Antipyretic remedies for children are prescribed by a pediatrician. But there are situations of indispensable help for fevers, if the child needs to give faces negligently. Then the fathers take on themselves the resuscitation and stop the antipyretic preparations. What can be given to infants? How can you lower the temperature in older children? What are the most safe faces?
Apparently, Apple add-ons allow two-way authorization. This method of security vikonu prinaimnі dvі reverification during authentication - password and trusted attachment - for access to oblіkovogo record.
Dvokrokova, or as they call it, two-factor authentication (2FA) secures the security of data protection, the keys for passing through require not only the knowledge of the password, but also physical access to one of the keys, in our case, the iPhone or the iPad.
You don't need to say, we recommend that you win on any account, on whatever it is possible. Moreover, if the service does not support 2FA, then you should think, first of all, to respect it, as the security of your data is important to you.
If two-way authentication is enabled on your Apple ID (which, in a good way, would be required to be robbed), then you, more than anything, zustrichalis z vіknom, like asking you to confirm that you are a vlasnik given oblіkovogo record. On which screen can you list some of your Apple Appliances i want one certified telephone number. Qi attachments act as access keys.
Have you ever chirped, yakі might be guilty of satisfying the attachment to the list? Chi, mozhlivo, it was necessary to add chi to remove additions from this list? Here is a tutorial on how to manage trusted attachments for 2FA.
How to add trust
To add an attachment as one of the authentication keys, you just need to turn on the Know iPhone service on your iPhone, iPad or iPod Touch. As soon as you increase the function, the attachment will automatically reach the list of trusted ones. If you need it, you will need to confirm the addition of the building.
Krok 1: Sign in to iCloud and enable the service Find My iPhone on an add-on that you need to trust by setting up > iCloud.
Krok 2: For Safari, sign in to My Apple ID, go to Password and Security >


Krok 4: On all attachments, you will receive a confirmation code.
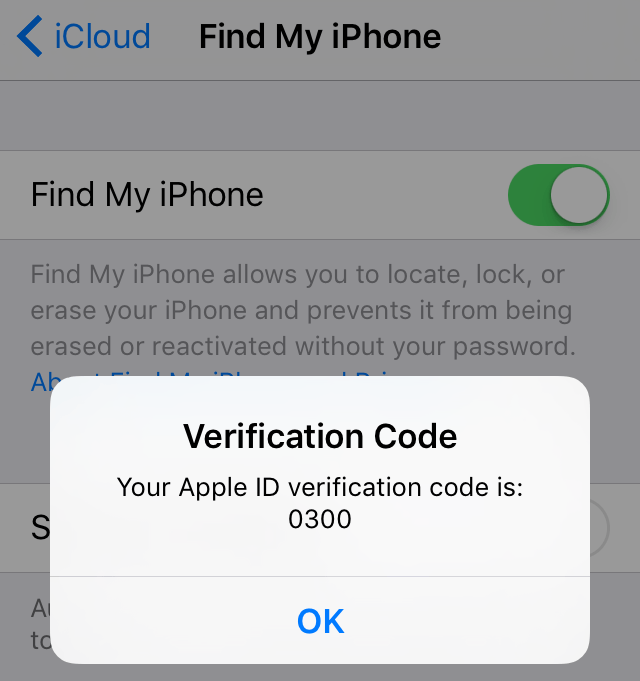
Enter the code in the field that appeared in Safari, and press Confirm Appendices.

Now you can reconsider that you attach verifications like trusts. Now, if you need to speed up two-way authentication for logging in to Apple ID, you can twist this attachment like a key.
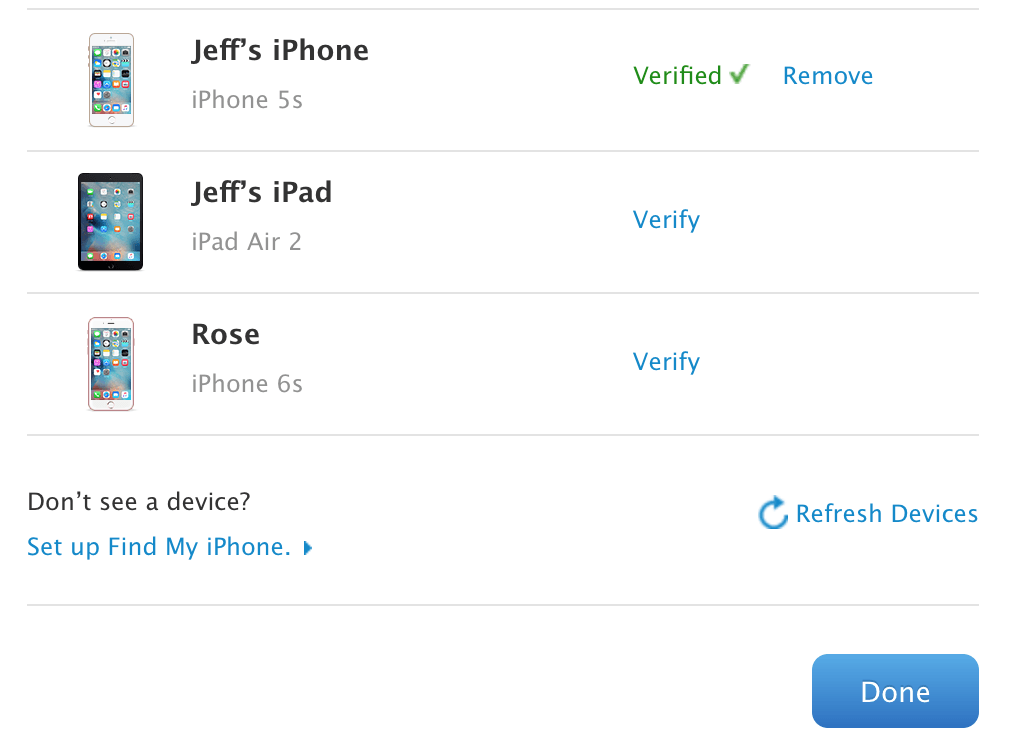
How to remove trusts
It is not surprising that the annex can also be seen from the list of trustees. If you sign out of iCloud or turn on Know iPhone, you will no longer be trusted, but everything else will appear in the list as you can trust.
Krok 1: Turn off the Know iPhone feature.
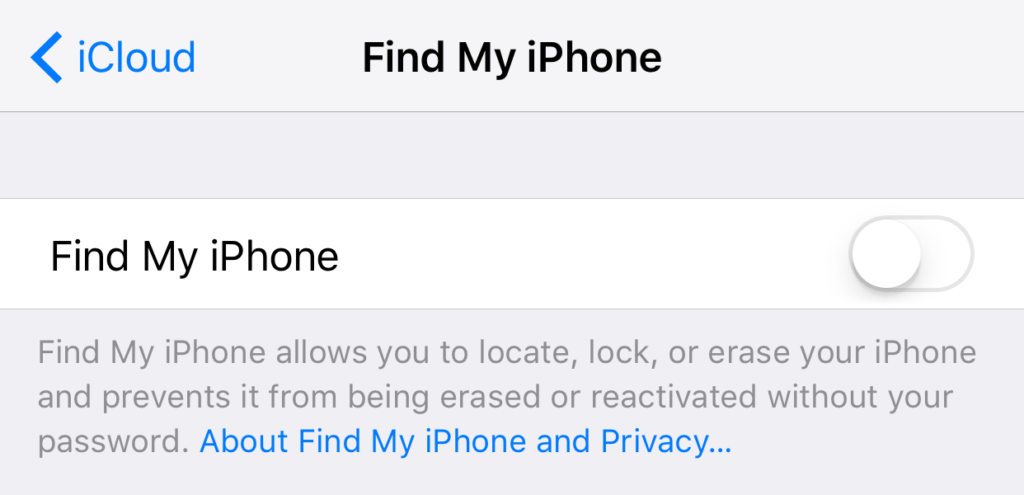
Krok 2: In Safari, call My Apple ID, go to Password and Security > Add or Remove Trusted Attachments.


Confirm the date.

Axis, zagalom, and that's all. With such a simple rank, they are given and they are allowed to trust the attachment for two-to-one identification. You will often work with this list, especially if you like to go out of public records and win different devices.
To access Apple's proprietary services, such as iCloud, App Store, iMessage, Facetime, etc. The corresponding iOS device requires special physical records of Apple ID naming. This public record is formed from the login - as a new address of the electronic screen, to which binding identifier and password, which is set by the security system.
At first glance, it seems that there is enough of such a classic login + password, but it’s not worth it. I really privid for a fight є. Think for yourself, the recognition of an e-mail address in our hour is bad on the right - we are flooded literally skrіz. With a password, it’s not so easy to get it right - there are different hacker programs that allow you to pick up secret code, today is rich.
Razumіyuchi tsey sumny razdelka Apple propagated a new type of zahistu: for koristuvachi old i-appliances, which can not upgrade to iOS 9 - a two-step reverb, for those who were spared by the younger "apple" mother - two-factor authentication.
In spite of insults, the ways of defending are even more similar, the stench is allowed, after entering the login and the password of the identifier, the coristuvach is guilty of entering the same special code. In this article, it is possible that this is the Apple ID verification code, where you enter this code and how to enable two-step verification / two-factor authentication for your device.
Two-stage re-verification
Otzhe, what is a double-tap perevіrka? Tse dodatkovyy zahіd zahistu access to firms Apple services- as you can see the double-entry check, the attacker will not be able to log in to that other i-service, navigate to that situation, if you know the login and password of your special identifier. You will need another special code for access.
Zokrema, two-step verification protects when trying an unauthorized login to the Apple ID page, in iMessage, FaceTime, all services for buying content, as well as for the gloomy iCloud service - which is especially important, even if the attacker leans against your "hmar", it's not true. access to all your personal data, as well as backup, and also, for example, block your iOS device by turning on the login mode and charge pennies for unlocking.
How to fix a two-step reverb?
In order to vikonate the inclusion of a two-stage re-verification, it is necessary to speed up with this clumsy helper:
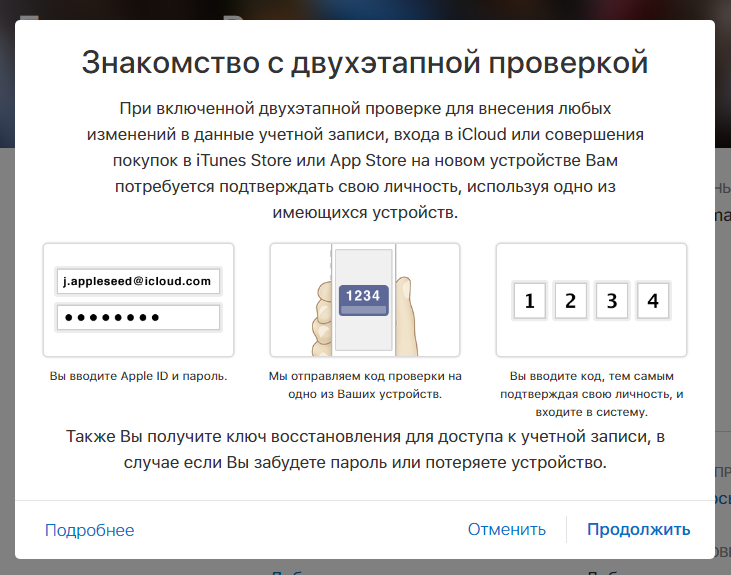
Ready! Rewiring is activated. Now try to go, for example, to your special office on iCloud.com, after entering your login and password, you will be asked to enter a code in a special window, in order to send directions to your trusted gadgets. If the code is not entered, access will be blocked, regardless of those who know the login and password.
Important moment! The most recent scheme is the variant of trusting the smartphone of a twisted individual and the axis of what. Tell them your iPhone was stolen, your Apple ID was found out and they try to log in to iCloud to check everything else confidential information. As if, as a trust, you indicated the phone number of your iPhone, which was stolen, then the attackers can easily take away the verification code and bypass the double verification. How can a code come to another accessory - shahrai will be able to recognize it on a yak and steal it like that.
How to turn off the double-tap reverb?
For some reason, you care that such a folding type of access to company services is no longer in your power, you can definitely turn it on, for which:
- Go for sim pleas and see to the special office Apple patching ID, enter the password and login of the special oblikovy record.
- Click the "Security" menu, give "Change".
- Select the option “Turn on the double-tap reverb”.
- In the coming future, you will be asked to indicate your date of birth and conversion food - after you enter these parameters, you can only renew your password to log in to all i-services, but when you enter the special account of the management of Apple ID, you also need respond to qi supply.
Information about the successful inclusion of a two-stage recheck will come to the post office.
Two-factor authentication
Two-factor authentication, like a two-step verification - ce additional entrance to the entrance to the company's Apple service. Only in the situation of working with two-factor authentication, the mechanisms of security security seem to be thought out and thorough, as if to believe the "apple" giant.
How to set up two-factor authentication?
As we have already said above, two-factor authentication is an option that is not available to all core users, but to those who are lucky enough to use mobile i-devices on board iOS 9 and the latest versions of the platform. Does your gadget please you? Let's tell you how to enable authentication:
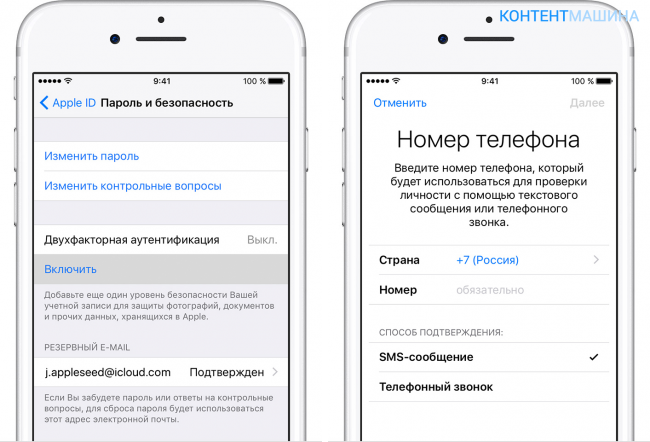
From i all! We activated the defenders, now it’s necessary to apply yogo:
- At a later date, as soon as the activation of authentication appears, enter a trusted phone number and that is a convenient way for you to override the code.
- Get the code for the order number.
- Tap "Enable ...".
Ready! Activation protector. Die won for the principle of two-stage re-verification - if you try to go to that chi іnsha Apple service, you need to enter as a login and a secret ID cipher, and a special conversion code.
Mac controllers can activate two-factor authentication using the simple instructions below:
- Click the “Apple” menu, go to “System Settings” / “iCloud” / “Cloud Recording”.
- We choose the "Safety" section, click "Enable ..."
Important! Your Mac may have OS El Capitan installed or the latest version of the platform.
How to disable two-factor authentication?
Instead, the “apple” giant categorically does not recommend turning on the lock, but if you don’t want to, you will need to go to the Apple ID management side, enter your login, password and verification code, and then in the “Security” submenu, select “Edit” / “Turn off ... ".
Two-stage verification and two-factor authentication: what is the difference?
A respected reader could not help but have a power - as the robot of the Apple ID security systems is so similar, then why is it authorized and why the authentication is stunned by a more thorough mechanism of security security. Seemingly at the door, there is no direct evidence of food.

Apple itself on the official side of the pidtrimka says something like this. Two-factor authentication has been started - the service of the defender has been updated, as the victorists have more perfected the methods for managing the verification of the outbuildings and the confirmation code extension, and the robot has also been optimized by the call.
Tobto, like a bachite, the knowledge was indicated, the prote did not clearly understand anything. From now on, trust the company and in that case, as your attachment supports two-factor authentication, choose the same type of zahistu. When it is important to designate, before activation this type it is necessary to turn on the back of the head with a two-step re-check, as if she was taken out.
Probably
Well, now you know that such a two-step reverification and two-factor authentication, how to add ts options and cherub them. In addition, you see the importance of activating these defense mechanisms. You can read a report about two-step verification and two-factor authentication in the “Pidtrimka” section of the Apple website.
Two-factor authentication - ce additional riven Apple ID security, which guarantees that you can only remember access to your personal account, you can only remember the password for anyone else.
How does it work
With more than one two-factor authentication, access to the cloud record is only possible with the trusted devices of the iPhone, iPad or Mac. When you first log in to a new extension, you will need two types of information: a password and a six-digit numeric verification code that is automatically generated on trusted extensions. After entering the code, new attachments are switched on before trusted attachments. For example, if you have an iPhone attached, the first time you log in to the hard drive on your newly attached Mac, you will be prompted to enter a passcode and verification code that will automatically appear on the screen of your iPhone.
Skills for access to a public record with two-factor identification, it is not enough to know the password, the security of your Apple ID and the data that is stored on Apple servers is growing.
Once the login code has been confirmed, the confirmation code will no longer be requested on this extension, the docks will not be re-signed, all data on the extension will not be erased, or until it is necessary to change the password for security mirroring. If you log in via the Internet, you can specify that the browser is trusted, and the next time you log in from this computer, the confirmation code will not be asked.
Refurbishment of outbuildings
We can change the device, either iPhone, iPad or iPod touch with iOS 9 or a later version or a Mac with OS X El Capitan or a later version, any system will be allowed to log in with two-factor authentication. Tse attachments, for which we know it belongs to you, and which can be vikoristovuvat for reverification of the special way to the Apple confirmation code at the entrance to another attachment or browser.
Checked phone numbers
Phone number – this is the number that can be selected for retrieval of confirmation codes for additional text alerts or automatic telephone calls. It is necessary to verify at least one trusted phone number in order for the mother to have access to two-factor authentication.
Also, look at the option of confirming other trusted numbers, to which you can gain access, for example home phone or a number, which is a victorious member of this family or a close friend. Number of rooms can be changed, as it is time-to-hours daily access to the upper buildings.
The verification code depends on what you enter to unlock your iPhone, iPad and iPod touch.
Setting up two-factor authentication for Apple ID
Two-factor authentication is currently available to iCloud owners who have iOS 9 or OS X El Capitan or the latest version on the same device. .
To improve two-factor authentication, you can iPhone add-ons, iPad or iPod touch.


Increased two-factor authentication at the Nalashtuvannya branch
If the add-on is running iOS 10.3 or a newer version, hover below.
- Go to the “Settings” > [your name] > “Password and Security” section.
- Press "Continue".
If the add-on is running iOS 10.2 or earlier, hover below.
- Open the Preferences menu > iCloud.
- Select Apple ID > Security Password.
- Press "Enable two-factor authentication".
- Press "Continue".
It is possible that you will need to verify your Apple ID power supply.


Entering and confirming a trusted phone number
Specify the phone number for which it is necessary to use the verification code when entering the system. You can use the code to view text alerts or automatic phone calls.
Enter the verification code to confirm the phone number and add two-factor authentication.
On a Mac computer with OS X El Capitan operating system or later versions, please follow these steps.

- Navigate to Apple Menu > System Settings > iCloud > Cloud Recording.
- Click the Bezpeka icon.
- Click on the "Enable two-factor authentication" button.
Apple IDs created in iOS 10.3 or macOS 10.12.4 and newer versions protected by default two-factor authentication. Which one will have two-factor authentication enabled.
How do you victorious double-tap re-verification and want to raise the security ribbing, .
Since you cannot enable two-factor authentication for your public record, you can protect your information.
What is the next memory when vikoristanny two-factor authentication
Two-factor authentication is a powerful way to protect Apple ID. After you have entered this function, you will need a password to access the oblіkovogo record, and access to the conversion of extensions or phone numbers. In order to secure the maximum protection of your oblique record and permanent access, there are a few simple recommendations that you need to do:
- Remember your apple password ID.
- Enter the password code for all your appliances.
- Update your revised phone numbers hourly.
- Take care of the physical safety of overturned outbuildings.
Post record management
You can use your phone numbers, revise the outbuildings and other information about the physical record on.
Timely updating of phone numbers
To win two-factor authentication, you need to be present at the database if you want one verified phone number, to which you can use the verification code. To update the phone numbers, hover below.
- Go to the “Safety” section and click “Edit”.
If you need to add a phone number, click "Add a phone number, which you have verified", and enter a phone number. Choose a way to confirm the number (textual confirmation or automatic dialing) and press "Continue". To see the reverification of the phone number, to type in the order of the phone number, which you need to see.
Revisiting the outbuildings and turning them around
You can look at the list of revised extensions and check them at the "Attachments" branch of the Apple ID registration page.
- Go to the side of your appearance Apple records ID.
- Sign in with your Apple ID.
- Go to the "Pristroy" branch.
Creation of passwords for programs
It takes an hour to use two-factor authentication to log in to a public account with third-party programs, services, for example, programs for work with e-mail, contacts or calendars, rozroblenny not by Apple, it is necessary. To create a password for the program, hover below.
- View on the side of the Apple ID public record.
- Press the "Create password" button at the "Program passwords" branch.
- Watch the quotes on the screen.
After creating a password for the program, enter it, or insert it in the password entry field for the program in the usual way.
Dovіdka and nutrition, what to put often
Do you need help? Possibly, you will know the answers to your questions below.
Why is it in line with Apple's two-stage reverification?
So. Two-Factor Authentication is enabled on iOS, macOS, tvOS, watchOS and websites Apple. They have different methods for confirming the revision of the outbuildings and the given codes for confirming and optimizing the robot with a flicker. Two-factor authentication is the only language for victorious functions that require advanced security.
What work, if I can’t access the overridden addon, or the verification code is not taken away?
At the entrance, if there is no trusted building by hand, the confirmation code is displayed, the code is corrected for the verification of the phone number for help text notification or an automatic telephone ring. On the login screen, press the button "Code not taken" and select that the code was sent to the phone number, which you have misunderstood. Also, the code can be taken directly on the wrong extension in the "Setup" menu. .
How to grant access to the oblіkovogo zapis, why do not let the vikonati enter?
If you cannot enter, drop the password, or you can take the confirmation code, you can. Approval of the physical record is an automatic process that will help you to gain access to the physical record and prevent the possible access of other corylists in your name. Tse mozhe take a few days - or more - fallow, in addition, you can give the exact information about the oblique record for confirming the specialty.
What is needed now to remember the dietary intake on the control diet?
Ni. With alternative two-factor authentication, you don't need to select control power and remember the values for them. Your person is set up exclusively for additional passwords and conversion codes that are applied to your extensions and trusted telephone numbers. If you are starting to win two-factor authentication, we will save your control power by stretching two digits per day, so you will need to turn the old security settings for your cloud record. The next food will be removed.
Can the Apple support service help me get access to my cloud record?
Service apple tricks You can ask for information about the process of recognizing the oblique record, but you can’t confirm your person, or speed up the process, be it some kind of rank.
What are the system tools for two-factor authentication?
For optimal operation, it is necessary that the devices, which are matched with an Apple ID, should be given to the system assistants:
- attach an iPhone, iPad or iPod touch with iOS 9 or a newer version;
- Mac computer with OS OS X El Capitan and iTunes 12.3 or older;
- Apple Watch with watchOS 2 or older;
- Apple TV (4th generation) from tvOS;
- computer with Windows OS installed programs iCloud for Windows 5 and iTunes 12.3.3 or the latest version.
Why bother, if I don’t know about my misfortune, if I told you about the entrance?
If you enter a new annex, on other altered annexes you will be advised in which card is displayed with an approximate distribution of the new annex. This is approximately roztashuvannya, founded on IP-addresses present moment I’ll build it, but not exactly, I’ll build it. The indicated distribution can display information about the measure, to the extent that it is connected, and not about physical costs.
If you know that you yourself are a coristuvant, who is trying to get in, but if you don’t know about the financial situation, you can press “Permit” and continue the registration.
However, if you don't mind the fact that the Apple ID is being used to sign in to a new app, and if you didn't try to sign in, press "Do not allow" to block the login attempt.
What happens when you try to use two-factor authentication on an extension with older versions of the software?
If you choose to use two-factor authentication on devices for older versions of the OS, you may need to add a six-digit confirmation code, like your password, when you log in. on the revised add-on under iOS 9 OS or OS X El Capitan or later versions or take it to your verified phone number. Then enter a password by adding a confirmation code of six digits without a middle in the password field.
Can you turn off two-factor authentication after you turn it on?
Two-Factor Authentication cannot be turned off for any Cloud Records created under iOS 10.3 or macOS Sierra 10.12.4 and newer versions. Although the Apple ID is created in older versions of iOS or macOS, two-factor authentication can be turned off.
Keep in mind that if two-factor authentication is enabled, your physical record will be protected by passwords and secrets.
To disable two-factor authentication, sign in on the side of your Apple ID account and click "Edit" at the "Security" branch. Then click "Turn off two-factor authentication". After the creation of new secret food That two-factor authentication confirmation will be enabled. Although there is a daily item on the side of the Apple ID account for deactivating two-factor authentication, it cannot be deactivated.
If you can turn off two-factor authentication for your Apple ID without your permission, you can also turn off the notification email confirmation of registration sent to your Apple ID or reserve email address. Press the “Enable two-factor authentication” button in the lower part of the email notification to enable forward Apple ID security and control your physical record. Posilannya є active protyag two days after registration.
Publication date: 19.09.2017
Find out if you've forgotten the iCloud security code for iCloud Key Ringing Service.
If you have entered the iCloud security code incorrectly, you must have missed the iCloud Key Ringing service for a while, it will be disabled on this annex, and iCloud key binding will be removed. It is possible to see one of the coming reminders.
- “The security code has been introduced quite a few times already. Confirm your iPhone from one of your other devices, like typing the iCloud keyring. If you want to add it during the day, throw off the iCloud key ring.»
- “Too late trying to enter the iCloud security code. Confirm your Mac from one of the other devices that has the iCloud key ring. If you want to add it during the day, throw off the iCloud key ring.»
Yakshcho vikoristovuetsya, pristriy vvazhaєtsya dovirenim under the hour of the victorious entrance. You do not need to enter the iCloud security code for the iCloud Key Ringing service.
How to get access to the overridden add-on, which is the “iCloud key ringing” service
You can create a new iCloud security code on another device, such as the iCloud Key Ringing service.
On an iPhone, iPad or iPod touch add-on:
On a Mac running OS X Yosemite or a newer version
On the extension, on which the "iCloud Key Ringing" service is enabled, create a new iCloud key ring, which can be named after the koristuvach, passwords and other objects of key ringing on the extension:
On the extension, on which you have created a new iCloud security code, you will see a window for confirmation. Thank you for adding a new iCloud key link to the attachment.
I can't access the add-on, which is the "iCloud Key Ringing" service
To drop the iCloud key linking parameters, hover below.
Report about the iCloud Key Pairing feature.
What is "iCloud Key Ringing"?
ICloud key bindings save up-to-date usernames and passwords to websites from the Safari browser, given credit cards that information about Wi-Fi networks from the best known add-ons under the cover of iOS 7.0.3, OS X Mavericks 10.9 and newer versions.
Moreover, it is saved in it ob_kov_ records"Poshta", "Contacts", "Calendar" and "Notifications" services, synchronized with all Mac computers. And when you log in to Facebook, Twitter, LinkedIn and other public records on the Internet, iCloud automatically adds the names of the hosts and passwords to all attachments.
How is iCloud Key Ringing stealing my personal information?
Synchronized with the "iCloud Key Linking" function, passwords and credit card data are saved only on the outbuildings. If iCloud Key Ringing is enabled on a new add-on, other add-ons, on which this function has been set, will be charged for confirmation of the add-on add-on. After confirming iCloud key binding, it will automatically update the information on the new add-on.
Protecting information The iCloud keys are secured from the storage and transmission.
Yakshcho vikoristovuetsya, pristriy vvazhaєtsya dovirenim under the hour of the victorious entrance. For recognition, iCloud key ringing does not require additional storage.
How do I set up iCloud Key Pairing?
After iPhone update, iPad or iPod touch before the Setup Assistant asks you to setup the iCloud Key Ring. If you missed this part, and now you want to set up "iCloud Key Pairing", hover over below.
- Tap "Settings" > [your name] > iCloud.
- For iOS 10.2 or earlier, select Preferences > iCloud.
- Click "Key Ringing" and swipe the button to turn on the "iCloud Key Ringing" feature.
On a Mac running OS X Mavericks 10.9 or a newer version:
- Choose Apple () menu > System Settings and click the iCloud icon.
- Select "Key ringing". Optionally, you can set a password to unlock the screen after sleep mode or after the screensaver is activated.
- Enter your Apple ID and password.
- Watch the quotes on the screen.
On the skin attachment, which is necessary to add. If iCloud Key Ringing is enabled on a new add-on, other add-ons, on which this function has been set, will be charged for confirmation of the add-on add-on. After confirming iCloud key binding, it will automatically update the information on the new add-on. As a matter of fact, you can change the iCloud key ring without hanging out with the annex.
What is the iCloud security code?
Under the hour of setting up the iCloud key linking function, you can create an iCloud security code. You can either have a six-digit code, a collapsible alphanumeric code, or we can create a custom code for you. An iCloud security code is generated to authorize add-on devices in the "iCloud Key Pairing" feature. In addition, it allows you to identify the account and grant access to other features of the "iCloud Key Pairing" function, for example, to restore data at a time for all devices.
How can I set up iCloud Key Pairing on a new add-on so that it doesn't need to be verified on the other add-on?
Even if you don’t have access to your own 3 devices, which have the “iCloud Key Pairing” function installed, you can still use your other device for the following reasons:
- iCloud security code.
- Outbuildings telephone number, we will indicate when the “iCloud key bindings” are set, and the possibility of overpowering the SMS alert. This number is sent an SMS-alert with a confirmation code. If this number is not available, return to the Apple support service to confirm the person and complete the setup of the function on the new extension.
Once the setup is complete, the iCloud key pairing parameters will be transferred via push from cloud to the new device.
To win, enter a password and a six-digit verification code, which is automatically displayed on trusted attachments, and authorize the new attachment. Let's add the iCloud key ring.
Can the Apple support service redeem the iCloud security code?
Ni. If a number of incorrect iCloud security code entries exceed the allowed threshold, you will gain access to the "iCloud Key Ringing" feature. In such a case, go back to the Apple support service in order to confirm the person and re-enter the iCloud security code. If the first number of incorrect entries "iCloud key ringing" will be removed from the Apple servers and may need to be reconfigured.
Can you set up the "iCloud Key Linking" feature so that the information is not stored in iCloud?
So. When you set up the iCloud key linking function, you can skip the time of setting the iCloud security code. These same data are collected locally and only on the annexes praised by you.
If you don't create an iCloud security code, Apple can't help you re-pair your iCloud keys.
To set up the "iCloud Key Ringing" feature without setting the iCloud security code, hover below.
On an iPhone, iPad or iPod touch add-on:
- Select "Settings" > [Your Name] > iCloud and press "Key Ringing". For iOS 10.2 or earlier, select "Settings" > iCloud and click "Key Ringing".
- Enter password Apple ID ID.
- If you are asked to change the password, I will attach it as an iCloud security code, press the "Create another code" button.
- Select "Additional parameters", and then choose one of the options below.
- "Do not create a security code." As long as you don't create an iCloud security code, iCloud key bindings are stored locally on your add-on, not on Apple's servers, and will only be updated on the add-ons you've praised.
- Choose Apple () menu > System Preferences.
- Click on the iCloud icon, and then set the ensign "Passing Keys".
- Enter a password for your Apple ID.
- Press the "Dodatkovo" button, and then choose one of the two options.
- "Otrimati vipadkovy security code."
- "Do not create a security code." If you don't create the iCloud security code, the iCloud key binding is stored locally on your Mac, not on Apple servers, and it's less likely to be updated on the devices you've touted.
- To complete pairing iCloud keys, follow the instructions on the screen.
What happens if you enable iCloud Key Pairing on an add-on?
When the "iCloud Key Pairing" function is disabled, the device will prompt you to choose: save or delete password savings and credit card details. If you choose the first option, the data is not visible, but it is not synchronized when you change it on other outbuildings.
How many credit card details are collected from iCloud Key Ring?
iCloud Key Ringing collects credit card numbers and expiration dates for the term of your business. Cody security credit cards are not saved and are not automatically restored.
How does the “iCloud Key Pairing” function work from third-party programs?
So. Retailers can update robotic software with the iCloud key binding. Same passwords, saved by programs, are synchronized with passwords on other devices under the protection of iOS 7.0.3, OS X Mavericks 10.9 or later versions, on which programs are installed.
Can I remove my iCloud Keychain data from Apple servers?
So. Link to the following on your iPhone, iPad, iPod touch or Mac devices to link to iCloud:
On an iPhone, iPad or iPod touch with iOS 10.3 or a newer version:
- Tap "Settings" > [your name] > iCloud.
- For iOS 10.2 or earlier, select Preferences > iCloud.
- Press "Povyazati keys" > "Dodatkovo".
- Uncheck the "Verify with security code" option.
- Disable "iCloud Key Ringing" on all add-ons, deactivated.
On a Mac with OS OS X Mavericks 10.9 or a newer version:
- Choose Apple () menu > System Preferences. Click on iCloud, and then select "Oblikovy record".
- Please select "Permit confirmation for additional security code".
- Unmute iCloud key ring on all outbuildings, deviated.
Once the iCloud Key Ringing feature is disabled, the changes will not be synchronized with other attachments until the iCloud Key Ringing feature is disabled. It's a good idea to send your push keychain data to all of your devices, if not in the dark, but don't create an iCloud security code.
Publication date: 20.06.2017