Zharoznizhyuchі zasobi for children is recognized as a pediatrician. Allegedly, there are situations of inconvenient help for feverish women, if the children are in need of giving innocently. Todi dad take on the versatility and constipation of fever-lowering drugs. How can you give children a breast? How can you beat the temperature of older children? What are the best ones?
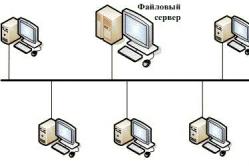
For the tradition of starting at the booths, they launch a kitchenette. For organizing, the role of the "cat" in one grain is a local numbered hedge. Without it, the company would send a message to the new office.
Installation of a LAN (Local area network)
Ale scho take LOM? Is it a cord that can be inserted into a computer? You can, You are welcome, having learned, as it is a lot of things to enter at the understanding of a local fancy.
So is it a local numbered framing?
LOM - the price of software and hardware devices for connecting computers from one system of obtaining and processing information. As simple as it is, it’s a local net: computers, modems, servers, routers, commutators and other possessions. Tse from one side. From the bottom - operational systems and protocols.
The word "local" in the name LOM casts on the size of the hem. Zazvychay won to serve in order to have one office chi budinok. Rіdshe - kіlka budinkіv.
Being among computers in a local grid is not guilty of overhauling 100 meters. As a result, the electrical signal cannot be podtolit on the cable of a large country. From the cymbals, you can struggle. In addition, between computers, they are actively installed.
Need a LAN?
The axis is for the main employees, which are used for processing the local numbered fences:
- Zagalny access to the Internet... The installation of a local mesh in an office can be done without special vitrates by organizing the connection to the Internet for a skin specialist.
- Communicative... You can set up a local custom server and organize a custom server or set up the program to exchange messages.
- Sumisna pratsya... Spіvrobіtniki can mentally work over documents on the server without the establishment of duplicate or manual copies. The robot is much more meaningful and organized.
- Local access to printers, copiers and scanners. You can justly spare the part of vitratic materials by adding a fencing printer or a scanner.
- Merezha vіdkrivaє majestic perspectives for organizing business-breeding. For example, it is possible to vikoristovuvati the Corporate Information System (KIC).
But far from all the possibilities of the framing, the scarlet abundance, the intelligence, like a straining tool, can be well planned and set up a local fenestration.
At the very name of the Local numbered framing, the sign, the function of the interconnection of the system, is already laid down. I will name it at the warehouses. Local, approved from the English local - micevy, so that the pattern is tied to a specific geographic place that is interconnected in the territory, numbered, Tied with a warehouse of hedge (numbered possession, PZ) and signs, hedgehog- I’m on the point of being aware of the number of possession that PZ on the ground (local) at the edge (for additional cables).
In such a rank, it is possible to formulate the value of the Locally numbered net (LAN) - the whole system of interconnected numbered resources (computers, servers, routers, software, etc.), for capturing-transmission, securing and processing of information of business people.
p align = "justify"> The development of locally numbered fences can function as well as they can be tied together for others in communes, for example, at enterprises with a filial fence in different places. The managers of such a connection can be connected with other stations, connected to a network of locally-numbered fences. There are local hedges, universities that are geographically located at 12,500 km (space stations and orbital centers), and even the stench carries all the same to the local ones.
According to LOM є securing a special and one-hour access for singing groups of individuals until the date, the program of possession (computers, printers, graphic loggers, attachments and access to files and databases) and transmission of data (electronic access to text, information viddalenikh bases) danih, transfer of digital movement).
For example: the manager accepts a request to enter it into the computer, it is far from the accounting office, and a rakhunok is formed there, one hour the information can come to the legal service to terminate the contract.
Crowbar characteristics:
- Visokoshvidkіsnі channels (1-400 Mbіt / s), but there must be more than one koristuvachevі;
- Become a workstation, which can be connected to a local grid, let it grow from hundreds to thousands of meters;
- Transfer of money between stations of EOM coristuvachiv;
- Decentralization of thermal possession, such as microprocessors, displays, cash registers, etc.
- Transfer of tribute to subscribers, we connect to the framing, overhead cable;
The main functions of LOM є:
- Security of one-hour access to the possession, software security and information, shared with the border;
- Minification of the risk of unauthorized access to information and cut-and-paste resources;
- Distributing access to information and stock resources;
- Providing a quick and confidential exchange of one-hour robots with information on the singing stake of individuals;
- Control over information flows, including incoming and outgoing;
- Distribution of control functions and related aspects on a skin university (for a skin university, a system administrator, as a rule, control functions);
- Optimization of vitrate at the production plant and the possession of a joint venture (for example, one printer per one printer)
As a result, LOM can be connected to personal computers, rostasovani on bagatokh in remote working missions. The work of the athletes is no longer isolated and integrated into a single system, as I’m special perevagi:
- Possibility of remote access to possession, PZ and information;
- Optimization of the resources of the robot processor;
- Numerous number and intensity of pardons at the appropriate level on the basis of telephone channels;
- Passage of the building of the site, lower at the global edge;
- Possibility of reconfiguration and development of new terms
Zasosuvannya area local hedges are even wider, nini such systems are practical for the skin office (for example, there is one printer for a number of computers, one for a printer is for one software, perhaps 1C: Accounting and others.). On a skin day, the flows of information become larger, the program of protection is more foldable and functional, the geography of the organization's activity is expanding. Stagnation in LOM grows not just bazhanim, but necessary for the success and development of business, science, new students, school students, training and retraining of faculty, display of state programs and functions.
The structure of the function of the hem.
The structure of a local pattern is based on the principle of management and the type of communication, most often it is to be found on the structure of organization, to be serviced. Vikoristovuyutsya type of topology: shinna, kil'tseva, radial, tree-like. Naybіlsh widenі pershі two vidi, for a rakhunok of an effective vikorstannya canals in connection, simplicity of management, nasty possibilities of expansion and snake.
 Bus topology- all computers are connected to the lance, connected to the main cable segment (trunk), at the end of the terminal there is a "termatori", to extinguish the signal, so that it can be connected to the sides. Computers in the framing are connected by a coaxial cable with a triynikovy z'udnuvachem. The throughput of the net is 10 Mb / s, for the occasional programs, which actively play video and multimedia data, which is a disadvantage. Reconstruction of the central topology of the field in the low wiring range and the unification of the connection.
Bus topology- all computers are connected to the lance, connected to the main cable segment (trunk), at the end of the terminal there is a "termatori", to extinguish the signal, so that it can be connected to the sides. Computers in the framing are connected by a coaxial cable with a triynikovy z'udnuvachem. The throughput of the net is 10 Mb / s, for the occasional programs, which actively play video and multimedia data, which is a disadvantage. Reconstruction of the central topology of the field in the low wiring range and the unification of the connection.
 The bus topology is passive. Zb_y of one computer doesn’t pour on the quality of the hedgehog. The posting of the main cable (bus) before the signal is displayed and the whole line becomes unpredictable. Vimknennya that especially connects to such a framing to break the tire, which causes the collapse of the circulating flow of information and system freezing.
The bus topology is passive. Zb_y of one computer doesn’t pour on the quality of the hedgehog. The posting of the main cable (bus) before the signal is displayed and the whole line becomes unpredictable. Vimknennya that especially connects to such a framing to break the tire, which causes the collapse of the circulating flow of information and system freezing.
Topology "tree"- Nybilsh has been configured to the "tire" type. Prior to the backbone main tire, through active repeated or passive multiplication, a splinter of simple tires should be attached.
 Topology "zirka"(star) - є the most convenient topology, information about the peripheral work stations to pass through the central university of the numbered hedge. The central university of management is a file server that can implement an optimal mechanism to secure against unauthorized access to information. All numbered fences can be keruvatis from the center.
Topology "zirka"(star) - є the most convenient topology, information about the peripheral work stations to pass through the central university of the numbered hedge. The central university of management is a file server that can implement an optimal mechanism to secure against unauthorized access to information. All numbered fences can be keruvatis from the center.
It is simpler to finish the cable production, because the skin work station is tied only to the central university. Vitrati laid cables to reach the top, especially if the central university is geographically expanded over the center of the topology. When expanding the number of numbered fences, it is unwise to know the winners before the winners of the cable tie: before a new workmanship, it is necessary to lay an edge cable from the center of the fencing.
At the time of the last configuration of the LOM skin attachment to the physical center, the information is transmitted only to one attachment. At the same time, they are reduced to transmissions and receptions, some of all stations take an active part in the transmission.
 Topology "circle"(ring) - computers are connected by cable segments, it has the shape of a ring, in principle identical to a tire, except for the need for a terminator. If there is an inequality of one of the segments in the net, the whole net will go wrong.
Topology "circle"(ring) - computers are connected by cable segments, it has the shape of a ring, in principle identical to a tire, except for the need for a terminator. If there is an inequality of one of the segments in the net, the whole net will go wrong.
Signals are transmitted in one direction. The skin station is without a middle ground, from two houses, ale the transmission of a single station. Kіlze to become a splinter of picks and from the resulting physical middle. Effortless stations can provide mothers with the right to have access to the physical center. At the same time, one of the stations can play the role of an active monitor, which will exchange information. The laying of cables from one working station to the last one can be carried out by folding and expensive, especially geographically working stations located far away from the circle (for example, near the line).
The main problem in the case of cyclical topology of polygons is that the skin work station is to blame for the active participation in the overwhelmed information, and at every turn, I want one of them to be paralleled. It is easy to locate faults in cable networks. Connected new working stations in the field of imaging of the hedge, oskilki before the hour of the establishment of the new work station. The circumference for the length of the numbered framing is dumb, very small, vise, vizyulyaetsya vіdstannyu vіdstannyu mіzh two working stations.
Computers can be connected to each other, and they can be easily accessible from the middle of the world: middle providers (twisted pair), optical providers (optical cables) and through the radio channel (childless technologies). Drotov, optical calls are established via Ethernet, drowned - via Wi-Fi, Bluetooth, GPRS and others. Most often, local networks are inspired by Ethernet and Wi-Fi technologies. It means that Frame Relay and Token ring protocols were used earlier, as on this day they are developing all the time, it can be deprived of special laboratories, primary mortgages and services.
Components of the maintenance of the downtime of the local framing vikoristovuyutsya:
- Adapter (network adapter) - attachment, which connects the computer (terminal) from the fancy segment;
- Міст (bridge) - pristіy, where from'є
- A router (router) - an attachment for interconnecting wide-area traffic for additional distribution of a net on a segment, securing information for information, managing and organizing reserve routes between wide-area areas;
- The commutator is an attachment of the high school designation, effectively segmenting the border, changing the area of the skin and increasing the throughput of the skin cancer station.
- Uninterruptible living units are an extension for securing the primary system of living.
Installation of Locally Computational Fringe (LAN)
Vibir in the form of topology, the middle is accessible to the warehouse of the LOCAL SYSTEM, and to lay down from all the needs of the Zamovnik. Modern technologies allow the development of an individual version, which is suitable for all vimogs and employees.
Laying of CABLE cables, such as those of the largest types of cable fences, can be used in different ways. When choosing a method of installation, it is based on individual architectural and constructive features of the awakening, its technical characteristics, the appearance of a framing, that is, that is the possession of, the order of interaction of low-current systems with other systems. Importantly, you can name two ways - display and admonition. For the proper conduction of the cables, the CROWNs can be used for the construction of the walls, the pidlog, the stele is more natural, the routes are stolen from the third-party injections, access to them is located, it is possible to be carried out immediately in a special preparation room. It is a pity that it is possible to carry out robots in an open manner, but often it is necessary to carry out robots in an open manner behind the addition of plastic boxes, vertical columns and trays. It’s not easy to forget, but there is still a way to lay cables in turn, it’s most often used for communal services, if there is no way to lay the cable near the channel, it’s too expensive.
The installation of a LAN is a foldable and flexible robot , as a result of the performance of the system, the stability and correctness of the functionality of the system as a whole, the steps taken by those who are deposited to its factory, the speed of transmissions and the processing of money, the number of pardons and the number of pardons. It is necessary to be carried even more primitively and seriously, for that, whether it’s the basis (the skeleton and the blood-bearing system) of the whole organism from low-current systems, it seems that there’s a large number of functions that do It is difficult for a robot to have a skinny system (expansion, repair, etc.) Economy of costs on the stage of design and installation of scrap metal, you can turn into kudi in big vitrates at the stage of operation and upgrade
Yaka pokryvaє zzvychay altogether a small territory or a small group of budowels (budynok, office, company, institute). There are also local hedges, universities that are geographically located at 12,500 km (space stations and orbital centers). Uninvolved on such sites, as well as all one carry to local.
Here you can ask about such a navazhlivish priest, a subscriber, a server, a client.
Subscriber (university, host, station)- tse pristіy, connections to the net and active in the information exchange. Most often a subscriber (university) of a net is a computer, or a subscriber can be, for example, a net printer or a peripheral attachment, but there is no way to connect to a net. Dal in course replace the term "subscriber" for simplicity, the term "computer" is available.
Server the subscriber (higher education institution) is called a net, who donated his resources to all subscribers, but not to vicarist resources. With such a rank, I will serve as servicemen. The servers in the net can be a little bit, but the server is not necessary, but the server is the most needed computer. Visions (dedicated) the server is a whole server, so you need to deal with the nether works. Unseen server Maybe, except for the service of the fancy, the visonuvati and the staff. A specific type of server is a chain printer.
Clintom The subscriber is called a fancy, which is only victorious fancy resources, but the resource itself in the framing is not visible, so that you will not be able to use your service, but you shouldn’t be bothered. Computer client is often called a workstation. In principle, a skin computer can be both a client and a server at once. From the server and the client, it is often not the computers themselves, but the software programs that run on them. At the end of the day, the program, as only seen the resource from the hem, is the server, and then the program, as only using the hem resources - the client.
Zavdannya LZ
Lokalnі friazhі allow okremim koristuvacham easily and quickly interchange one with one. The axis is deprived of deyakі zavdannya, as permits the viconuvati LZ:
- robot spіlna with documents;
- Simplified document management: you take away the ability to peer, coriguvati and comment to document your work, not organizing the collection of those narads that take away a lot of an hour;
- saving and archiving your robots on the server, so you don’t need to worry about space on the hard disk of your PC;
- easy access to programs on the server;
- the lodging of a spіlnogo vikorystannya in the organization of expensive resources, such as printers, accumulating CD-ROMs, hard drives and programs (for example, text processors or programs for securing databases);
Local components
The basic components of that technology, tied to the architecture of local framing, can include:
Apparatus for safety:
- cables;
- Servers;
- Fewer interface payments (NIC, Network Interface Card);
- Concentrator;
- Server for remote access;
Security program:
- Merezheve PZ management
Crumbs of the history of the computer connection
The connection to small computers in technology, having pushed back to the first personal computers.
Before the great computers (mainframes), there were numerical terminals (aka "intellectual displays"). True, the intellect in the cich terminals of the bulo is much too small, practically no processing of information was smelled, and the main meta-organizing connection was in the fact that it was necessary to distribute the intellect ("machine hour") of the great laborious and expensive computer. for multiple terms. The price was called the regime by the hour, and the great computer was last seen at the time of the day. In the case of the once reached the spilne of the numbered ones, the number of resources - the numbered ones (Fig. 1.1).
Rice. 1.1. Connecting the terminals to the central computer
Then the blades of the microprocessor and the first microcomputer. There was a possibility of developing a computer on the table of a skin corystic, some calculating, intellectual resources fell in price. Then all the resources are too expensive. And what does it mean goliy intellect without saving information and documenting? You will not be able to re-type the program when you turn on the liveness, but you won’t be able to win, or take it into the small life memory. They came to help me with a call. Having acquired a small number of microcomputers, it is possible to organize the production of the computer peripherals (magnetic disks, magnetic lines, printers). In general, all processing of information was carried out at home, and the results were transmitted to centralized resources. Here I know the same spіlno vikoristovuvalosya udorozhe, well є in the system, albeit called in a new way. I will call such a mode the mode of the ringing hour (Fig. 1.2). For the first time ever, use the call to reduce the performance of the computer system and call.

Rice. 1.2. Ob'dnannya in the netting of the first microcomputers
Then the personal computers appeared, as they were seen from the first microcomputers, so it’s not enough to get a new set for autonomous robot peripherals: magnetic disks, printers, it doesn’t seem like it’s about more monitors, etc.). The periphery has fallen in price and has become at the price of the whole adjusted with the computer. Well, b, now, start your personal computers (Fig. 1.3)? Who is it, since everything has already been sorted out and is on the table of the skin cure? Intellect at home vistachaє, periphery, i.e. How can I make a custom?

Rice. 1.3. Ob'dnannya in the line of personal computers
Naygolovnіshe - the price of the same spіlne vikorystannya resource. Those same zorotnyy podіl hour, altogether on a principled іnshomu іvnі. Here it is necessary to be stagnant for lowering the system's costs, as well as for the effective management of resources, which are available from ordered computers. For example, the hedgehog allows you to handle the volume of disks in all computers, making sure that the skin is not accessible from them to the most powerful ones.
But it is most obvious that some of them will appear in the same way, if all of them are actively working from a single database, feeding information from it and bringing it into a new (for example, at a bank, shops, warehouses). There is no need to use floppy disks here anymore: it took me many days to transfer data from a skin computer to a sieve, so that we could get rid of the whole state of kur'eriv. And everything is much simpler when I measure it: be it a serpent, be shattered from a computer, it will immediately become visible and accessible to all. In general, there is no need for a special housekeeping, and in principle, you can get by with cheap terminals (turn to the first visible situation), but even personal computers, you might be uninterestedly robustly. Until then, the possibility of folding information processing on the site can often be changed to change the amount of money that is transmitted.

Rice. 1.4. Vikoristannya local framing for organizing social robotics computers
It is also uncomfortable to get around without a hem, as it is necessary to protect the robot's robot from a number of computers. The situation is most likely to be learned, if the computers need to work not to enumerate the robots with the data bases, but in the managerial departments, in the control, and the computer to get out of these (fig. 1.4.). The attachments can be used for developing virobnichi technological systems, and for navigating control systems for scientific installations and complexes. Here, the grid allows synchronization of computers, interconnection and speed up the process of processing of data, so that it is not just peripheral resources, but rather intellectual technology.
The very significance of the overwhelming of local fences and the preservation of the popularity and ever wider stagnation, unaffected by all the lack of handiness, connected with the establishment and exploitation.
Topology of local fences
From the topology (components, configuration, structure) of the computer framing Get smart to physically roztashuvannya computers in a net one to one that way of connecting with the lines of communication. It is important for the understanding of the topology to lay down, peredusim, to the local hedge, in which the structure of the links can be easily quilted. In global fences, the structure of the links is pricked up in the form of coristas, and it is not even important, because a skin session can be carried out by a lord.
The topology of the type of cable to be used, the type of cable to be used, admissible and the best manual methods of control of the exchange, the reliability of the robot, the ability to expand the net. I would like to select the topology of the topology of the topology infrequently, the nobility about the particularity of the main topologies, their passages and the shortcomings of the demand.
Officials, which is injected into the physical propriety of the hedge and without the need to tie the topology to the understanding.
1)Computers (subscribers), plugged in to the net. In some cases, a subscriber breakdown can block the robot from all fences. In some cases, the subscriber's inequality does not flow into the whole robot, it does not interfere with the information for all subscribers.
2)The fairness of the hedgehog possession, that is, technical support, without any connection to the hem (adapters, transveri, roses, etc.). Vyhіd from the fret of the hemisphere possession of one subscriber can be found on all the hemispheres, or it is possible to destroy the exchange with one subscriber.
3)Integrity of the mesh cable... If the cable is cut into the mesh (for example, through the mechanical devices), the exchange of information can be destroyed in all the mesh, or in one of the parts. For electric cables, it is so critical to have a short flicker in the cable.
4)Interchangeable with cable, tied from the extinguished signal, which will expand according to the new one. Yak vіdomo, in any middle, with an extended signal, weaken (extinguish). And the more the signal goes through, the more it goes off (Fig. 1.8). It is necessary to quit, so that the cable doesn’t get too much for the fringe of Lpr, when you change it, it’s still unacceptable (the subscriber doesn’t recognize the signal, but it’s weak).

Rice. 1.8. Extinguishing the signal when the signal is widened through the hem
There are three basic mesh topologies:
Bus (bus)- All computers are connected in parallel to one line of communication. Information from the skin computer is instantly transmitted to computers (Fig. 1.5).

Rice. 1.5. Measuring bus topology
Bus topology(anyway, they call it the bus) by its very structure of transmission, the identity of the free-hand possession of computers, as well as the equal parity of our subscribers who can access the net. Computers in the bus can transfer information to the lack of it, so the line is connected to one of Edin's vipad. As soon as the number of computers will transmit information instantly, you will be able to compete in any way (conflict, colossus). At the tire, the mode of the so-called half duplex exchange is implemented (in both directions, albeit by the way, but not overnight).
In the topology of the bus, the central subscriber clearly bends, through which all information is transmitted, all the information is transmitted, and the whole system ceases to function for the video center. Adding new subscribers to the bus is easy to reach and you can get more robots for an hour. For a large number of cables with a victorian bus, a minimum number of cable is required for a specific topology.
Oskіlki the central subscriber is seen, the display of possible conflicts in the case of a child on the wall of the installation of a skin-friendly subscriber. At the connection with the cims of the hemming equipment with the topology, the bus is folded, below the other topologies. Protect through a wide spread of the netting from the topology bus (before the most popular Ethernet netting), the part of the netting is not necessary.

Rice. 1.9. Shaving the cable in the topology.
It is important to re-run the bus in the fact that when you see a computer, if you look at a machine, you can normally prodzhuvati exchange.
It used to be, when the cable is shaved, there are two complete tires (Fig. 1.9). However, it is necessary to use it, but through the special features of the expansion of electrical signals along the lines of the connection, it is necessary to transfer the inclusion on the tires of the bus of special uzgodzhuvalny attachments, therminators, shown in Fig. 1.5 and 1.9 in viglyadi rectangulars. Without the inclusion of terminators, the signal will be picked up from the end of the line and will be performed in such a way that the calls as the line becomes unwise. In case of a breakdown, or if the cable breaks down, the communication line breaks down, the communication between these computers, which has lost itself between them, will break down. In a short time, the bus cable will lead the whole line to the ground.
You can create a custom-made subscriber in the bus, and you can drive the entire net into operation. Until then, such a view is important to locate, some of all subscribers are turned on in parallel, and intelligence, which is not a bad thing for them.
When passing through the line the link of the netting from the topological bus, the information signals will be weakened and not updated, so that a severe interconnection is imposed on the total amount of line connection. Moreover, the skin subscriber can trim the signal from the net from the bottom to the subscriber, which is transmitted. Tse visuvaє dodatkovі vimogi to the priymalnі vuzlіv of fancy possession.
If you accept that the signal at the cable of the net will weaken to the boundary permissible level of the amount of Lpr, then the additional amount of the tire is not possible to change the value of Lpr. For a whole sensible bus, I will secure a new one with the opposite basic topologies.
To increase the number of segments from the topology of the bus, it is often shown that the number of segments (parts of the hem, leather from the bus) are shown, with the help of additional special signals and repeated signals. the borderline is the increase in growth to 2 Lpr, fragments of skin from the segments can be up to Lpr). However, this growth cannot be continued indefinitely. Interchangeable with a pre-dinner tied with a kintsevoy shvidk_styu razpushennya signals in the communication lines.

Rice. 1.10. Segments in a hedge-type tire for an additional repeater
Zirka (star)- one central computer is attached to one of the peripheral computers, and the skin from them will have a vikorist ring around the line (Fig. 1.6). Information from the peripheral computer is transferred without the central computer, from the central computer - one or more peripheral ones.

Rice. 1.6. Merezheva topology zirka
Zirka- a chain of single topology of the grid with a clearly visible center, which connects the subscriber's address. The exchange of information is carried out through a central computer, for which there is a lot of new options, for those who are not, as a rule, they cannot be engaged. Zrozumіlo, as little as the possession of the central subscriber is significantly foldable, less the possession of peripheral subscribers. About the equality of all subscribers (both tires) at the time of speaking. Call the central computer the most demanding, you will be obliged to pay for all the functions of managing the exchange. There are some conflicts at the bottom of the topology with the principle of ill-will, some of the management is more centralized.
If you talk about the performance of the light to the views of computers, then go out of the fret of the peripheral computer, as well as the edge of the possession, one should not be able to see the function of the part of the edge, if I start to work out the robustness of the central computer. At the connection with the cims of the lives of special calls, it is necessary to adjust the hopes of the central computer and the same device.
Having shaved off the cable for a short time at a new one with the topology of the star, I will interrupt the exchange with one computer, the protectors of the computers can normally feed the robot.
At the top of the tire, at the point of contact on the skin line, there are only two subscribers: the central one and one from the periphery. It is most often for them to receive two lines of communication, skin transmission of information in one straight line, so that on the skin line there is only one receiver and one transmission. This is the name of the transfer speck. All the price of the Sutta will forgive the common possession in the context of the tire, and will relieve the need for the possession of additional, called ternators.
The problem of extinction of signals in the line of communication can also be seen in the eyes of the simpler, lower in the case of the tire, and even the skin receiver will always receive the signal of one level. Boundary to the edge of the grid from the topology of the star can be added to the larger one, below the bus (tobto 2 Lpr), some leather from the cables, the same center with the peripheral subscriber, you can also have the mother Lpr.
Serious shortfall in the topology of the zirka polyagu in a severe interconnected number of subscribers. Call the central subscriber, you can service three more than 8-16 peripheral subscribers. It’s easy to add new subscribers to the tsikh mezakh, but after them it’s just uncomfortable. At zirtsi it is permissible to connect the substitution of the peripheral more than one central subscriber (as a result, the topology comes from a number of other stars).
Зірка, shown on small. 1.6 I will call it active or true stars. There is also a topology, as it is called a passive glimpse, as if the call is not similar to the glare (Fig. 1.11). At the end of the day, it was widened on the side of the river, and the star was active below it. To get the word out, you won’t be victorious at the most popular current Ethernet hedgehogs.
At the center of the grid with this topology, there is not a computer, but a special attachment - a hub, which I call it, a hub (hub), like a visitor the same function, like a reporter, so that the signals are updated, so that they come, all of the links.

Rice. 1.11. Topology passive star and її equivalent scheme
Go, if you want the wiring diagram to be connected to a normal or active star, in fact, you can find out about the bus topology, some information from the skin computer will be immediately transmitted to all the other subscribers of the central subscriber and not. Crazy, passive staring for a tire that needs a concentrator. To protect you, I have given a whole lot of low additional possibilities, tied from the passes of the zirka, zokrem, I will ask the servants for the repair of the fences. For the very same hour, the passive star of the day is more difficult to help the star, as it takes on an unpromising topology.
You can also see an intermediate type of topology with an active and passive view. At the end of the day, the concentrator does not only relay signals, but it controls the exchange, but it doesn’t take part in the exchange itself (it’s so broken in the 100VG-AnyLAN mesh).
Great dignity of the star (both active, and passive) is in the fact that the points of connection are selected for one mission. This allows the robot to easily control the hedge, localize the inequities by simply connecting quiet subscribers to the center (which is not a pity, for example, in different bus topologies), as well as interconnecting access to the least important ones for living To the peripheral subscriber at the time of the star, there can be either one cable (for which there is transmission in both directions), or two (the skin cable is transmitted in one of two smart lines), and the rest of the device runs more often.
In short, all topology types of zirka (active, and passive) are significantly larger, lower for other topologies, vitrate to the cable. For example, if the computers are installed in one line (like in Fig. 1.5), then when you select the topology, the star is known to have more space for the cable than with the bus topology. The price is conveniently injected onto the part of the hem and it is also easy to install the cable.
Kilce (ring)- computers are last connected to the door. The transfer of information from the circle is usually carried out only in one direction. The skin from computers will transfer information to one computer, which will go into the lance behind it, and will remove the information from the front in the lance of the computer (Fig. 1.7).

Rice. 1.7. Merezheva topology
Kilce- the whole topology, in which the skin computer communicates with the two lines: from one to the same information, to the one transmitted. On the skin line connection, as in the case of the star, there is only one transmission and one pickup (point-to-point type connection). You are not allowed to view the information about the registration of new terms.
The special feature of the field is important in the fact that the skin computer retransmits (update, if possible) the signal that comes before it, so that it appears in the role of a repeater. Signal extinguishing in a usable circle is not of a proper value, it is important to deprive it of extinguishing between susceptible computers of a circle. As a borderline for the cable, it is surrounded by a loss, it becomes Lpr, a total of a number of computers can be reached for NLpr, de N is a number of computers at a circle. The outer size of the hedge between the bude NLpr / 2, the splinters of the circle will be brought into the fold. There are tens of kilometers for the size of the circlet (for example, for the FDDI). Quite often I am changing the meaning of the topology.
Clearly seen by the center with a circular topology, all computers can be the same and equal. However, a special subscriber is often seen in the middle of the day, who controls the exchange or controls it. Zrozumilo, the appearance of such a single control subscriber will reduce the reliability of the hedgehog, and the odds of it will paralyze the entire exchange at once.
Strictly, the computers in the circle are more equitable (for example, for example, from the bus topology). Also, one of them will be bound by the information from the computer, when the transmission is carried out at a given moment, earlier, and at the same time. The very special features of the topology will be the methods of managing the exchange through a net, specially insured on the ring. In such methods, the right to step on the transfer (or, as it seems, on the flooding of the gutter) to pass one last time to the offensive on the stake of the computer. It is easy to connect new subscribers at the end of the week, if you want to connect all the robots for an hour of connection. As long as you have a tire, the maximum number of subscribers in a circle can be great (up to a thousand or more). Kil'tseva topology will give you a high speed to re-entanglement, you will not allow the robot in the great flows of information, so that it will be transmitted as often as possible, so that, as a rule, there are no conflicts , which can be re-entangled by the great flows of information.

Rice. 1.12. Merezha with two rings
The signal at the end will pass last through all the computers of the fancy, that way I want one of them (anyway, the fancy possession) will destroy the robot in the whole. Tse suttuviy nedolіk kіltsya.
So itself shaved off or a short mimicry in any kind of cable ring to rob the robot of all the heaps of ill-will. Three different topologies of the ring are the most challenging for the cable, so at the same topology of the ring you will need to transfer the laid two (or more) parallel lines, one of which is in the reserve.
One of the hemlines with a topological ring is based on two parallel ring lines, which transmit information along the other lines (Fig. 1.12). The meta of a suitable solution is an increase (in ideals - udvichi) information transmission as a measure. Until then, when one of the cables is used, the netting can be made with the same cable (however, the borderline changes in performance).
In the zoryano-ring (star-ring) topology in the ring, not the computers themselves, but special concentrators (images in Fig. 1.16 at the direct-turn viewers) are connected, to which computers are connected to their computers behind other times ring. As a matter of fact, all the computers of the net are included in a closed loop, so that all the hubs in the line connect a closed loop (as shown in Fig. 1.16). The topology gives the possibility of combining the crossings of the green and circle topologies. For example, the concentrators allow you to pick up all the points of cable connection in the mesh in one place. Just talk about the expanded information, the topology is equal to the classic ring.
At the end of the request, also talk about the mesh topology, when a computer is connected, it’s not just one, but a bunch of lines, to set up the mesh (Fig. 1.17).

Rice. 1.17. Sitkova topology: povna (a) and chastkova (b)
In general, the network topology has a skin computer without needing to connect with other computers. There is a wide variety of computers in the range of small numbers of computers that grows quickly and there are few lines of communication. In addition, whether the change in the configuration of the mesh was introduced into the configuration of the mesh of all computers, the firebox of the mesh did not reject a wide extension.
Chastkova sitkov topology of transmission of direct links without the most active computers, which transmit the maximum information. Інші computers are connected through industrial universities. City topology allows you to choose the route of delivery of information from the subscriber to the subscriber, bypassing disparities in the connection. On one side, there is a greater hope for the hem, and on the other side, there is a vimag of the Sutta acceleration of the hem, as I can pick up the route.
Fingering computer- A whole group of computers, connected by communication lines.
Local fences abo "local numbered fences"(LAN, Local Area Network) - there are some hedges, as there may be small local changes, so you can keep computers close.
Shchepravda, at once it is no longer possible to carry out a clear cordon between local and global fences. Most of the local hedge may be connected to the global one. But the nature of the information, which is transferred, the principle of organizing the exchange, the mode of access to resources in the middle of the local fence, as a rule, is strongly perceived from the quiet, which is taken up in the global fence.
Digital information can be transmitted by local hedge: data, images, telephone calls, electronic sheets too. Most often, local hedges are used for the subtlety (social vicarious) of such resources, such as disk space, printers and outputs for the global hedge, but at the same time the part of quietness is insignificant, as it is necessary to create local hedges. For example, the stench allows you to exchange information between computers of different types. The secondary subscribers (universities) can be used not only for computers, but also for attachments, for example, printers, plotters, scanners. With this help it is possible with a robotic technological system or pre-installation from a number of computers in one hour.
However, they may and may not end up with suttas of shortcomings, about such passages of memory:
Merezha vimag of additional, one-of-a-kind material vitrats for the purchase of a hemstitch installation, software security, installation of back-up cables and equipment for personnel.
Merezha can be taken to the robot by a specialist (administrator of the net), which is involved in the control of the robot, modernization, access to resources, the possibility of possible inadequacies, the way of information backup.
Along with the interconnection of the possibilities of shifting the computers connected to it, that is why you can transfer cables at all times.
Merezhi is an excellent middle ground for expanding computer viruses, so those who eat from them will have more respect than an autonomous victorious computer. Even enough information is needed and all computers will be hostile.
At the same time, I am very sensitive to the need for unauthorized access to information for її hijacking or misery. Information logist will require a whole complex of technical and organizational calls.
PLUSI TA MINUSI VIKORISTANNA LOCAL MEREZHI
Did you get it right?
bedroom vikoristannya resources
e-mail and call
quick exchange of information between computers