage
Tsіlі i zadannya
The method of another stage of the course project is the development of the specifications of the communication system, the variance of the work carried out and the plans of the working premises, which are combined into a scrap, from the designation of the distribution of PCs and cable lines in them.
Before the skin application, it is necessary to lay down the specifics of the communicative possession, after which it is necessary to lay down the main plan for the use of LOM and the specifics of the entire possession.
Select cable system
The choice of the cable system to lie down in the intensity of the merging traffic, could protect the information, maximize the distance, could up to the characteristics of the cable, the cost of implementation.
Wita pair (twistedpair) - a type of cable connection, is one or a couple of pairs of insulated conductors twisted together and covered with a plastic sheath. The twisting itself allows you to avoid certain types of overshoots that are aimed at the cables. Ring for Ethernet 10Base - T using a cable that can make two bets. One for transmission and one for reception (AWG 24).
Thin coaxial cable (RG-58 or "Thin Ethernet") - an electric cable that is folded from the central conductor and screen, which is loosely packed, and serve to transmit high-frequency signals. Hvilyovy opir 50 Ohm, diameter 0.25 inches, maximum length of the cable segment 185 meters. Rule 5.4.3 is enforced. 10BASE2 standard . The coaxial cable is more zavadostiyky, the signal is extinguished at a much lower rate at the twists of the pair.
Passive warehousing of SCRAP includes:
1) The cable itself
2) RJ-45 wall sockets
3) Patch panels
4) Repeaters
5) Patch cords (subscriber cords) with RJ-45 sockets (cable for connecting wall sockets with roses on the computer's wired adapter).
The laying of cable systems at the working premises is based on the folded plan of the premises with the improvement of the specifications on the glass materials and the components of the given premises.
When designing cable systems, it is necessary to insure the characteristics of the interfacing of different cable systems:
1) The maximum length of the cable segment is up to the 1st type
2) I'll pass through cable
3) Availability of the installation, which ensures the interoperability of Space with other cable systems
After analyzing the characteristics of different types of cable, physical expansion of computers, we chose a 10Base-T twisted pair cable and a thin coax cable.
Choice of topology
Merezhev topology- a way to describe the configuration of the truss, the scheme of roztashuvannya and the installation of the truss outbuildings.
Іsnuє kіlka options for topologies for designing and pobudovi merezhі. Below is a description of some of them.
Bus topology
The topology of the cable bus is connected to a single cable, which is connected to all the computers in the network. Awareness that is being superseded by the working station is expanding to all computers in the area. The skin machine is reverified - to whom the message is addressed and how it is processed. There are special entrances to get used to, so that for an hour, the computers do not override one to one to transmit and receive data.
With such a connection, computers can transmit information only via a call, since there is only one line of communication. In another way, the information will be transmitted after the invoice (conflict, collision).
Fig.1 Topology
Tires are not terrible for other computers; In addition, the shards of vikoristovuetsya less than one cable, at the time of the shave, the work of the network is destroyed. You can get it, that the tires are not terrible and having cut the cable, the shards in this way are overwhelmed by two practical tires. However, due to the peculiarities of the expansion of electrical signals along long lines, it is necessary to transfer the connection on the ends of the tires of special attachments - Terminators.
When prompted great meshes vinikaє the problem of subcontracting on a double link between hubs, in such a size it is divided into segments, as they are connected with different outbuildings - repeaters, concentrators and hubs. For example, Ethernet technology allows you to twist the winding cable of more than 185 meters.
Fig. 2 Topology of a busbar with repeaters
Advantages:
1) A small hour of installation of measures;
2) Cheapness (requires less cable and framing outbuildings);
3) Ease of fitting;
4) Departure from the fret of the working station is not allowed on the robotic lines.
Noodles:
1) If there are any problems in the mesh, like shaving the cable, if the terminator is out of tune, the work of all the meshes will be destroyed;
2) Foldable localization of faults;
3) With the addition of new working stations, the productivity of the mine is decreasing.
Topology of the star
Zirka is a topology with a clearly visible center, to which other subscribers are connected. The entire exchange of information is carried out exclusively through the central computer, which in such a rank is already a great vanity, and nothing else, for example, can not deal with it.
As a rule, the central computer itself is the most powerful, and all exchange control functions rely on it. Everyday conflicts in the “mirror” topology of the principle are impossible, the shards of management are mostly centralized.
Departure from the fret of the peripheral computer does not interfere in any way with the functioning of the part of the fence, then, if the central computer's computer, to break the fence, it's not practical. Therefore, the next step is to get used to special approaches to improve the reliability of the central computer and yogo mesh equipment. Shaving any cable or short chirp For some, with the "star" topology, it destroys the exchange with only one computer, other computers can normally continue the robot.
Fig.4 Zirka topology
There are only two subscribers on the skin line of the connection: the central one and one of the peripheral ones. Most often for today's business there are two lines of communication, the skin of which transmits information only in one straight line. In this order, on the skin line, there is only one receiver and one transmitter. All the same, I’ll simplify the borders of possession in a pair of tires, and it will allow for the need for stasis of additional callable terminators. The problem of extinguishing signals in the line of communication is also different in the “zirtsі” is simpler, lower in the “tire”, even if the skin receives the signal of one line.
Behind the bags of topology "zirka" it is possible to develop different topologies, even if you want to expand them. For example, it is possible to add a concentrator with a singing quantity of ports to the concentrator, which is already obvious in the measure, and by the same token, add new coristuvachs to the measure.
This topology will be on the "vita pair" cable system, if you want to have a concentrator with an additional port for connecting to an additional coaxial cable, you can use the cable. For example, you can come to sleeping yard more work stations from topology, for example "bus". In this manner, with the help of topology, it is possible to work out practically whether or not the topology is changed.
Advantages:
1) out of the fret of one working station is not seen on the robots of all the lines;
2) good scalability of the measure;
3) a slight search for faults and shaves at the edge;
4) high productivity of the merezhі (for the mind of the correct design);
5) gnuchki ability of administration.
Noodles:
1) the departure from the fret of the central concentrator will turn into an unproductive measure (or a segment of the measure) with a zahal;
2) for laying a line, it is often necessary to use more cable, lower for more other topologies;
3) the last number of working stations at the merezha (or segments of the merezha) is surrounded by a number of ports at the central concentrator.
On the basis of all the information provided about the topology of the line, its advantages and shortcomings, and also depending on the characteristics of the line of the line, we choose the topology "zirka-tire".
The obstezhennia of the opposite destination.
All the objects (offices 30, 36 and 39) are on the third level and are recognized for carrying out practical work for students on a PC. In our offices, we carry out informational obstezhennya, fold schemes, analyze the necessary amount of possession and yogo variety.
Below is the plan of the first object of the merezhі, office No. 30. There are 15 working stations in my warehouse.
Scheme 1. Plan for office No. 30
Clever meaning:
Table 8
| № | name | Alone in the world | Kіlkіst | Price, rub.) | Varity (rub.) | Note |
| I Glassware materials | ||||||
| 1 | meter | 44 | 140 | 6167 | 3m on the pidom along the wall, | |
| 2 | Coaxial cable RG-58 C/U, coil 100m | meter | 43 | 14 | 619 | 3m on the pidom along the wall, |
| II Accessories | ||||||
| 1 | bracket 19"" 3U | Things | 1 | 638 | 638 | |
| 2 | concentrator 16xRJ-45, 1xBNC, 19" | things | 1 | 2613 | 2613 | |
| 3 | BNC connector RG-58(P) crimp | things | 31 | 16 | 496 | |
| 4 | BNC connector RG-58( M) obtisk | Things | 1 | 25 | 25 | |
| 5 | BNCT connector (M-M-M) | Things | 15 | 67 | 1008 | |
| 6 | Cable BNC(P) - BNC(P) 1.5 m | Things | 15 | 84 | 1272 | |
| 7 | BNC terminator 50 Ohm | things | 1 | 32 | 32 | |
| III Mounting | ||||||
| 1 | Meter | 35 | 58 | 2030 | ||
| 2 | Putting the cable in a box | Meter | 34 | 14 | 493 | |
| 3 | Obtisk RG-58 BNC-connector | things | 32 | 43 | 1392 | |
| 4 | Installation of a socket (BNCT-connector) at the box. | Things | 15 | 87 | 1305 | |
| 5 | Things | 1 | 725 | 725 | ||
| 6 | Installation of the Concentrator at the rack | Things | 1 | 435 | 435 | |
| 7 | Scrap testing | Porty | 15 | 40 | 600 | |
| IV Zagalna vartyst | ||||||
| TOGETHER: | 19851 |
Another project area (office No. 36) includes 16 working stations. Below is a yogo plan.
Scheme 2. Plan for office No. 36
Clever meaning:
Table 9
| № | name | Alone in the world | Kіlkіst | Price, rub.) | Varity (rub.) | Note |
| I Glassware materials | ||||||
| 1 | meter | 262 | 9 | 2599 | 3m on the pidom along the wall, | |
| 2 | Box 40x20mm straight, white | meter | 43 | 140 | 6026 | 3m on the pidom along the wall, |
| II Accessories | ||||||
| 1 | bracket 19"" 3U | Things | 1 | 638,08 | 638,08 | |
| 2 | Things | 1 | 768 | 768 | ||
| 3 | Things | 1 | 4832 | 4832 | ||
| 5 | Things | 16 | 57 | 921 | ||
| 6 | Things | 32 | 25 | 819 | ||
| III Mounting | ||||||
| 1 | installation of the box on the wall up to 50 mm | Meter | 35 | 58 | 2030 | |
| 2 | Putting the cable in a box | Meter | 209 | 14 | 3030 | |
| 3 | Mounting an RJ-45 socket in a box | Things | 16 | 87 | 1392 | |
| 4 | Mounting Bracket 19"" on the wall | Things | 1 | 725 | 725 | |
| 5 | Installation of the switch at the rack | Things | 1 | 435 | 435 | |
| 6 | Installation of a patch panel in a box | Things | 1 | 435 | 435 | |
| 7 | Things | 16 | 87 | 1392 | ||
| 8 | Scrap testing | Porty | 16 | 40 | 640 | |
| IV Zagalna vartyst | ||||||
| TOGETHER: | 26684 |
The third object of the design measure (office No. 39) will have 3 working stations. Below you can poserіgati yogo plan.
Scheme 2. Plan for office No. 36
Clever meaning:
Table 10
| № | name | Alone in the world | Kіlkіst | Price, rub.) | Varity (rub.) | Note |
| I Glassware materials | ||||||
| 1 | Cable "Vita pair" 8 pr. 5E cat. (PCnet), bay 305m | meter | 56 | 9 | 555 | 3m on the pidom along the wall, |
| 2 | Box 40x20mm straight, white | meter | 22 | 140 | 3083 | 3m on the pidom along the wall, |
| II Accessories | ||||||
| 1 | bracket 19"" 3U | Things | 1 | 638 | 638, | |
| 2 | Patch panel 19" 16 ports, cat. 5e, universal (PCnet) | Things | 1 | 768 | 768 | |
| 3 | Switch PLANET GSW-1600 16-port 10/100/1000BaseTX 19" | Things | 1 | 4832 | 4832 | |
| 4 | Socket 8P8C (RJ-45) category 5e, universal (PCnet) | Things | 3 | 57 | 172 | |
| 5 | Patch cord cat. 5e 0.5m (blue) | Things | 6 | 25 | 153 | |
| III Mounting | ||||||
| 1 | installation of the box on the wall up to 50 mm | Meter | 17 | 58 | 986 | |
| 2 | Putting the cable in a box | Meter | 45 | 14 | 652 | |
| 3 | Mounting an RJ-45 socket in a box | Things | 3 | 87 | 261 | |
| 4 | Mounting Bracket 19"" on the wall | Things | 1 | 725 | 725 | |
| 5 | Installation of the switch at the rack | Things | 1 | 435 | 435 | |
| 6 | Installation of a patch panel in a box | Things | 1 | 435 | 435 | |
| 7 | Cross-fitting patch panels | Things | 3 | 87 | 261 | |
| 8 | Scrap testing | Porty | 3 | 40 | 120 | |
| IV Zagalna vartyst | ||||||
| TOGETHER: | 14079 |
Scrap project plan
Scheme 4
Clever meaning:
Table 11
| at | name | Alone in the world | Kіlkіst | Price, rub.) | Varity (rub.) | Note |
| I Glassware materials | ||||||
| 1 | Cable "Vita pair" 8 pr. 5E cat. (PCnet), bay 305m | meter | 130 | 9,92 | 1289,60 | 3m on the pidom along the wall |
| 2 | Box 40x20mm straight, white | meter | 85 | 140,16 | 11913,60 | 3m on the pidom along the wall |
| II Accessories | ||||||
| 1 | Switch 5-port wall | Things | 1 | 1285,76 | 1285,76 | |
| 2 | RJ-45 plug for round loop cable | Things | 8 | 2,88 | 23,04 | |
| III Mounting | ||||||
| 1 | Box installation (< 60 мм) на стену из легких материалов высота >2 m | Meter | 68 | 72,50 | 4930,00 | |
| 2 | Cable laying in a box height > 2 m | Meter | 104 | 17,50 | 1820,00 | |
| RJ-45 connector crimp | Things | 8 | 43,50 | 348,00 | ||
| IV Zagalna vartyst | ||||||
| TOGETHER: | 21610 |
Visnovok of another stage
Working on another stage, the plan of the initial premises was laid down, the upper plan of laying the SCRAP, and the tables of window materials were put together. Information about the number of cables, components, as well as about installation work and their varity is given in the tables.
The total amount of window materials, components and assembly work was 82,224 rubles.
Stage 3
Tsіlі i zadannya
At this stage, it is necessary to fold the plan for the calculation of the diameter of the merezha, from the designated working stations, rozmіrіv primіschen, after the folded plan, fold the table for the rozrachunka of the diameter of the merezha. So, just behind the folded table, lay down the block diagram after the diagram, work out the cost of designing the LOM.
Razrahunok of the diameter of the mesh
The method of determining the diameter of the mesh can be designed as a table. Row numbers and column numbers are given to the indicators of working stations on the central plan of LOM, and the values of the middle in the table are indicated to be between working stations with the row number and the column number. With any diagonal element, do not take revenge.
The maximum value in this table and the increase in the diameter of the treadmill in the domain of the collation of this LOM.
Table 12
| WS1 | WS3 | WS4 | WS19 | WS20 | WS34 |
| WS1 | 29.10 m | 43.42 m | 76.15 m | 98.48 m | 128.41 m |
| WS3 | 29.10 m | 45.74 m | 78.47 m | 103.80 m | 133.73 m |
| WS4 | 43.42 m | 45.74 m | 32.73 m | 156.98 m | 186.91 m |
| WS19 | 76.15 m | 78.47 m | 32.73 m | 144.45 m | 174.38 m |
| WS20 | 98.48 m | 103.80 m | 156.98 m | 144.45 m | 29.93 m |
| WS34 | 128.41 m | 133.73 m | 186.91 m | 174.38 m | 29.93 m |
In order to make a project for the LOM, it is necessary to correctly complete 3 minds:
1. The number of working stations can be revisited 1024 approx.
2. Two-way signal jam (PDV) between two stations is not responsible for overshooting 575bt.
3. The shortest time between shots and the hour of the passage of all shots through all repetitions can be revisited 49bt.
Structural diagram of LOM
The block diagram describes the LOM with the diameter of the tether from WS4 to WS34.
Scheme 5
Rozrahunok PDV
When rozrahunku PDV it is necessary to file with a preliminary table and output data (footage, type of cable system, block diagram).
Table 13. Dovidkova PDV table
| segment type | Base of the left segment | Base of the intermediate segment | Base right segment | Tie in the middle by 1 meter | Maximum length of a segment |
| 10BASE-5 | 11,8 | 46,5 | 169,5 | 0,866 | 500 |
| 10BASE-2 | 11,8 | 46,5 | 169,5 | 0,1026 | 185 |
| 100BASE-T | 15,3 | 42 | 165 | 0,113 | 100 |
| 10BASE-FB | - | 24 | - | 0,1 | 2000 |
| 10BASE-FL | 12,3 | 33,5 | 156,5 | 0,1 | 2000 |
| Foilr | 7,8 | 29 | 152 | 0,1 | 1000 |
| AUI(>2m) | 0,26 | 2+48 |
Rozrahunok PDV (from 1 to 4):
Livy Segment1: 15.3 +20.93 * 0.113 = 17.67 bt
Intermediate Segment2: 42 +50.96 * 0.113 = 47.76 bt
Intermediate Segment3: 42 +81.18 * 0.113 = 51.17 bt
Right Segment4: 169.5 +33.84 * 0.1026 = 172.97 bt
Rozrahunok PDV (from 4 to 1):
Livy Segment1: 11.8 +33.84 * 0.1026 = 15.27 bt
Intermediate Segment2: 42 +81.18 * 0.113 = 51.17 bt
Intermediate Segment3: 42 +50.96 * 0.113 = 47.76 bt
Right Segment4: 165 +20.93 * 0.113 = 167.37bt
So, if the value is less than 575bt, in order to pass the line following the criterion of the maximum possible jamming of the signal turnover, with a maximum limit of 186.91 m.
Rozrahunok PVV
Table 14. Table of PVV bit intervals
| segment type | transmission segment | Intermediate segment |
| 10BASE-2 | 16 | 11 |
| 10BASE-5 | 16 | 11 |
| 10BASE-FB | – | 2 |
| 10BASE-FL | 10,5 | 8 |
| 100BASE-T | 10,5 | 8 |
Rozrahunok PVV (h 1 on 4 ):
Libya Segment1: 100BASE-T - 10.5 bt
Intermediate Segment2: 100BASE-T – 8bt
Right Segment4: 10BASE2 - 16bt
Rozrahunok PVV (from 4 to 1):
· Libya Segment4: 10BASE2 - 16bt
Intermediate Segment3: 100BASE-T – 8bt
Intermediate Segment2:100BASE-T – 8bt
Right Segment1: 100BASE-T - 10.5 bt
Given the LOM for the criterion of PVV does not exceed 49bt. In such a rank, the LOM was designed, represented by a structural diagram, povnistyu practical . Dotrimannya tsikh could ensure the correctness of the work of the SCRAP in quiet situations, if they break simple rules measure configuration.
Visnovok
Pratsyyuchi over the course project, vivchiv the entire cycle of design and implementation of this LAN. The bula was designed by LOM for the primary use of one of the buildings of the Petrovsky College for the Ethernet standard with the “Vita Pair” and “Thin coax” cables for all parameters, with the various standards of 10Base-T and 10Base.
There were carried out examinations of the diameter of the LOM, and examinations of the reverification of the LAN practicality for the additional method of bit intervals. This method shows that LOM is designed to be practical and comply with all requirements and criteria of the Ethernet standard.
Zmist
Entry
Chapter 1 Understanding that classification of computer systems
1.1 Purpose of the computer system
1.2 Classification of computer systems
Chapter 2
2.1 Local enumeration measure (LAN)
2.2 Global Counting Measure (GWP)
Visnovok
List of victorious literature
Entry
The entrance of Russia to the world of information expanse draws on the widest range of new information technologies, and on the first black, computer merezh. With this, the ability of the koristuvach is sharply growing, both at the right hand of the servants of their clients, and at the top of the authorities’ organizational and economic tasks.
Prerechno scho, scho schasnі kom'yuternі merezhі є system, mozhlivostі і characteristics koї in tіlоmu іstotno vіdpovidnі vіdpovіdnі vіdpovidnі vіdpovidnі pokaznіnі simple ї sumi storіvnyh elementі v merezhiі personal kompyuterіv vіdsutnostі vzaєmodії mizh them.
The advantages of computer networks zoomed in on them widely in the information systems of the credit and financial sphere, in state administration bodies and municipal self-regulation, enterprises and organizations.
Computer systems and information processing technologies have become the basis for modern information systems. The computer of the ninth line is not looked at as an extension of the processing, but as a “window” in the computer network, making communication with the resources of the network and other short-term resources.
For the rest of the world, the Internet has turned into a world scale phenomenon. Merezha, as until recently was victorious among a number of high-ranking, state servants and practitioners of lighting installations in their professional activities, became available for large and small corporations and for individuals.
The method of this course work is to get to know the basics of encouraging the functioning of computer networks, the organization of work and computer networks. To achieve the goal, it is necessary to set the low task:
Acquaintance with computer chains, seeing their features and powers;
Characteristics of the main methods of stimulating a fence (topology of a fence);
Education of scientific and methodological literature from the source
Chapter 1 Understanding the classification of computer systems
1.1 Appointment of a computer system
The main recognition of computer networks is the use of multiple resources and the creation of an interactive link, both in the middle of one company, and beyond the borders. Resources - data, add-ons and peripheral attachments, such as an old disk drive, printer, mouse, modem or joystick.
Computers that enter the meter have the following functions:
Organization of access to the measure
Information transfer management
Nadannya counting resources and services to the coristuvachi of the merezh.
In Denmark, the local counting (LAN) naboules were already wide in width. Tse viklikano kіlkom reasons:
Combination of computers in a measure allows you to significantly save money for a change in the amount of money for the use of computers (sufficient disk space on a file server (the head computer of a measure) installed on a new software product, vikoristovanimi dekilkom working stations);
Local borders allow wicking Postal screenshot for transferring information to another computer, which allows in the shortest term to transfer documents from one computer to another;
Local dimensions, due to the presence of special software (PS), serve to organize a split list of files (for example, accountants on decal machines can process the postings of one and the same accounting book).
For the most part, in some spheres of activity it is simply impossible to do without CREW. To such spheres lie: banking on the right, warehouse operations of great companies, electronic archives of libraries and others. In these spheres of the skin, a working station is taken, in principle, it cannot save all information (mainly, through a too great deal).
Globally counting the merezha - the merezha, which connects computers, geographically farest from each other. Vіdіznyaєtsya vіd іn localі ї merezhі more protyanіy komіnіkatsіyami (satellite, kabelnymi іn.). The global merge unites the local merge.
The global network of the Internet, which served once and for all to senior and primary groups, whose interests ranged right up to access to supercomputers, is becoming more and more popular in the business world.
1.2 Classification of computer systems
According to the method of organization, the measures are divided into real pieces.
Piecemerezhі (pseudo-merezі) allow you to connect computers at once through successive or parallel ports and do not require additional attachments. Some calls in such a network are called a call on a null modem (the modem is not victorious). Self-hosted is called null-modem. Piecemeal lines are victorious, if it is necessary to transfer information from one computer to another. MS-DOS and windows are provided with special programs for the implementation of a null-modem network.
Real networks allow you to connect computers for additional special attachments in switching and a physical medium for data transmission.
/> Territorial breadth of borders can be local, global, regional and local.
Local counting network (LAN) - Local Area Networks (LAN) - the whole group (communication system) of a small number of computers, combined with a double-width medium of transmission of data, roztashovaniy on the exchange for the size of a small area in between one day, what is close (sound at the radius no more than 1-2 km)
Globally counting network (WAN chi WAN - World Area NetWork) - a network that connects computers, geographically large distances from each other. Vіdіznyaєtsya vіd іn localі ї merezhі more protyanіy komіnіkatsіyami (satellite, kabelnymi іn.). Svіtova merezha united local merezha.
Miska merezha (MAN - Metropolitan Area NetWork) - merezha, as a service to the information needs of the great city.
Regional - distribution on the territory of the city and the region.
So, for the rest of the hour, the fahivtsy see such a kind of bank, like a bank, as they represent a small corporate bank of a great company. It is obvious that the specifics of banking activities pred'yavlyayet zhorstki vomogi to the systems of protection of information in the computer systems of the bank. No less important is the role of the need for security of uninterrupted and uninterrupted work in the event of a corporate measure, the shards of winding a short-time battle in your robots can be brought up to gigantic battles.
For trustworthiness, they distinguish between vіdomchi and sovereign cities. Vіdomchi belong to one organization and roztashovuetsya in the same territory.
Sovereign merezhi - merezhi, like in sovereign structures.
For the speed of transmission of information, computer networks are divided into low-, medium-high speed.
low speed (up to 10Mb/s),
medium speed (up to 100Mb/s),
high-speed (over 100 Mb/s);
Fallow in recognition of the technical solutions of the land can be mothers of different configurations (or, as it seems, architecture, or topology).
In the loop topology, information is transmitted by a closed channel. The skin subscriber without intermediary po'yazaniy іz two nearest susіdami, wanting in principle zdatny zv'yazatisya s be-yakim subscriber merezhі.
At the mirror-like (radial) center, there is a central computer that communicates sequentially with subscribers and calls one to one.
The bus configuration of the computer is connected to a channel (bus) that is important for them, through which they can exchange messages.
A tree-like one has a “head” computer, for example, an advancing level computer, and so on.
In addition, it is possible to configure without a clear nature of the connections; boundary є povnozv'yazkovy konfіguratsіya, if the skin computer is at least intermittently connected with any other computer.
At a glance, the organization of interoperability of computers, links to share on a peer-to-peer (Peer-to-Peer Network) and a visible server (Dedicated Server Network).
All computers are peer-to-peer networks. Be-yakoy koristuvach merezhі can take away access to data that is saved on any computer.
Peer-to-peer networks can be organized behind the help of such operating systems, like LANtastic, windows "3.11, Novell Netware Lite. Designed by programs, they work both with DOS and Windows. Peer-to-peer networks can also be organized on the basis of all modern 32-bit operating systems - Windows 9x \ME\2k, Windows NTworkstation version, OS/2) and others.
Advantages of peer-to-peer networks:
1) the most easy to install and operate.
2) operating systems DOS and Windows may have the necessary functions that allow peer-to-peer networking.
Not a lot of peer-to-peer merezh at tsomu, which makes it difficult to get the supply of information. Therefore, such a way of organizing a network of victories is for a network with a small number of computers, and there, de feeding the protection of data is not important.
In the hierarchical measure, when installing the measure, one or more computers are seen, which manage the exchange of data according to the measure and distribution of resources. Such a computer is called a server.
Whether a computer that can access the services of a server is called a client or a work station.
The server in ієrarchіchnykh merezhakh - tse postіyne collection of resources, which are divided. The server itself can be a client only a larger server high levelієrarchії. Therefore, hierarchical lines are sometimes called lines with a visible server.
Servers and sound with high-performance computers, possibly, with a small number of parallel processors, with high-capacity hard drives, with a high-capacity tethered card (100 Mb/s and more).
The ІІєrarchical model of the line is the most beautiful, the shards allow you to create the most stacked structure of the line and more rationally split the resources.
Also, the transfer of the archival treasury is a greater high rіven for the protection of data.
To a few ієarkhіchnoi merezha, in equal parts with peer-to-peer merezha, lie:
1) the need for an additional OS for the server.
2) greater height of installation and modernization of the fence.
3) Necessity to see an open computer as a server.
Chapter 2
2.1 Local enumeration measure (LAN)
Local areas (LZ EOM) combine a relatively small number of computers (sound from 10 to 100, if you want to zoom in and out more) in the boundaries of one application (primary computer class), whether you install it (for example, at a university). The traditional name is the local numbering of the merezha (LAN)) - it’s more like a danina at the same time, if the merezhi were mostly victorious and the numbering of the counting orders; The cost of the LZ is explained by the fact that 60% to 90% of the necessary installation information circulates in the middle, without requiring the output of a name.
The creation of automated business management systems (ACS) made a great contribution to the development of LZ. ACS includes a sprinkling of automated work stations (AWS), control complexes, control points. The more important field, in which the LZ brought their effectiveness - the creation of a class-calculating technique (KUVT).
Zavdyaki is good enough for small lengths of line communication (as a rule, no more than 300 meters), via LZ it is possible to transmit information to digital look with high speed transmission. On larger distances, such a method of transmission is unacceptable due to the inevitable extinction of high-frequency signals, in these cases it is possible to go into advanced technical (digital-analog conversions) and software (protocols for correcting pardons and other) solutions.
A characteristic feature of the LZ is the presence of a communication link for all subscribers in a high-speed channel for communication of information transmission in a digital form.
Іsnuyut provіdnі і bezdrotovі channels. The skin of them is characterized by the sing values of the suffixes from the point of view of the organization of the LZ parameters:
Data transmission speed;
Maximum length of line;
Transmission protection;
Mechanical strength;
Transparency and ease of installation;
Vartist.
At the given hour, ring out the chotiri tipi of the fencing cables:
Coaxial cable;
Vita pair unprotected;
Twisted couple stolen;
Fiber optic cable.
The first three types of cables transmit an electric signal by medium conductors. Fiber optic cables transmit light over glass fiber.
More measures allow for a few options for cable services.
Coaxial cables are made up of two conductors, sharpened with insulating balls. The first sharіzolyatsії otochuє central midny provіd. This ball of weaves is called a callous conductor, which is on the screen. The most wide coaxial cables are thin and thin Ethernet cables. Such a design ensures the safety of the garna of over-protection and a small loss of the signal on the guards.
There are thin (approximately 10 mm in diameter) and thin (approximately 4 mm) coaxial cables. Volodiyuchi advantages in terms of changes, cost, durability, coaxial cable is more expensive and foldable in installation (yogo foldable is stretched through cable channels), thinner. Until the rest of the hour, a thin coaxial cable is a reasonable compromise between the main parameters of a LAN link and in Russian minds, it is most likely to win for the organization of great LZ enterprises and installations. However, more expensive cables will ensure safe transmission of data to a larger width and less sensitive to electromagnetic shifts.
Viti bet represent two leads, twisted at once, throw six inches per inch to secure the protection of the electromagnetic transitions and to make it easier for the Idansu or the electric support. For other names, call (we are sorry for such a phone, є “IBM type-3”. In the USA, such cables are laid on weekdays to ensure telephone calls. first, unprotected twisting bets are sensitive to electromagnetic shifts, for example, electrical noises that are created by luminescent lamps and elevators, that collapse.
It is also important to note that telephone lines do not need to be laid in a straight line. The cable, which connects two orders of accommodation, can actually get around half the time. Underestimation of the length of the cable at times can lead to the fact that it will overestimate the maximum allowable length.
Protecting twisted parishozhі s unprotected, for the sake of the fact that the stench of vicorist more tovst carry out that protection from the outer inlet of the insulator. The largest extension type of such a cable, which is installed in local areas, "IBM type-1" is a protection cable with two twisted pairs of uninterrupted wire. In new booths, the best option is to have a “type-2” cable, so that you turn on the cable for transmitting data and not protecting the bet with an uninterrupted wire for transmitting telephone conversations. In this way, "type-2" allows you to twist one cable to transmit both telephone conversations and data on a local basis.
Protect and retelne to increase the number of twists per inch.
Fiber-optic cables transmit data at the sight of light pulses, curse the wires. Most of the systems of local networks are currently supporting fiber-optic cable installations. Fiber optic cable can be compared to other copper cable options. Fiber optic cables are safe find swedishness transmission; the stench is greater than that, for those who are not able to enter information packets through electromagnetic passages. The optical cable is thin and flexible, so that it can be easily transported with a more important medium cable. However, the most important are those that only an optical cable can suffice for the capacity of the building, as in the future it will be necessary for larger swedish networks.
So far, the price of a fiber-optic cable is significantly higher than the average. Installing an optical cable with a mid-wire cable is more laborious, but depending on the degree of responsibility, it is resolutely polished and polished to secure the above ground. the sticking of optical fibers is successfully achieved.
Bezdrotovy sv'yazok on the radios of the low-frequency range can be vikoristovuvatsya for the organization of merezh at the boundaries of the great premises such as hangars or pavilions, there, de vikoristannya svishchaynyh line sv'yazku is difficult or not enough. In addition, bezdrotovy lines can po'yazuvat in the distance segments of local merezh on vіdstanyakh 3 - 5 km (with an antenna type hvilovy channel) and 25 km (with a straightened parabolic antenna) for clear line of sight. The organization of a dartless mesh is much more expensive, lower.
For connection of computers for an additional line connection of the LZ, adapters are needed (otherwise, as they are called, they pay). The most common ones are: adapters of the following three types:
Of these, the rest of Russia was oversized. The adapter is inserted directly into the middle slot of the motherboard of the personal computer and to the new one on the back panel of the system unit there is a line of communication with the LZ. The adapter, according to its type, implements the same access strategy from one computer to another.
To ensure efficient work in the transfer of data, there are different communication protocols for transferring data - sets of rules that are responsible for the transmission and receiving side for the efficient exchange of data. Protocols are sets of rules and procedures that regulate the order in which a call is made. Protocols - tse rules and technical procedures that allow a number of computers when combined in a measure to communicate one with one.
Use of anonymous protocols. I want all the stinks to take part in the implementation of the connection, the skin protocol may vary in number, vikonu different tasks, may have its own advantages and exchange.
The protocols work on different levels of the OSI/ISO interoperability model. The functions of the protocols are determined by the equal, on which wine is practiced. Kіlkaprotokolіv can be practiced in full. This is the stack of titles, or the collection of protocols.
Just as the functions are separated across all the layers of the OSI model, so the protocols work together on different layers of the protocol stack. Peers in the protocol stack match those of the OSI model. In the totality of the protocols, to give an overall description of the functions and capabilities of the stack.
The transfer of data as soon as possible, from a technical point of view, is due to the accumulation of the last steps, the skin one needs to follow its own procedures or protocol. In this rank, strict callousness is taken away from the vicons of the singing diy.
In addition, all of these are due to be vikonan in the same sequence on the leather lace computer. On the computer-controller, they are straight up to the beast down, and on the computer-controller, from the bottom up.
The computer-controller allows the protocol to follow these steps: split the data into small blocks, called packets, with which you can work out the protocol, add address information to the packets, so that the computer-otrimuvach can instantly determine what this data is recognized by itself data before transfer through a fee twill adapter and farther - along the cable.
The computer-operator is allowed to follow the protocol on its own, but in the reverse order: it receives data packets from the network cable; transfers data to the computer through the merging adapter board; reads all the service information from the packet, added by the computer-controller, copies the data from the packet to the buffer - for their merging with the output block, transfers the appendix of this block of data to the format, which is victorious.
The computer-controller, and the computer-controller, need to vikonate the skin department in the same way, so that the data came through the border and were collected from the authorities.
For example, two protocols will separate the data into packets differently and add information (sequence of packets, synchronization and re-verification of pardons), the same computer, vicorist one of these protocols, you can successfully communicate with the computer, the computer other protocol.
Until the mid-80s, most of the local meshes were insulated. The stench served the surrounding companies and rarely joined the great system. However, if the local merezhs reached a high level of development and the general information transmitted by them, the stinks became components of the great merezhs. Data that is transferred from one local network to another via one of the possible routes is called routed. The protocols that support the transfer of data between networks over decal routes are called protocols that are routed.
Among the anonymous protocols, the most widely used are:
· IPX/SPX and NWLmk;
· Set of OSI protocols.
2.2 Global Counting Measure (GWP)
WAN (World Area Network) is a global network covering large geographic regions, including both local networks and other telecommunications networks and extensions. WAN butt - frames with packet switching (Frame relay), which can "remove" between themselves different computer chains.
Today, if the geographic boundaries of the border are expanded, so that the connections between different places and powers are changed to the global counting network [WAN (WAN)], and the number of computers in the border can change from dozens to thousands.
The Internet is a global computer network that embraces the entire world. Today the Internet may have close to 15 million subscribers in more than 150 countries of the world. Shhomіsyatsya rozmіr merezhі zbіlshuєtsya by 7-10%. The Internet establishes itself as a bi-core, which ensures the communication of various informational networks, which should lie with the various institutions of the whole world, one by one.
Even earlier, the network was victorious as a medium for transferring files and acknowledging electronic mail, but today there are more complicated tasks for access to resources. Close to three fates were the creation of shells, which support the functions of a common search and access to the distribution of information resources, electronic archives.
The Internet, which served once and for all to senior and senior groups, whose interests stretched right up to access to supercomputers, is becoming more and more popular with the business community.
Companies have peace of mind, cheap global calls, availability for conducting joint work, available programs, a unique Internet database. The stinks look at the global measure as an addition to their local lines.
For a low service rate (often a fixed monthly fee for victorious lines or a telephone) coristuvachi can gain access to commercial and non-commercial information services in the USA, Canada, Australia and other European countries. In the archives of free access on the Internet, you can find practical information on all areas of human activity, starting from new scientific findings until the weather forecast for tomorrow.
In addition, the Internet offers a unique opportunity for cheap, reliable and confidential global communication throughout the world. This seems to be more convenient for firms that spread their names around the world, transnational corporations and management structures. Sound, using the Internet infrastructure for international communication is much cheaper than direct computer communication via a satellite channel or via telephone.
E-mail is the widest service of the Internet. You can send your address by e-mail about 20 million. Sending a sheet by electronic mail is much cheaper than sending a sent sheet. Krіm moreover, podomlennya, nadіslane email reach the addressee for a few years, then the same list can reach the addressee for a few days, or navit tizhniv.
In the present hour, in the Internet, practically all types of communication lines are victorious from low-width telephone lines to high-width digital satellite channels.
In fact, the Internet is made up of impersonal local and global networks that belong to different companies and enterprises, which are interconnected by different lines of communication.
How and in be-yakіy іnshіy measure in the Internet іsnuє 7 rіvnіv vzaєmodії міzh computers: physical, logical, rіveny, transport, rіvnіv sіv'yazku, predstavnіtskiy applied rіven. Vidpovidno to the skin level in vzaimodії vіdpovіdaє set of protocols (to rule vzaimodії).
The protocols of the physical level determine the appearance and characteristics of the line connection between computers. In the Internet, practically all vіdomі vіdomi vіdomi vіdі vіdі vіdnі chаnі zv'yazku vіd simple drotu (twisted twirl pair) up to fibre-optic line zv'yazku (VOLZ).
For the skin type of line communication, a separate protocol of logical equalization has been developed, which deals with the management of the transmission of information over the channel. The SLIP (Serial Line Interface Protocol) and PPP (Point to Point Protocol) protocols are considered to be the logical level protocols for telephone lines.
For linking cabel-local networks - ce package drivers for LAN boards.
Merezhny equal protocols are charged for the transfer of data between outbuildings at different merezhs, so they are engaged in packet routing at the merezh. IP (Internet Protocol) and ARP (Address Resolution Protocol) lie before the protocols.
Transport layer protocols control the transfer of data from one program to another. Before the protocols of the transport layer, TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) lie.
The protocols of the equal sessions are to be connected for the installation, support and reduction of the air channels. The Internet is already working on the TCP and UDP protocols, and the UUCP protocol (Unix to Unix Copy Protocol).
Protocols and representatives of the level are engaged in the maintenance of application programs. Before the program representative, there are programs that are launched, for example, on a Unix server, for the provision of various services to subscribers. These programs include: telnet server, FTP server, Gopher server, NFS server, NNTP (Net News Transfer Protocol), SMTP (Simple Mail Transfer Protocol), POP2 and POP3 (Post Office Protocol), etc.
Prior to the protocols of the applied level, one can see the mere services and programs of their work.
Internet - a network that is constantly developing, for which everything is ahead, we will be aware that our country is in the midst of progress.
/>/>/>/>/>/>/>/>/>/>/>/>Visnovok
The computer of the merging is the association of a number of EOM for the joint execution of informational, enumeration, initial and other tasks.
The main recognition of computer systems is the accumulation of resources and the development of interactive communication as the middle of one company, so
and beyond the borders.
The local computer of the merezha is the collection of computers connected by the lines of the connection, which ensures the potential of the sap resource of the com- puters. From the other side, more simply kazhuchi, computer merezha - tse sukupnіst kom'yuterіv і rіznih pristroїv, shko іnformatsiyny іnformatsiyny іmіnі kom'yuterymi іnmіrzhі without vykoristannya yakіh yakіh іnіzhnyh nіїv іnformatsії.
Globally counting network (WAN chi WAN - World Area NetWork) - a network that connects computers, geographically large distances from each other. Svіtova merezha united local merezha.
The Internet is a global computer network that embraces the entire world.
In fact, the Internet is made up of impersonal local and global networks that lie between different companies and enterprises that connect with each other with different lines of communication.
List of victorious literature
1. "Internet at your home", S. V. Simonovich, V. I. Murakhovsky, TOV "AST-Press Book", Moscow 2002.
2. Gerasimenko V.G., Nesterovsky I.P., Pentyukhov V.V. that in. Obchislyuvalnye measures and zasob їkh zahistu: Headmaster / Gerasimenko V.G., Nesterovsky I.P., Pentyukhov V.V. that in. - Voronezh: VDTU, 1998. - 124 p.
3. Tizhnevik for entrepreneurs and fahivtsiv at the gallery of information technologies ComputerWeek Moscow.
4. Magazine for personal computers Koristuvachіv Svіt PK.
5. Kamalyan A.K., Kulov S.A., Nazarenko K.M. that in. Computer measurements and the collection of information: Headmaster / Kamalyan A.K., Kulev S.A., Nazarenko K.M. ta in - Voronezh: VDAU, 2003.-119p.
6. Kurnosov A.P. Workshop on Informatics / Ed. Kurnosova O.P. Voronezh: VDAU, 2001. - 173 p.
7. Malishev R.A. - Ribinsk, 2005. - 83 p.
8. Olifer V.G., Olifer N.A. Merezhev operating systems / V.G. Olifer, N.A. Olifer. - St. Petersburg: Peter, 2002. - 544 p.: Іl.
9. Olifer V.G., Olifer N.A. Computer systems. Principles, technologies, protocols / V.G. Olifer, N.A. Olifer. - St. Petersburg: Peter, 2002. - 672 p.: il.
10. Simonovich S.V. Informatics. Basic course / Simonovich S.V. that in. - St. Petersburg: publishing house "Piter", 2000. - 640 p.: il.
Entry
Chapter 1
1.1 Organization structure
1.2 Description of the organization's hardware
1.3 Description of software that is awarded in the organization
1.4 Description of the activities of the information technology organization
Chapter 2
2.1 Translation of instructions, necessary organization of the working place of the computer systems adjuster of the hardware and software systems adjuster.
2.2 Implementation of a system of preventive maintenance of computers in a group
2.3 Description of the control, diagnostics and implementation of computer systems and complexes
2.4 Revealing the incomplete security systems of steel robotic computer systems and complexes. Propositions for a thorough given system
Chapter 3. Description of the information system that the organization has
3.1 Analysis / development of the structure of the information system
3.2 Description of the database management system/software to be developed for distribution
3.3 Description of the main objects of the information system
3.4 Instructions for employees to work with an information system
3.4.1 Assigned programs
3.4.2 Clean up the software
3.4.3 Programming
3.4.4 Operator notification
3.5 Description of the zaobіv, priyomіv vakhistu іnformatsiї pіd hr work z іnformatsіynoy system
Visnovok
List of vicorists dzherel
Entry
Today, the whole world is collaborating for additional computers. High-tech machines are in the skin's homeland, without them there is no daily business. Tilki not kozhen vmіє rozmovlyat with a computer yogo mine and learn yogo rozumіti mov people. Being familiar with computer systems means being one step ahead of the hour. And yet nothing in the world develops so quickly, like computer technology. It doesn’t seem like a gift to Aja: “The computer has been installed in the past, as only a few hopes in sales.”
Knowing how to improve computer systems, you begin to understand the language of numbers, know automated design systems, microprocessor systems and peripherals. In other words, you begin to speak with my computer alone. Win, like a friend, to solve problems, assess risks and take decisions in non-standard situations, which robots should cost. The range of knowledge of a specialist in computer systems is wide: from small salons to large enterprises - a designer, a computer, a necessary system administrator - a specialist in computer systems and complexes.
In order to better prepare fahіvtsіv tsієї professії, nebіbnі practical vminnya. The very thing for whom at the beginning of the pledges was given practical employment.
Practice from the profile of specialty is the primary form of employment in organizations (enterprises) of various forms of authority and organizational and legal forms.
Practice with a profile of specialty is carried out with the method of training fundamental principles the functioning of organizations and the establishment of the management of the practice and the regulation of social and labor vodnosin, employment services; the principles of organizing the work of services and drozdilіv, which are engaged in catering for the recruitment, placement and appearance of personnel, cadres, wages, wages, personnel management; and start the analysis of documentation, which ensures the activity of assigned services. It allows you to get theoretical training from practical work in specific work areas. Before the start of practice, enter:
- monitoring, diagnostics and updating the practicality of computer systems and complexes
- system technical service computer systems and complexes
- improvement of hardware and software systems and complexes;
- installation, configuration and adjustment of the operating system, drivers, resident programs;
- maintenance of customer databases;
- demonstrating the possibilities of folding technical systems;
- consulting on the selection of folding technical systems;
- informing you about the use of the selected options for technical solutions, licenses.
- In the course of practice with a profile of specialty, it is necessary to see the following work:
- characteristics of the enterprise Analysis of the external and internal environment of the organization;
- description of the technical and software park of enterprise;
- development of methods and regulations for carrying out preventive maintenance of computer equipment;
- development of the system for modernizing the technical and software park of the enterprise;
- rozroblennya rules of the policy of information security;
- designing the structure of the database of organizations;
- general description of configuration/database, interface, data entry and display forms;
- configuring and configuring data bases, setting privileges for access to data;
- folding instructions for coristuvachevy pіd h vykoristannya song system for managing data bases;
- rozrobka presentation of goods in organizations.
Chapter 1
1.1. Organization structure
The principle of the Company is one of the largest companies in the Smolensk metropolitan area, which specializes in the manufacture and implementation of computers, advanced power supply and integration, as well as in the supply of office and mobile equipment, components and fiber materials.
Stores of representations have the widest selection of modern computer equipment: personal and portable computers, monitors, office equipment from leading light sources (Samsung, Acer, Phillips, Toshiba, MSI, Intel, AMD, Asus, Dell, LG, Canon, Epson and rich others).
Great choice of window materials (paper, cartridges for inkjet and laser printers, toner, ink etc.)
At the current moment, he is the post-manager of the wealthy of the great state and commercial organizations of Smolensk and Smolensk region.
Also, having become the first Smolensk maker of computers certified according to GOST, it can obtain an international ISO 9001 quality certificate.
As the first Smolensk company Gold Certified Partner of the Microsoft company with the competence of "Managing licenses in organizations", proposing to the successors of software security for different programs of licensing, which allows them to choose the best option.
1.2. Description of the organization's hardware security
In our time, the part of organizing victorious work in a robotic modern automated system is already more important. computer technology, software security and information transfer.
12 computers were founded.
To the warehouse of hardware security of the computer for the working area enter:
- type i processor frequency - Intel Core 2 Duo 2.4 Hz;
- obsyag operational memory-2048 MB;
- HDD type and size - WDCWD1600AAJS-61 WAA0 (IDE500GB);
- type of motherboard integrated;
- videocard type - budged;
- type CD-ROM-DVD-R;
- sound card type - sound card;
- tie card type-ETHERNET (100 MB/sec);
- BIOS type - overwritten;
- type and size of the monitor-RK 17''.
To the warehouse of the system software for the PC for the working area enter:
- OS - Windows XP Professional;
- virobnik-Microsoft;
- discharge OS-32;
- hacked file system-NTFS;
- view of the rendered interface-graphics.
Minimum distance to the architecture of the computer under the hour of installation of this OS:
- Intel processor іz with a frequency of 2.4 Hz or shvidshy;
- at least 64 MB of RAM (recommended less than 128 MB);
- not less than 1.5 GB free space on hard drive;
- drive for CD- or DVD-disks;
- keyboard, mouse MicrosoftMouse.
The organization has installed the S5000MB (S5332LNi) server as a computer server: Core i5-4590 / 8 GB / 2 x 1 TB SATA RAID.
To the hardware warehouse of the server computer enter:
- Intel processor
- Storage interface SATA 6Gb/s
- HDD storage type
- RAM 8 GB
- Merezheva card 10/100/1000 Mbit/s
In the organization there are peripheral devices HP LaserJet P2035, HP LaserJet PRO Color CP1025, HP LaserJet Pro P1102, HP SCANJET 300, Samsung ML-1210
1.3. Description of the software that wins in the organization
How the operating system wins software security Microsoft Windows XP Professional.
Software security of personal computers:
- Microsoft Office 2007
- KasperskyAnti-Virus
- 1C: Business (1C: Accounting).
- 1С: TRADE AND WAREHOUSE 7.7
- Windows 2000 Server SP4
Windows XP Professional is an operating system (OS) of the Windows NT family of Microsoft Corporation. It was released on April 25, 2005 as a version of Windows XP for the personal computer platform.
Kaspersky Antivirus (KAV) is an antivirus software developed by Kaspersky Lab. Nadaet koristuvachevi zahist against viruses, trojans, spyware, rootkits, adware, as well as other threats for the help of a proactive hijacker, which includes the HIPS component (only for older versions, which are called "Kaspersky internet security 2009+, de '+' - the sequence number of the forward register, which scales up by one in the same way to the number of the fate that comes after the fate of the release of the black version of the antivirus"). On the cob, on the cob of the 1990s, called V, then - AntiViral Toolkit Pro.
1C: Enterprise with a software system for automating various economic activities. For a specific software product, which should be included before the 1C: Acceptance program system, those functions and capabilities are included, as they indicate recognition of this product.
Usі skladovі system program 1C: Pіdpriєmstvo can be added to the Technological platform and Configuration. p align="justify"> Technological platform is a set of different mechanisms that are victorious for automating economic activity and do not fall into the category of specific legislation and methodology. Change it with good applied solutions. The skin configuration is directed to the automation of the main sphere of economic activity and, obviously, in accordance with the adopted legislation.
"1C: Trading and Warehouse" is recognized for the appearance of any kind of trading operations. Zavdyaki gnuchkosti and nastroyuvannosti system zdatna vykonuvat all functions in the form - in the form of a conclusion and the introduction of the first documents to the removal of other information and analytical information.
“1C: Trade and Warehouse” automates the work at all stages of business activity and allows:
- conduct a rozdіlny managerial and financial appearance
- keep a record of the name of a number of legal entities
- maintain a batch image of the commodity stock with the possibility of choosing the write-off method (FIFO, LIFO, average)
- to keep a detailed look of your goods and goods taken for sale
- make purchases and sales of goods
- to automatically start filling in documents on the basis of earlier data entry
- conduct a form of mutual frost protection from purchases and post-employees, details of mutual frost protection for other contracts
- form the necessary primary documents
- draw up accounts-invoices, automatically create a sales book and a purchase book, keep a balance sheet at the VMD numbers
- pick up the reservation of goods and control payment
- keep the appearance of cats on the rozrahunkovy rachunks and at the kasі
- maintain the form of commodity credits and control their repayment
- keep a record of the goods transferred for sale, their return and payment
At “1C: Trade and Warehouse” you can:
- ask for a skin product necessary kіlkіst cіn different type, save the prices of post-employees, automatically control and promptly change the price level
- process from mutual documents
- check the automatic recalculation of prices for the write-off of goods
- promptly make changes for additional group processing of documents and documents
- to conduct a form of goods in different units of the world,
- and koshtiv - in other currencies
- take away the most important information and analytical information about the goods and pennies
- automatically form accounting entries for 1C: Accounting.
"1C: Trade and Warehouse"
- feasibility of fencing to coristuvachas of “direct” access to information
- special mode of data removal from the control of cross-feeds
- Possibility of fences for koristuvachs to edit data for the past summer period
- the installation of a fence on the editing of other forms of documents
- "Zamikannya" of the system coristuvachem with timchasovy attached work.
Software for the server computer
Windows 2000 Server is a rich operating system that provides the functions of a file server, a program server, a Web server, and a communications server. The new system in parallel with the front ensures greater reliability, security and ease of management. More importantly, Windows 2000 Server has a great set of different services based on Active Directory - a rich, scalable directory built around the best of Internet technologies and fully integrated with the system. Active Directory significantly simplifies the administration of systems and searches for resources from a corporate organization.
Numerous Web and Internet services, which are included before the Windows 2000 Server warehouse, allow organizations to widely endorse Internet technologies, create collapsible Web add-ons, and services for the distribution of streaming information (audio, video, etc.) and streaming Windows 2000 Server as platforms for platforms for intranet.
Windows 2000 Server Je promising tsіlovoyu that іnstrumentalnoyu platform for Square postachalnikіv software zabezpechennya (Independent Software Vendor, ISV) that rozrobnikіv recommending BIZNES-dodatkіv, oskіlki in tsomu produktі pіdtrimuyutsya that rozvivayutsya nayperedovіshі service rozpodіlenih dodatkіv, takі yak the DCOM, Dedicated Servers tranzaktsіy that Cherga povіdomlen. In addition, to increase the productivity of Windows 2000 Server, the base product of the Microsoft server family supports a rich processing symmetrical processing (SMP) on two processors and up to 4 GB of memory.
1.4. Description of activity in the field of information technology organizations
Posadovi obov'yazki system administrator:
1. Install on the server and robotic stations, operating systems that are necessary for robotic software security.
2. Set up software configuration on servers and working stations.
3. Supporting the practical station with software security for servers and working stations.
4. Registry of local mail servers, assigning identifiers and passwords
5. Designing technical and software support for coristuvachs, advising coristuvachs on power supply and local measures and programs, compiling instructions for how to work with software security and bringing them to the appearance of coristuvachivs.
6. Set the access rights and control over the management of the resources.
7. Take care of copying, archiving and backing up data.
8. Vzhivaє zakhodіv schodo vіdnovlennya pratsezdatnostі localі mérіzhі pіd h zbїv аbо vykhodіv z fret іn аrе mеrеzhі obladnannya.
9. Viyavlyaє pardons koristuvachіv and software security and live zakhodіv shkodo їх corrections.
10. Carry out monitoring of the measure, expand the proposals for the development of the infrastructure of the measure.
11. Protect security measures (protection against unauthorized access to information, review or change) system files ta danikh), security between intermediaries and mutual modality.
12. Build anti-virus protection for local enumeration, servers and working stations.
13. Ready propositions for modernizing and adding to the borders.
14. Zdіysnyuє control over the installation of local facilities by specialists of third-party organizations.
15. Inform your uninterrupted clerk about the failures of the violation of the rules of the local counting net and come in.
Chapter 2
2.1. Translation of instructions, necessary organization of the working place of the computer systems adjuster of the hardware and software systems adjuster.
The adjuster of hardware and software security is fahіvets, which cheruє robot EOM and nalashtovuє sing type of possession, connected with computer technology that information security. The field of activity of the profession is the installation, maintenance and modernization of equipment and equipment, including hardware and software for personal computers, servers, as well as peripheral attachments, and possession of computer office equipment.
Sobi praci
- hardware and software for personal computers and servers;
- Peripheral possession;
- Multimedia equipment;
- Information resources of local and global computer networks.
Main types of work (labour work)
- Maintenance of hardware security of personal computers, servers, peripheral attachments and equipment, computer office equipment;
– installation and maintenance of software for personal computers, servers, peripherals and equipment;
– modernization of hardware security of personal computers, servers, peripherals and equipment;
- Modernization of software for personal computers, servers, peripherals and equipment.
Professional competencies
– put into operation the technologies of counting;
– to diagnose pratsezdatnіst, fix malfunctions and malfunctions of the hardware security of the calculation technique;
– to replace window glass materials, which are used in the accounting department and office equipment;
- install operating systems on personal computers and servers, as well as fix the interface of the koristuvach;
- administration of operating systems of personal computers and servers;
– to install and improve the work of peripheral outbuildings and control;
– install and update application software for personal computers and servers;
– to diagnose pratsezdatnist, fix problems and failures of the operating system and applied software;
– to optimize the configuration of the calculation technique in a fallow way, depending on whether it hangs, and if it hangs over a rough patch;
– see and add components of personal computers and servers, replace them with sums;
– replace, remove and add the main components of peripheral devices, possessing and computer office equipment;
- update and see versions of operating systems of personal computers and servers;
– update and see versions of application software for personal computers and servers;
– update and see drivers for attachments of personal computers, servers, peripherals and equipment;
– upgrade firmware components of computers, servers, peripherals and equipment
2.2. Implementation of the system of preventive maintenance of computers in the office
Wimogi bezpeki before the cob of roboti
- Clothes and resolutely refuel the installations of special clothes (robe) and technological vzuttya (slippers) according to the standard standards, not allowing the hanging of kintsiv and squeezing the hour of the rush.
- Perevirity and reconciliation in the presence and correctness of the fixed instrument, attaching a safe, carefree vikonnannya works, sobiv іindivіdualnogo zakhist, sobіv fire extinguishing.
- Pereviriti camp zagalnogo and ordinary osvіtlennya.
- Do not carry out any work on the repair of outbuildings, inventory or anything else, so as not to enter the doctor's shoes.
- About all the shortcomings and inaccuracies that were revealed when looking at the worker's job, let the elder change for a living and come in for their full adoption.
- Raztashuvat іnstrument on the working place with the maximum zruchnіstyu for koristuvannya, do not allow the visibility of the objects in the work area.
- Review the presence of the first-aid kit of the 1st medical aid.
Vimogi security pid hour of work
- Pratsyuvati tіlki at the right tare retelly podіgnanomom special clothes and specials. vzuttya and zastosovuvati іndivіdualі і zabі zahistu, put on the working place for chinnymi norms.
- When servicing and repairing workbenches, it is allowed to stop the metal drabins of the exits. The robot from the boxes and other third-party objects is fenced.
- It is necessary to install the drabin carefully, having disproved її steadfastness before the pidyom. Drabini with a height of 1.3 m is due to but with an emphasis.
- Steadyly seek for the right of possession. In case of exit from the verst or the manipulator, the rest are to blame, but zupineni and nestrumleni.
- Pratsyuyte for nayavnosti and spravnosti fencing, blocking and other outbuildings, scho to ensure the safety of work, for the mind sufficient lighting.
- Do not stick around mechanisms, which are known in Russia, and overhead parts of machines, as well as stream-guiding parts of the possession, which are under pressure.
- Treat in order that cleanliness of the working place.
- Third-party objects and tools should be placed on the stand against the mechanisms that are collapsing.
- When starting the machine, make sure to check especially at the workers' presence near the area of robotic machines.
- All repair work on electrical installations, preventive inspection, repair of the next step when the guards are removed (pressure). Vidsutnіst naprugi on jet-carrying parts of the electrical installation should be checked with a voltmeter and a voltage indicator.
- For protection against opikiv when changing lamps in the equipment, the adjuster is guilty of using extra mittens, special keys and attachments.
- Without delay, carrying out the necessary switching on the switching equipment (automatic, knife switch, vimikachi) included in the preparation of the work station due to cry: "Do not turn it on - people work!" – a robot on the line!”.
- For robots, use a hand tool with insulating handles (pliers, pliers, wire cutters, twists), electrically cover it not to the fault of the mother, and gently lie down to the handle.
- Usunennya poshkodzhenya and repairs on the installation are necessary to carry out with the full release of the voltage from the control.
- A portable electric tool (a soldering iron, a lowering transformer), which is fixed, is to blame for testing and mother's inventory number, systematically and in its own way, overturned and repaired.
Wimogi security in emergency situations
- A leather practitioner, who, having revealed damage, could not follow instructions, and ruled for the protection of practice, or remembering the injustice of the possession, which could become unsafe for people, goiter and yazan, tell about the bezperedny kerivnik.
- In quiet depressions, if the injustice of the possession becomes a threatening problem for people, or the possession itself, the practitioner, who has shown it, goiter, come to life when he or she has been pinned down by the possession, and then tell about the bezperedny kerivnik. Usunennya inaccuracies to go through with dotrimanni could be safe.
- As soon as an hour of work becomes an unfortunate depression, it is necessary to give a first medical aid to the victim, tell about your uninterrupted boss and live by visiting to save the situation of an unfortunate depression, as it is not associated with unsafe conditions for the life and health of people.
- When struck by an electric strum, it is necessary to call out the injured person in the strum, at the time of work on the heights to live in, which will protect the yogo fall. Vimknennya possessing the power for the help of vimics, the rose of the plug socket, cutting the wire of life with a tool with insulated handles. It is not possible to turn on the possession of the swede, it is necessary to get used to other entries for the sound of the stream, which has suffered in the air. For water-reinforcement of the injured in the strum-conducting parts, either the dart should be hurried with a club, a doshka, or some other dry object, so as not to conduct an electric strum, if you hope to help, you should be guilty in a dry place, so not to conduct a strum, or put on electric gloves.
- At times, after a technical application, proceed negligently to the first extinguishment with obvious methods (carbonic acid fire extinguishers, asbestos curves, sand) and fire a part.
Vimogi security after the completion of the work
- It is necessary to arrange the work space, tools and supplies.
- Tell the clerk about all the faults, mark the hour of work, that come in, live until you are asleep
- Pick up the overalls at a specially designated place.
Implementation of the system of preventive maintenance of computers in the office
See the technical service of the SVT
The type of technical maintenance is determined by the periodicity and a complex of technological operations with the support of the operational authorities of the SVT.
GOST 28470-90 "System of technical maintenance and repair of technical aids of computational equipment and informatics" designates such a type of maintenance
- regulated;
- more periodically;
- with periodic control;
- with uninterrupted control.
The regulated technical service may be included in the contract with the improvement of the direction, transferred to the operational documentation for the SVT, independently from the technical state.
Periodic technical maintenance is due to be checked at intervals of an hour in the obsyaz, established in the operational documentation for the SVT.
Technical maintenance with periodic control can be overcome from the periodic control of the technical station of the SVT and the necessary complex of technological operations that are installed in the technological documentation.
Technical maintenance with uninterrupted control is due to be duly reviewed prior to the operational documentation for the SVT or technological documentation for the results of continuous control over the technical mill of the SVT.
The control of the technical station of the SVT can be carried out in static and dynamic modes.
In the static control mode, the values of the voltage and the frequency of the sync pulses are overridden by the constant stretching of the last cycle of preventive control, and in the dynamic mode, the periodic changes are transmitted. In this way, for the adjustment of tight modes of operation of the SVT, it is possible to reveal critical for the superiority of the elements.
Preventive control is implemented by hardware and software paths. Apparatus control is carried out for additional special equipment, control and monitoring devices, stands and software and hardware complexes.
Works from the elimination of malfunctions during the hour of preventive control can be divided into the following stages:
- analysis of the nature of the faults in the production line of the SVT;
- control of the parameters of the navkolishny middle and come in at the right time to sleep;
- localization of a pardon and a designated mishap for the help of hardware and software tools of the SVT and for the help of additional equipment;
- usunennya malfunctions;
- updating tasks.
At this hour of the greatest expansion, the following types of technical service systems (STO) were installed:
- Scheduled and scheduled maintenance;
- service for a technical camp;
- Combined service.
Scheduled and scheduled maintenance is based on the calendar principle and the implementation is regulated and periodically technical maintenance. The number of robots are victorious with the method of support of the attachment of the SVT at the reference station, the revealed signals in the setting, the early failures and the commands of the robot of the SVT.
Periodicity of planned and preventive work to lay down according to the type of SVT and minds of exploitation (amount of change and cost).
The advantages of the system - ensure the readiness of the SVT.
Nedolіki system vimagaє great material and physical vitrates.
Zagalom, the system includes the following types of technical maintenance (prevention):
- look around (KO)
- Schedenny MOT (ETO);
- short maintenance;
- double maintenance;
- decade maintenance;
- shomіsyachnі THAT (TO1);
- two-month maintenance;
- pіvіchnі chi seasonal (STO);
- rіchnі THAT;
KO, CE SVT includes inspection of outbuildings, test run swedish proofreading readiness (practicality of outbuildings), as well as the work of carrying out proper prevention (subject to instructions for operation) of all external outbuildings (cleaning, oiling, adjusting thinly).
Under the hour of two-time maintenance, diagnostic tests are being transferred, as well as we see two preventive works, transferring for outside outbuildings.
In the event of a monthly maintenance, the re-verification of the functioning of the SVT is carried out for the help of all the test systems that enter the warehouse of the software security. The re-testing is carried out at the nominal values of the life expectancy of the preventive voltage change + 5%.
Preventive change of voltage allows you to reveal the weakest schemes of the system. Call the schemes of responsibility to save your practice when changing the voltage at the boundaries. However, the old and other factors call for steps to change the working characteristics of the schemes, which can be manifested in preventive modes.
Rechecking the SVT with a preventive change in voltage reveals the prediction of malfunctions, which causes a change in the number of malfunctions, which are important to localize, which lead to failures.
Under the hour of regular prevention, all the necessary work is done, instructions are given for the operation of the existing outbuildings.
During the first (river) maintenance, the same work is carried out, as with the first maintenance. And also all kinds of primary (river) preventive work: sorting, cleaning and installing all mechanical nodes of the outer outbuildings from their one-hour regulation or replacement of parts. Krym tsyogo, an inspection of cables and tires, which should be revived, should be carried out.
A detailed description of the preventive measures is given in the instructions for the operation of the other outbuildings, which are added to the SVT by the virobnik plant.
During the maintenance of the technical station, the work of maintenance may be planned according to the plan and, if necessary, the departure of the object will become (the results of the test), which will support the technical maintenance with uninterrupted control of the nimbo of the technical maintenance.
Prior to scheduled preventive maintenance, there is a need for later preventive maintenance, which is considered to be the main rank after the adoption of serious malfunctions of the SVT. The obsyag of preventive visits is determined by the nature of the fault, which is the fault, and possibly by the consequences.
Visnovok SVT for pre-planned prevention can be carried out, if there are a number of failures, which is blamed for the singing of the installation period, exceeding the allowable values.
The system improves the visibility and correct sizing of various testing aids (PT).
The system allows you to minimize the time spent on the operation of the SVT, but also the readiness of the SVT to the lower stage, lower to the later planned-perezhuvalnoy SRT.
When combining the system of technical services, "young people see TO" are carried out in the world of need, as for the TE camp, they go to the minds of a specific type of SVT or the results of yoga testing. Vikonannya "senior types of TO" and repairs are planned.
Rational organization of the STO can transfer the accumulated static material for the results of the operation of the SVT with the method of yogo aggregation, analysis and variation of the recommendations to thoroughly improve the structure of the service, improve the efficiency of the operation of the SVT, and reduce the cost of the
Transfer of the necessary material and technical aids for organizing and carrying out work from TO SVT
The level of operation of the SVT is to be stored in the form of provision with spare parts, various attachments of stained glass materials, provision of control and monitoring accessories, tools, etc. etc.) and for service personnel (climate wash, noise level, lightness is thin).
The operation of the SVT can be carefully planned. Planuvannya can shove all the food, which is like folding the main programs of the SVT robots, rozpodіl machine hour too soon, so it is up to all the robots of the service personnel.
The rational organization of the operation is responsible for transferring the accumulated static material for the results of the operation of the SVT with the method of further aggregation, analysis and the development of recommendations for a thorough service structure, promotion of the efficiency of the operational costs of the SVT,
Diagnostic programs
For PC, there are a few types of diagnostic programs (working with them at the same time with the computer), which allows you to quickly reveal the causes of problems that are blamed on the computer. Diagnostic programs that can be installed in a PC can be divided into three equal parts:
- Diagnostic software BIOS - POST (Power-OnSelfTest-procedure self-verification when enabled). Vikonuetsya with skin upgraded computer.
- Diagnostic programs of the Windows operating system are supplied with a large number of diagnostic programs for rechecking various computer components.
- Diagnostic programs of firms - diagnostic tools.
- Diagnostic programs of ignorant recognition. Such programs, which provide relay testing for any PC-smart computers, release a lot of companies.
Power-on self-test (POST)
POST-sequence of short subroutines that are saved from the ROM BIOS on the system board. The stench is recognized for re-verification of the main components of the system, once again, because it is turned on, so, well, it is the cause of the blockage before the interference of the operating system.
When the skin computer is turned on, the re-verification of the main components is automatically checked:
- processor,
- ROM chips,
- additional elements of the system board,
- operational memory and the main peripheral outbuildings.
Qi tests vykonuyutsya shvidko that not really relativly when a faulty component is detected, there is a warning or a warning about a pardon (incorrectness). Such inaccuracies are sometimes called fatal pardons (fatalerror). The POST procedure beeps for three ways to indicate a fault:
- sound signals,
- reminders of what to display on the monitor screen,
- sixteenth code of pardons, which are seen in the I/O port.
When a malfunction is detected by the POST procedure, the computer sees characteristic sound signals, after which the faulty element (or its group) can be identified. As the computer is in charge, you will feel one short beep at the next hour; As if an incompatibility was revealed, one can see a series of short chimes of sound signals, which are different combinations. The nature of the sound codes depends on the BIOS version and the company that you have developed.
For most PC-crazy models, the POST procedure is displayed on the screen of the process of testing the computer's RAM. As soon as the POST procedure has passed, an error has been detected, the screen will display an additional message, as a rule, it looks like a numeric code with a number of digits, for example: 1790-Disk 0 Error. Having speeded up as a helper for the operation of that service, you can determine if there is an error in your code. Cody pardons, which are seen by the POST procedure at the I/O port
Smaller options for the procedure are those that, on the cob of the skin test for the address of the special input-output port POST, see the code for the test, so you can read only for the help of installing the roses and expanding the special adapter board. The POST board is installed in the expansion roses. At the moment of completion of the POST procedure, two-digit sixteen numbers are changed on the second indicator. If the computer cannot be pinned to the test, or it is “hanging”, which indicator will show the code to the test, at which time the test will become bad. Tse permits the sound of the call to the joke of the wrong element. Most computers have POST code to I/O port 80h
Diagnostic software of the operating system
Warehouse OS DOS and Windows є kіlka diagnostic programs. Yakі take care of vikonannya testing warehouse parts SVT. Modern diagnostic programs create graphic shells and enter the warehouse of the operating system. Such programs are, for example:
- disk cleanup utility for non-essential files;
- a utility for rechecking a disk for the presence of pardons;
- defragmentation utility for files and free space;
- data archiving utility;
- file system conversion utility.
All listed programs in Windows
Diagnostic programs of firms - diagnostic tools
Virus collectors produce specialized programs for diagnosing a particular disease, a specific worm specialist. You can see the following groups of programs:
- Programs for diagnostics of hardware security
- SCSI Attachment Diagnostic Software
- Software for diagnostics of merging adapters
Diagnostic programs of general and special recognition
Most test programs can be run in batch mode, which allows you to run a whole series of tests without using an operator. You can put together an automated diagnostics program that is more effective in that case, so you need to detect defects and or to check the same sequence of tests on multiple computers.
The programs override all types of system memory: main (base), expanded (expanded) and extended. The fault point can most often be pinpointed to the exact IC chip of the module (SIMM chi DIMM)
There are no such programs. Tsey view software can be divided into following categories:
- information programs;
- Test programs;
- Universal programs
Information programs
Vykoristovuyutsya in situations, if it is necessary to fix the report configuration and maximally protest the computer for work, do not disassemble the system unit, or if at first glance everything works fine, but it is hard to make sure that the computer is constantly glitching and starting up every other time. But after the repair, for example, replace the electrical capacitors with maternity pay, it is necessary to carry out a relay diagnostics to check if the computer is working normally. They test the computer or its components, and see the report information about the yoga state, functionality, and possible software and physical problems.
Test programs
Follow the principle of maximum engagement with various operations, which emulate the robotic work of the computer, and measure the overall productivity of the system, or the productivity of four components on the basis of correlation with the obvious data base.
Universal programs
The programs are divided into two categories of programs - informational and test. They allow not only to protest the PC, but to take get information about yoga components.
I use a copy of absolutely different versions of the program, but all the stench is oriented blamelessly on the vimiryuvannya productivity of the video system.
Before the launch of the program at the head window, please check the model of the video card and the characteristics of the monitor. For more detailed information, click on SystemInfo, where you can find out - processor model, cache size, directX version and other system information. The program has a choice of all or less than some tests. May all tests be carried out on both low and high levels of detail, which gives great accuracy. After the test, the program displays the result as a ball, as you can match with another computer. It goes without saying that the test of the video system cannot do without a critical focus on other components of the computer. If the computer ran into them during testing, then it’s better for everything, the main components are in order
Among the packages of service utilities, without a doubt, "the first among equals", is NortonUtilities, which is produced by Symantec and has grown up to the 2001 version.
The SystemInformation utility, which is included in the package, can be manually grouped by all the main components of the computer. Possibility of detailing information from various divisions, and to form a call. To finish that barvisto at night, with circle diagrams, the information about the efficiency of that disc is framed. You can protest the processor by pressing the Benchmark button. The program sees the schedule of the smart code of your system; Intel processor 386SX-16MHz.
Service equipment
To search for faults and repair a PC, you need special tools, which allow you to detect problems and fix them just that fast.
To lie before them:
- a set of tools for sorting and folding;
- chemical preparations (rozchin for wiping contacts), a spray bottle with a cooling pad and a spray can with squeezed gas (povіtryam) for cleaning computer parts;
- collection of tampons for wiping contacts;
- special hand tools (for example, tools, necessary replacement of microcircuits (chips));
- Service equipment.
Service equipment is a set of attachments, specially designed for diagnostics, testing and repair of SVT. Service equipment includes the following elements:
- Vimіryuvalnі prilada testі roz'єmi for pervіrki poslіdovnіh and parallel portіv;
- add-on memory test that allows you to evaluate the functioning of SIMM modules, DIP chips and other memory modules;
- possession for testing the block of life of the computer;
- diagnostic add-on and software for testing computer components (hardware-software complexes).
Testing accessories and test roses for rechecking PC ports
For re-checking and repairing a PC, the following accessories are needed:
- digital multimeter;
- logical probes;
- generators of single impulses for rechecking digital circuits
Test roses ensure re-verification on the software and hardware ports of the PC input and output (parallel and subsequent).
Possibilities for testing the computer's life block for the safety of testing the PC's life blocks and their main characteristics. It is a set of equivalent vanishings, switching elements and simplistic fittings.
2.3. Description of the control, diagnostics and implementation of the implementation of computer systems and complexes
Analysis of the malfunctions of the "SamsungML-1210"
The printer does not accept paper. The problem with the roller is choking. It is necessary to carry out preventive maintenance.
Technical description Samsung ML-1210
Main characteristics:
- Druku technology - laser (Electrography);
- Freshness to each other - 12 PPM (sides for the quill);
- toner saving mode up to 30%;
- Razdіlna zdatnіst - 600 × 600 dpi;
- Hard 66 MHz processor;
- Repeating the rest of the arkush to the onslaught of one button;
- Sumіsnіst (Linux, Macintosh, Windows).
Other characteristics:
- Tray (cassette) - 150 arches;
- Viewing tray - 100 arches;
- Paper format - Letter, legal, Monarch, com 10, C5, DL, A4, A5, B5;
- Interface - USB, IEEE 1284 (parallel);
- Processor - 66 MHz;
- Memory (MB) - 8 MB;
- Working cycle (storinok per month) - 12000;
- Operating systems that are supported - Windows 95/98/2000/Me/NT, Linux (Redhat 6.0), Macintosh OS 8.0 and later;
- Emulation - Smart GDI;
- Toner cartridge - single cartridge: 2500 sides, at 5% fill, 1000 starter.
- Pressure (W):
- In the scoring mode - 5;
- For the friend regime - 180;
- Hour of drawing (sec.) - 25;
- First side exit (sec.) - 13;
- Noise ratio (max., dB) - 47;
- Fonts - Fonts Windows;
- Rozmir (W × D × H) mm - 329 × 355 × 231;
- Printer wagon - 6.2 kg.
Establishing the causes of malfunctions and failures in SamsungML-1210
The front cover is opened, 2 screws are screwed.
Screw 4 self-tapping screws in the back.
The back wall is lifted, the upper lid is lifted, the papers are directly removed and the side walls are lifted.
3 screws are twisted to trim the laser. There are 2 roses visible, which are located on the sides. Wipe with a wadded stick or clean with a piece of ganchirka.
It spins, in the air, the roller is choked up, like trimming 2 screws, and cleaning with a special motherland. At the same time clean up the galmivny maidanchik. Vaughn is known in the apparatus under the roller zahoplennya.
Let's clean the printer itself. This operation may be completed by a blower or by a compressor.
Folding is in order.
2.4. Iyavlennya nedolіkіv systems zabezpechennya staї robo-computer systems and complexes. Propositions for a thorough given system
Nedolіkom tsієї organіzаtsіїє є schedule tehnicheskogo obslugovuvannya PC і peripheral statkuvannya. At the link with the cim, it was proponated and it was split up on the given schedule
Chapter 3. Description of the information system that the organization has
3.1 Analysis of the object gallery for the information system
Students, organized into groups, study for one of the specialties. The initial process takes the fate of vikladachi. The initial process is regulated by the initial plan, according to the number of years assigned for skin discipline and form control (salіk, іspit). A vikladach can conduct employment in one of several disciplines.
3.2 Analysis / development of the structure of the information system
This small piece shows the structural diagram of the program, which means that the document is taken from documents.
Diagram of precedents (diagram of variants of variation) in UML is a diagram that shows the difference between actors and precedents and warehouse model of precedents, which allows describing the system on a conceptual level.
Precedent - the possibility of modeling the system (part of its functionality), zavdyaky koristuvach can take a specific, vimirny and necessary result. Precedent in vіdpovidaє okremі servіs system, vyznaє one іz variantіv її vikoristannya and vyznaє typical sposіb vzaєmodії koristuvachа s system. Variants of vikoristanny call zastosovuyutsya for the specifics of zvnіshnіh vimog to the system .
3.3 Description of database management system/software to be developed for distribution
The software system "1C: Enterprise 8" includes a platform and application solutions, expanded on a single basis, for automating the activities of organizations and private businesses. The platform itself is not a software product for using end-to-end coristes, as it works with one of the rich application solutions (configurations) developed on this platform. Such a pidhid allows you to automate various types of activities, vicarious and a single technological platform.
3.4. Instructions for employees for work with an information system
3.4.1 Assigned programs
The program allows:
- on the basis of the introduction of data, you can look through the information.
- zdiyasnyuvati avtomatizatsii vіdbіr nebkhіdnoї іnformatsії.
- form and display other documents for registration and zvіtni forms.
program benefits « information system of automatic admission”:
- durability and ease of use;
- small amount of memory on hdd;
- prompt service
Functional recognition
- the ability to independently shape the appearance by the method within the framework of the adjustment of the appearance policy and the adjustment of the parameters of the appearance;
- a sufficient structure for the code of the rachunks allows you to win a long code of the rachunks (subrachunks) and to conduct a rich plan of the rachunks with a great investment;
- mozhlivist work with kіlkom plans rahunkіv allows the appearance of a number of systems of appearance;
- to avenge vbudovaniy mehanizm vednya kіlkіsny and currency;
- on a be-yak rahunka one can lead a rich and rich analytical appearance;
- koristuvach can independently create new vidi subconto, add rahunki and subrahunki;
- state operations appear in the form mainly for additional input of documents in the configuration, identical to the primary documents of the bookmark, it is possible to enter all the postings manually;
- in the case of state operations on the documents of the change, it is clearly possible to show accounts of the accounting and taxable form;
- zastosovuvana accounting method for the safe one-hour registration of the skin record of the state's operation, both for accountants of the accounting form, and for the necessary analyzes of the analytical form, the bank account and the currency form;
Operational recognition
The program can be operated on enterprises oriented to the automotive industry, and the passenger transportation itself.
Coristuvach programs are responsible for auto-production practices.
Warehouse of functions
The program ensures the ability to hover below functions:
- functions for creating a new (empty) file;
- functions of viewing (capturing) a given file;
- appearance of material and virobnicheskikh reserves;
- warehouse appearance;
- appearance of trading operations;
- appearance of commission trade;
- form of agency agreements;
- form of operations from containers;
- appearance of banking and cash transactions;
- appearance of rozrahunkiv from contractors;
- appearance of the main assets and intangible assets;
- appearance of the main and additional virobnitstv;
- appearance of beverage products;
- appearance of indirect vitrates;
- appearance of pdv;
- appearance of wages, personnel and personification appearance;
- giveaway appearance from a tax on surplus;
- the system of podatkuvannya is simplified;
- the form of activity, as a single tax on the provision of income;
- form of income and vitrate of individual entrepreneurs - payers of personal income tax;
3.4.2 Clean up the software
Climatic minds of the exploitation, for some faults, the tasks of the characteristics are taken care of, the satisfaction of the helpers to the technical needs of the part of the minds of their exploitation is the fault.
Minimum warehouse for technical equipment
The warehouse of technical zabіv is responsible for the IBM-bag personal computer (PEOM), which includes:
- processor Pentium-1000 clock frequency, GHz - 10, not less;
- motherboard with FSB, GHz - 5, less;
- operative memory is limited, GB - 2, less;
Minimum warehouse of software products
System software programs, which are victorious by the program, may be represented by a licensed localized version of the operating system. It is allowed to change the update package 8.3.5.1284.
3.4.3 Programming
Launching the program
The launch of the program is performed by clicking the left button of the mouse on the shortcut of the program "1C: Enterprise 8.3", then it is necessary to select the configuration "Base ІСВ" and click "Configurator". At the same time, the choice is presented to the baby 1.
Figure 1 - Launching the information base
After launch software module in the “1C: Enterprise 8.3” system, “1C: Enterprise 8.3 System Operation” appears on the screen, in the new menu, that toolbar appears to be reversed short, it looks like this: the system operation window is presented in small 2.
Figure 2 - External view of the configuration menu
Robot from the menu
The entire menu can be divided into:
- menu "File";
- menu "Edit";
- menu "Configuration";
- menu "Natural";
- menu "Administration",
- menu "Service",
- menu "Vikna",
- menu "Documentation"
You can choose the main editing and editing of the document, starting with the creation of the new document, before establishing access rights to the information base. It is also possible to improve the interface of the singing coristuvach with the help of the advanced program for making the work easier.
The main menu is the “Configuration” menu, but the structure of the information base is created for the new one. Skin object configuration may have a unique set of powers. This set of descriptions on the system equals and there can be no changes in the configuration process of the plant. The number of features of the configuration object is important to the recognition of the "1C: Enterprise" system.
The main power of any configuration object or name is the short name of the configuration object. When a new configuration object is created, it automatically assumes a mental name, which is composed of words that are assigned to the object, and numbers. The value of the name can be changed in the process of editing the authority of the configuration object, with which the system recognizes the uniqueness of the names. Im'a configuration object cannot be empty and used for 255 characters.
Acts of power to the entire set of powers, power objects of configuration, available for editing and can be so changed in the process of system configuration. The nature of the change and yoga between are also set only on a equal system. Fahivets, which is the configuration of the system, the purposeful change of the authorities of the object configuration can achieve the necessary behavior of the object at the hour of the robotic system.
3.4.4 Operator notification
Oskіlki program is not console (with interface command line), and with a graphical interface of a koristuvach, classic textual reminder do not transfer. Information about pardons is heard at the sight of the vicons on the working table. Served on little 3.

3.5 Description of the zaobіv, priyomіv vakhistu іnformatsiї pіd hr work z іnformatsіynoy system
1C: Acceptance increases the possibility of capturing / expanding the information base of a file. This mechanism of appointments is in front of us for taking away the image of the information base independently of the method of collecting data. For example, changing/viving the information base of a file can be changed to convert the file version to a client-server one.
Another mode of victorization is also for creating a backup copy of the information base, however, such an option for victorious copying may have a number of shortcomings. The main shortcoming of this method of creating a backup copy is the need to use a single-source mode for the creation of a single operation. With a great obsyazі іnformatsiynoї base break in robots coristuvachіv can be made great, but not always acceptable.
Depending on the variant of 1C: Submissions (file or client-server), you can recommend the following ways to create a backup copy of the information base:
1) If you choose the file option 1C: Enterprise 8, you can organize the process of creating a backup copy of the information base by simply copying the 1CV8.1CD file to the other directory or using different software for backup and updating data. Slord Ekravuvati, Shaho for slaughtering Tsіlіsnostі Ta Uzkazznosti Done Pіd Hour Copher Restaurant Kopії, Robot Corringer Maє Bethi Zabonene, Prothe Hour, Nefіdnia Sweeper Restaurant Kopіїsto Mensh, Nіzh Pіd Hour Vikristannya Vivanzhennya Informakinoji Basi File.
2) When choosing a client-server version of 1C: Enterprise 8, it is possible to create a backup copy of the information base by the DBMS. For example, SQL Server allows you to back up data at the same time, if the database is in a secured on a rich account mode and is available to all accounts.
Vykoristannya tsikh methods give the most accurate copy of the information base, which can be removed under the hour of victoriousness to the mode of acquisition / vivantage of the information base. For example, if the data base is damaged, then when the data base is restored, the information may not be vivantage, in that hour, when copying, all the information will be saved, and after the update, it will be possible to correct the correct data base.
Also, the hour of the information base in the single-file mode changes in the case of the file version of the work 1C: Enterprise 8, and in the case of the client-server version, the single-file mode does not change.
The most positive moment is those that, with the help of reversed methods, it is possible to set up various specialized programs for creating backup copies.
Visnovok
For an hour of vocational practice directly 230000 Informatics and calculation technology for specialty 230113 Computer systems that complexes were vikonanі so zavdannya:
Formation and development of advanced and professional competencies in the sphere of the chosen specialty;
Nabuttya and the formation of the necessary mind, beginner and dosvidu practical work for the development of professional heads in the minds of a particular enterprise (organization) of the place and area;
- Organization of independent professional activity, socialization in a specific type of activity.
- Also, the results of virobnichoy practice directly 230000 Informatics and calculation technology for specialty 230113 Computer systems and complexes were developed such tasks:
- Consolidation, destruction of that expansion of otrimanih theoretical knowledge, reduce that skill;
- Ovolodinnya professional competencies, skills and new methods of practice;
- Encouragement by the norms of the profession in the motivational sphere: awareness of motives and spiritual values in the profession;
- Mastering the basics of the profession in the operational sphere: awareness and mastered methodology of the development of professional tasks (problems);
- Education of various aspects of professional activity: social, legal, psychological, hygienic, technical, technological, economic.
As a result of virobnichoy practice, the knowledge about the information system of philia was taken into account in the analysis of the structured knowledge of the working stations.
List of vicorists dzherel
1. Baidakov V., Dranishchev V, Krayushkin A, Kuznetsov I, Lavrov M, Monichev A. 1C: Enterprise 8.0 Description of the movie. [Text] /. In 4 volumes .- M .: Firm "1C", 2004. -2575 p.
2. Bilousov P.S., Ostroverkh A.V. Repair of working stations. [Text] / Practical help. - M.: TOV "1C-Publishing", 2008. -286 p.: Іl.
3. Gabets O.P. Rozvyazannya operational chiefs. Methodical materials of a listener of a certified course. [Text] / M: TOV "1C-Navchalny center No. 3", 2004. -116s.: il.
4. Gabets A. P., Goncharov D. I. All about PC design. [Text] / M: TOV "1C-Publishing", 2008. -286 p.: il.
5. Gabets A. P., Goncharov D. I., Kozirev D. V., Kukhlevsky D. S., Radchenko M. G. Professional development of the system 1C: Pіdpriєmstvo 8. - M .: TOV "1C-Publishing"; [Text] / St. Petersburg: Peter, 2007. - 808 p.: Il.
6. Gladky A. A. 1C: Undertaking 8.0. - St. Petersburg: [Text] / Triton, 2005. - 256 p.: Il.
7. Mitchkin S.A. Development of the system 1C Enterprise 8.0. [Text] / M.: TOV "1C-Publishing", 2003. - 413s. mule.
8. Pankratov, F.G. 1С: Pіdpriєmstvo [Electronic resource]: assistant / F.G. Pankrativ. - M.: Businesssoft, 2005. - 1 electron. opt. disc (CD-ROM).
9. Radchenko M.G. 1С: Pіdpriєmstvo 8.0. Practical help of a retailer. Apply that type of take. [Text] / M.:, TOV "1C-Publishing", 2004. -656 p.: Il.
10. Radchenko M.G. Repair of computers and peripherals. [Text] / M.:, TOV "1C-Publishing", St. Petersburg: Peter, 2007. -512 p.: Іl.
11. Russian State Library [Electronic resource]/Center of Information. RDB technologies; ed. Vlasenko T.V.; Web-master Kozlova N.V. - Electron, yes. - M.: Fig. holding b-ka, 1997. - Access mode: http://www.rsl.ru, vіlniy