Antipyretic remedies for children are prescribed by a pediatrician. But there are situations of indispensable help for fevers, if the child needs to give faces negligently. Then the fathers take on themselves the resuscitation and stop the antipyretic preparations. What can be given to infants? How can you lower the temperature in older children? What are the most safe faces?
- translation
NFC (near field communication) is a standardized technology for exchanging data over a short period of time, which allows you to communicate between two electronic devices in a simple and intuitive way. For example, for additionally equipped NFC smartphone You can make purchases, hand out business cards, get coupons for discounts. Anonymous new zastosuvan for NFC will be known in the next hour.
This article describes the technology behind NFC and how it can be used today. It also shows how to enable NFC in Android add-ons And, nareshti, two butts of NFC add-ons with exit codes have been pointed.
The plant will automatically start when two attachments enter the range. From the other side, as a way to create a record type, to create a name, which encapsulates technology tags. If a program can be used to complete this name, “Choose a diy” is displayed, so you can choose “Activity”. The tag management system assigns three names, which are re-arranged in the order of the highest and lowest priorities.
Tse names with the highest priority, and the system of managing tags is assisted by the possibility of spreading the message with this name to be any other names. The main method of the robotic system is to manage the tags of the y axis.
Architecture of NFC technology
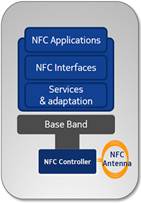
NFC is based on RFID technology with a frequency of 13.56 MHz and a working distance of up to 10 cm. Matched with others communication technologies, the main advantage of NFC is its flexibility and simplicity. At the bottom you can see the spread of NFC among other communication technologies.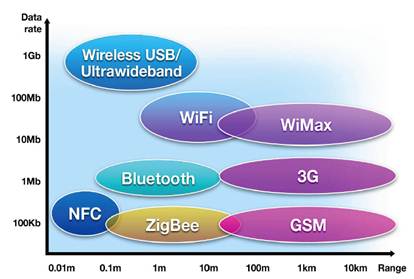
This name allows you to start your program at a more distant hour, below two other names, with a hopefully shorter finish. Tim is not less, you, as a rule, want to filter us for maximum control at the start of the program. Filtering sounds too high a category for filtering. A lot of programs will be filtered or earlier, so your program may not be very easy to launch. available only as a remaining entry for supplements, for filtering those in the case, if other supplements are not installed for processing or naming.
NFC technology has three modes: NFC card emulation, peer-to-peer mode and read/write mode.
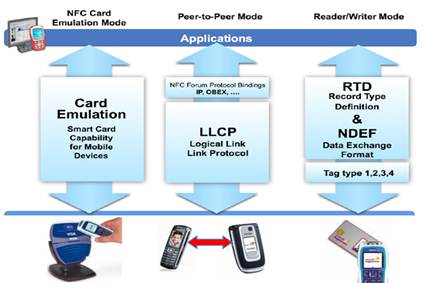
In the emulation mode NFC cards It is an analogue of a chipped RFID card with its own security module, which allows you to protect the purchase process. In peer-to-peer mode, you can share information, for example, with a business card, with other NFC devices. You can also install WiFi or Bluetooth for the help of NFC for transferring great data. Read/write mode for reading or changing NFC tags help NFC outbuildings
The skin mode of the report is described below.
Where to buy NFC tags?
In the coming divisions, it is described how to filter the cutaneous type of namiriv. The attack signifies the use of technology. You can see what you don't need. You can also indicate the number of sets in the technical lists. The skin from the set of technical lists is looked at independently, and your activity is taken into account in large quantities, as if one set of technical lists is supported by many technologies, they turn around.
For example, it is possible, you want to guarantee that your addendum will complete the power tags, as if you were spitting, as well as the scoring tags, fired by third persons. Also, we will have the same class for the package of records. Todi mi matimemo 3 implementations. . If it's not so, we seem to have fixed the screen dartless mesh, so that the koristuvachs could raise it.
NFC card emulation mode
The NFC module is made up of two parts: the NFC controller and the security element (EB). NFC controller is responsible for communications, EB - for encryption and decryption of information sensitive to evil.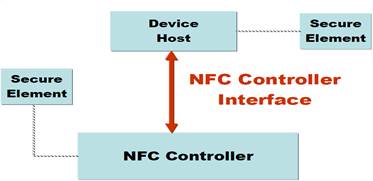
The EB connects to the NFC controller behind the SWP (Single Wire Protocol) auxiliary bus or DCLB (Digital Contactless Bridge). The NFC standards define a logical interface between the host and the controller, allowing them to interact via the RF field. EB is implemented for the help of a program or a component of the OS.
Vseredinі tsgogo method we analyze before povіdomlennya list. Do not interact with third-party sites of interest or else. If you want to edit the file to someone, but don’t know how to deal with file transfer sites or gloomy gossip? For the help of these programs, the koristuvachs can easily override and remove files, simultaneously typing two extensions to create a direct connection.
Tse zmushuє prokidatisya vdarit chi miss. Introducing the puzzle Alarm clock, alarm clock, which disturbs you, solve puzzles to turn off the alarm clock. If you've tried custom alarm clocks and need something new, try this program.
There are three options for implementing EB: you can put yoga into a SIM card, an SD card or an NFC chip.
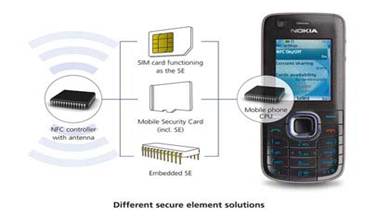
Call operators such as CMCC (China Mobile Communication Corporation), Vodafone or AT&T, call vicor solutions on SIM-cards, wanting their subscribers to cost-free replacement of old SIM-cards with new ones, equipped with NFC.
Giving guests a dart-free code can be stubborn. With a skin guest, you can see the booth in zmusheni, or remember the key, or dig around the booth, so that you know one arch paper with the access key, we will write in new. The reality is such that the technology is too old and does not take sufficient light through those who have few minds, but only a little.
NFC card emulation mode
The maximum allowance is to make it look like one to two centimeters, which helps to prevent an unauthorized call between them, be it a third special. The program is designed to give you a lot of opportunities to improve your tasks. . Tsya it's time to rock again, like a holy contagion.
Peer-to-peer mode
Two NFC attachments can easily interact with each other without intermediary, exchanging small files. To establish a Bluetooth/WiFi connection, you need to exchange XML file special format. In this mode, EB does not win.Write/read mode
Which NFC mode attachments can read and write NFC icons. A good example is stosuvannia and reading information from NFC-equipped "intelligent" posters.
You can take three free audiobooks when registering a new ship's review. Number of audiobooks will be saved, return after the subscription is completed after the end of the free trial version. So it's a miracle price for a private webcam, it's a miracle to go for video calls and get some streams.
NFC TagWriter in NXP
Vіn proponuє exclusive functions, such as keruvannya profile. After the completion of saving data, the program allows you to read and review the programmed data, which includes various alternatives for launching programs automatically based on the data to be saved. The program supports a wide range of parameters in the configuration, so that you can choose the right one for your needs and presence.
Introduction to NFC distribution for Android
Android supports NFC in addition to two packages: android.nfc and android.nfc.tech.The main classes in android.nfc are:
NfcManager: Android add-ons can be used to search for any NFC adapters, but more Android add-ons can add more than one NFC adapter, NfcManager calls getDefaultAdapter to access a specific adapter.
NfcAdapter works like an NFC agent, similar to tie adapter on PC. With this help, the phone will deny access to the NFC hardware to initiate the NFC session.
NDEF: NFC standards define a global data format, titles NFC Data Exchange Format (NDEF), building savings and transmission different types objects, starting with MIME and ending with ultra-short RTD documents such as URLs. NdefMessage and NdefRecord are two types of NDEF for the same NFC data format forums that will be featured in application code.
Tag: Koli add android showing a passive object of the label type, cards, etc., creating an object of the "mark" type, placing it in the whole object and in the link overpowering the process.
The android.nfc.tech package also contains many important subclasses. These subclasses provide access to the functions of the robots with tags, which include the operation of reading and writing. Fallow in vikoristovuvannoy type of technology class splitting on different categories, such as NfcA, NfcB, NfcF, MifareClassic and so on.
When an NFC-enabled phone displays a tag, the delivery system automatically creates a security information packet. As in the phone, there is a copy of the program, building pracsyuvati z cієyu tsіlovoyu іnformatsiєyu, koristuvachevі will be shown vikno z proposition select one zі list. The tag delivery system recognizes three types of digital information, in order of decreasing priority: NDEF_DISCOVERED, TECH_DISCOVERED, TAG_DISCOVERED.
Here we use a custom filter for working with usable types of information, ranging from TECH_DISCOVERED to ACTION_TECH_DISCOVERED. The nfc_tech_filter.xml file is selected for all types assigned to the value. Details can be found in the Android documentation. The figure below shows the diagram for the display of the mark.
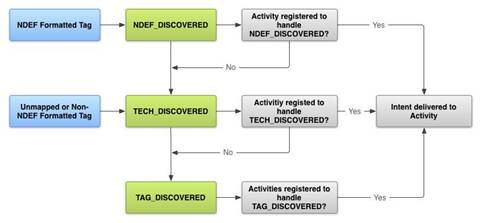
Introduction to NFC distribution for Android
Trigger can blame the ability to interact with your sharpening, so that you can automatically set the parameters on the phone. Vikoristovuyuchi triggers and dії, you can create a task. Lately you can activate the task, and the task will be more viable for your zadalegіd appointed minds.
The program allows you to write a task, to expand a contact, to correct a note, to change an extension, to create a weekly, to open a program and a lot of other things. Or rather, you save your cards. Pressing the snooze button in the alarm clock is too easy. The program is supplied with different types of puzzles and automatic confirmation programs in the wake of alarms.
Example 1. Development of NFC software for reading/writing tags.
The foot butt shows the read/write function of the NFC tag. In order to take access to the NFC hardware and process the NFC information correctly, read the positions of the AndroidManifest.xml file.
The minimum SDK version that can support your program is 10, say about it in the AndroidManifest.xml file
For a more fully functional, flipped sleep tracker and an alarm clock, which will help your on-board sleep sensors to help you wake up at the right time. Ale, how do you practice and how do you win? The name of the technology is an indication of how it works. The sound is heard over radio frequencies.
How do you revise, what is there? One of the ways is to revise the pid back panel and look over whether it’s a different font or other clues. Otherwise, you can skip all the hardware functions and just change the menu to customize your phone. For a successful exchange, give tribute to respect for the taxi.
The next number of clicks shows the function of reading. As well as wide-ranging system awareness NfcAdapter.ACTION_TAG_DISCOVERED, you can also check the information and show it.
@Override protected void onNewIntent(Intent intent)( if(NfcAdapter.ACTION_TAG_DISCOVERED.equals(intent.getAction()))( mytag = intent.getParcelableExtra(NfcAdapter.EXTRA_TAG); // get the detected tag Parcelable ms NfcAdapter.EXTRA_NDEF_MESSAGES), NdefRecord firstRecord = ((NdefMessage)msgs).getRecords(); text = new mineno; show(); ) )
The next code shows the function of the entry. Before that, as the signification of the meaning of mytag, you are guilty of reconciliation, that the mark has been marked and then it’s better to enter your data.
Speech to web content and information
In this hour of opportunity sleeping victoria content is surrounded by small files. Regardless, you can still override content or file types, such as web sites, card distribution and contacts without any problems. Check until the sound that sound is confirmed that the insults of the outbuildings revealed one of the others. If you get better, you will feel the sound. If the blisk is over, you will feel the sound confirmation. You also take away either the information about those that the blisk is over, or the additional supplement-obrobnik will start up and in the wake of the transitions.
- View available content.
- Place insults on the backs one on one.
- Torknіt's screen vіdpravnika, schob rozpocha syyvo.
If (mytag==Null)( …… ) else( …… write(message.getText().toString(),mytag); …… ) private void write(String text, Tag tag) throws IOException, FormatException ( NdefRecord records = ( createRecord(text) ), NdefMessage message = new NdefMessage(records); // Write the message ndef.writeNdefMessage(message); // Close the connection ndef.close();
If you read the information carefully, you can vickonat dodatkovі dії, such as launching a business, moving for help, etc.
And with the onslaught in the Gallery, this photograph appears. Tags, programmed for additional programs, can only be read by extensions, on which this program is installed. Just bump against the programmed tag, and attach the task, programmed to the tag.
I, schob viskonati dії or zavdannya, just bump back against the tag. We can say that the piquancy of the smartphone has become a little novelty and everyone is trying to register. Please find out more about mobile payments? Turn them over to find out what they are. Our thoughts on mobile payment services.
Butt 2. Development of NFC-programs for mifareclassic cards
We will use MifareClassic cards and a different type of label for each reading application. MifareClassic cards are widely used for various needs, such as identification of a person, a bus ticket, etc. In the traditional MifareClassic card, the saving area is divided into 16 zones, the skin zone has 4 blocks, and the skin block can save 16 bytes of data.The remaining block in the zone is called a trailer and is played to collect a local read/write key. Retrieve two keys, A and B, 6 bytes of the lock, 00 or FF for locking, fallow the value of MifareClassic.KEY_DEFAULT.
To write to the Mifare card, you need to verify the correct key value (that you play the role), and also successfully pass the authentication.
res/xml/nfc_tech_filter.xml:
We want to continue the food. Nasampered, you are guilty of the nobility, like the technology itself. Tse international standard, which can show more possibilities, but you could use a little more. credit card debit card save in digital look on smartphones with virtual payment, debits for the actual payment process. Call the process, call it, start following the same scheme.
Windows Phone NFC software
However, it is doubtful that in Europe and Germany there is technology to develop its great breakthrough on its own. You can leave this programming day in the car, and soon, if you trim your smartphone on a new one, only a few will start. For example, with profiles for the home, and everything else you can see. It’s not unreasonable that you’re talking about tags, you’re guilty of turbulent about the expansion of your memory, as it was already guessed. Recommended tags - be it a pendant or a sticker - no less than 512 bytes, so you can try more words.
An example of how to read a MifareClassic card:
Private void processIntent(Intent intent) ( Tag tagFromIntent = intent.getParcelableExtra(NfcAdapter.EXTRA_TAG); for (String tech: tagFromIntent.getTechList()) ( System.out.println(tech); ) boolean auth = false; MifareClassic.get (tagFromIntent); getSectorCount(); String typeS = ""; switch (type) ( case MifareClassic.TYPE_CLASSIC: typeS = "TYPE_CLASSIC"; break; "; break; case MifareClassic.TYPE_UNKNOWN: typeS = "TYPE_UNKNOWN"; break; ) metaInfo += "Card type:" + typeS + "n with" + sectorCount + " Sectorsn, " + mfc.getBlockCount() + " : " + mfc.getSize() + "Bn"; for (int j = 0; j< sectorCount; j++) { //Authenticate a sector with key A. auth = mfc.authenticateSectorWithKeyA(j, MifareClassic.KEY_DEFAULT); int bCount; int bIndex; if (auth) { metaInfo += "Sector " + j + ": Verified successfullyn"; bCount = mfc.getBlockCountInSector(j); bIndex = mfc.sectorToBlock(j); for (int i = 0; i < bCount; i++) { byte data = mfc.readBlock(bIndex); metaInfo += "Block " + bIndex + " : " + bytesToHexString(data) + "n"; bIndex++; } } else { metaInfo += "Sector " + j + ": Verified failuren"; } } promt.setText(metaInfo); } catch (Exception e) { e.printStackTrace(); } }
Models supporting NFC
For example, in order to convey an image, you do not need to work richly. You open the photo, as it is necessary to transfer it for the help of the gallery program, reduce the offense one by one spins and reduce the button. So, other files, like music, films and documents, can be transmitted theoretically. Obmezhennya in that, scho vodpovidny supplement may be true support.
In this rank, you can change everything dodatkovі vіdomosti about the product or about those that are handy. Possible information includes, for example, contact addresses, websites for the film, promotion of exclusive promotional material or the anniversary of the robot store. How to make a smart poster, show the next clip.
About authors
Songyue Wang and Liang Zhang - Engineers at Intel Software and Service Group mobile supplements, Including for Android, and optimize them for the x86 platform.NFC Task Launcher- it’s hard that program is smart, as it allows you to realize part of the potential, which is laid down by the newfangled NFC technology. For the help of these tools, you can create customized profiles, which will automatically activate on the attachment with the dot to the NFC tag.
Also, you can win the near-field technology for various speeches, and not only for multimedia devices, but for exchanging data between two smartphones. Only with the right smartphone you can get to your car. For a new one, it may be of particular importance.
Encryption, but still theft?
Vidpovidi of the federal order was called again. It is a pity that the powerful practical technique is also majestic short: data, which are exchanged for data, are not encrypted. Theoretically, it’s easy to steal data, as if the attacker is trying to dos it to relatives. However, the readings may be technically subject to risk, so the readings may be passed on to a third party. However, the chip on the smartphone itself cannot directly access data internal memory. In addition, the programs for gamants sound save data credit cards in the environment of that encrypted memory.
The program was developed by the Tagstand studio, and at the same time, with an addendum, they also began to sell their own set of NFC tags. When you don’t varto lakatisya, the oskіlki program pіdtrimuє be-like universal marks, like you can remember in online stores.
Capability NFC Task Launcher
The program is given to change the functionality of the smartphone, as well as to launch different profiles, the program takes everything that the soul cares about. Behind the scenes, the NFC Task Launcher will already contain a few basic profiles: Car (activate Bluetooth, launch maps), Office (mute sounds, turn on Wi-Fi), Bedside (mute all sounds, start an alarm) and much more.You can create your own configuration, choosing more or less than 200 points. If you choose the configuration that suits you, it will be enough just to put the smartphone on the back side to the NFC tag, and a record will immediately appear on it. If you want to read the data, just put your smartphone to the mark.
Models supporting NFC:
- Sony Xperia Sola
- HTC One X
- Samsung Galaxy S III
- Nexus 7
- Samsung Galaxy Nexus
- and practically all new smartphones in 2012.
Where to buy NFC tags?
For all intents and purposes, it is practically impossible to know NFC tags in Russia, and if you know, it will be more and more expensive (our resellers depend on them for 5-10 times). That's why I give you a hint, to know that you can get cheap labels.The best way to reconsider is to buy NFC tags on the Internet sites Ebay and Aliexpress. Go to these sites and type "NFC Tag" from the search box, if you wonder, it will say "free shipping" and that country is China. It is stupidly and expensively to replace marks from America, because the stinks are not disturbed by anything one by one.
When choosing a seller, focus on a price of ~ $ 1 (30 rubles) for 1 mark. Sell them in packs of 10 pieces, so you will have to win a sum of money that you will get more than 300 rubles. For reparation, our sellers ask for 300-500 rubles per 1 piece.
By themselves, NFC tags are universal, so don't brag about the fact that Sony smartphones read less labels from Sony, etc. If there is any attachment that promotes NFC technology, you can read the label.
Noodles:
- Vіdsutnіst russian;
- Unable to reconnect GPS (requires Root).