Antipyretic remedies for children are prescribed by a pediatrician. But there are situations of indispensable help in case of likhomantsi, if the child needs to give faces negligently. Then the fathers take on themselves the resuscitation and zastosovuyut antipyretic preparations. What is allowed to give to children of the chest? How can you lower the temperature in older children? What are the most safe faces?
Good day, shanovny vіdvіduvach. Name the stats. You have already realized what the language of the day is about the Zakhist. In one of the past articles, I looked at a product that can be introduced to this area of IT, showing itself badly. Today I will tell you about no less than a product of the company "Kaspersky Laboratories", our partners, Kaspersky Endpoint Security. We will look at the Hyper-V virtual environment on machines of another generation. The server part will be implemented on the Windows Server 2012 R2 OS domain controller, Windows Server 2012 R2 AD mode, and the client part on Windows 8.1.
It is important to note that this product is constantly winning in our practice of IT outsourcing.
What is Kaspersky Endpoint Security?
The solutions of Kaspersky Endpoint Security for Windows have light-class technology for protection against malicious programs combined with Application Control, Web Control and Device Control, as well as data encryption - all within the same program. Management of all functionality is carried out from a single console, which allows you to easily expand and administrate a wide range of Kaspersky Lab solutions.
feasibility:
- one supplement
- single console
- single policy
Kaspersky Endpoint Security for Windows is a single add-on that includes a wide range of the most important legacy technologies, such as:
- Protection against malware (including firewall screen and intrusion prevention system)
- Workplace control
- program control
- Web Control
- outbuilding control
- data encryption
Kaspersky Endpoint Security differs in the set of input modules, which should cover the difference in the number of modules in the fallback in the editorial:
- STARTER,
- STANDARD
- EXTENSIONS
- Kaspersky Total Security for Business
We will vikoristovuvat EXPANSIONS in our vpadku mi.
At the warehouse solution of Kaspersky Endpoint Security for Business START, select the following options:
At the warehouse solution of Kaspersky Endpoint Security for Business STANDARD select the following options:
- Defensive software, mesh screen and intrusion prevention system
- Workplace control
- program control
- Web Control
- outbuilding control
... as well as other technologies of Kaspersky Lab for IT security
Stock solutions for Kaspersky Endpoint Security for Business EXPANDATIONS and Kaspersky Total Security for Business have available options:
- Defensive software, mesh screen and intrusion prevention system
- Workplace control
- program control
- Web Control
- outbuilding control
- encryption
... as well as other technologies of Kaspersky Lab for IT security.
architecture
Server part:
- Administration Server of Kaspersky Security Center
- Administration Console of Kaspersky Security Center
- Kaspersky Security Center Admin Agent
Client part:
- Kaspersky Endpoint Security
Come on, let's get started
Installing the administration server
In our case, the administration server will be installed on the AD controller in Windows Server 2012 R2 mode. Let's run the installation:
.jpg)
Forgetting to clarify, we will quickly hack Kaspersky Security Center 10. installed new distribution , After downloading from the Kaspersky Lab website, the warehouse of which includes the installation package of Kaspersky Endpoint Security 10, obviously, and Admin Agent 10
At the next vіknі majstra choose a way to unpack the distribution kit and press "Install".
.jpg)
After unpacking the distribution kit, the installation wizard of Kaspersky Security Center tells us, after pressing the “Dalі” button, the wizard asks “Expand the size”, so that we will have only two clients, one x86, and the other x64 bit capacity, then we will say “Less 100 computers in merezhi".
.jpg)
We set the appearance record, under which the “Administration Server” will be started. Ours has an oblіkovy record of the domain administrator.
.jpg)
All of its data is stored by Kaspersky Security Center in the DBMS. When installing, the master prompts you to install Microsoft SQL Server 2008 R2 Express, otherwise, if the DBMS is already installed, you can choose the name of the SQL server and the name of the database.
.jpg)
At the “Administration server addresses” stage, the master asks for the server address, so that we have AD and DNS integrations installed, it would be more reasonable to specify the server name.
.jpg)
After selecting plug-ins for management, the installation of Kaspersky Security Center will start.
.jpg)
After a successful installation and the first launch of Kaspersky Security Center, we will be contacted by the master of the mail setup, in which we can specify the key, accept the participation of KSN, specify the address of the mail for the message.
.jpg)
.jpg)
This is how the parameters of innovation and policy are created by themselves.
.jpg)
After installation on our server will be installed:
- administration server
- administration console
- agent Administration
Ale, there will be no installations of Kaspersky Endpoint Security. If the installation is removed, since the administration agent is already installed, we can deploy Kaspersky Endpoint Security to the server. If the administration agent is present and blocked at all entrances to the Windows firewall, the installation will not be performed. Activate the "Remote installation" and select "Start remote installation master". Select the installation package and press the "Next" button
.jpg)
At the window "Select computers for installation" choose the installation option for computers placed in the administrative groups. Let's choose a server and press the "Next" button.
.jpg)
Reloading of the system will be required after updating the important modules of Kaspersky Endpoint Security, so that a new package needs to be updated, then reloading is not required. At the choice of oblіkovyh tributes, we will borrow everything for the locks, that is empty. After pressing the "Next" button, we continue to install Kaspersky Endpoint Security.
.jpg)
.jpg)
group group
The fragments of the policy and the administration, recognized for the servers, are changed in the policy and the administration of the working stations, then we create a group that determines the type of administration for various machines. Rozgornemo vuzol "Kerovani kompyuteri" and select "Group", press "Create a subgroup". We create two subgroups, "Working Stations" and "Servers". From the menu "Kerovanie komp'yuteri - Kom'pyuteri", for the help of "drag and drop" or "cut & copy", "DC" we will transfer to the "Servers" group and create a policy and task for this group Vuzli "Kerovan Computers".
Installing Kaspersky Endpoint Security
To remotely install Kaspersky Endpoint Security, you need to enable UAC for the installation hour. Vmoga є “inhuman”, so we create a policy for the Windows firewall in the GPO, in which it is permissible to follow the next intelligent rule “Great access to files and printers”.
After setting up and expanding the group policy, let's go to the administration console. Open the "Administration Server" window and select "Install Kaspersky Anti-Virus", click "Run Remote Installation Wizard". In the window of the master, select the required package for the installation package and press “Dali”. Select the clients in the group "Computer Unresolved" and press "Dal".
.jpg)
In the coming century, everything is too much for the locks and we press “Dali”. After a window with the choice of a key, the master asks the koristuvach about restarting the system after the installation of Kaspersky Endpoint Security is completed, it is too much for locking and we press “Dali”. At the end of the “Vidalennya insane programs” you can make adjustments, obviously, as the stench is needed. Let the master move the client computers to one of the groups, in our case, move them to the "Working stations" group.
.jpg)
.jpg)
.jpg)
How mi Bachimo, the console "talk" about the successful installation of Kaspersky Endpoint Security on client stations.
.jpg)
As a matter of fact, after installing the server, the administration of the transfer of client machines was taken out of the mind in the task of the installation.
.jpg)
Kaspersky Endpoint Security on a client machine.
.jpg)
We create a policy for client stations, in which case we include "Password Protection", it is necessary, for example, if you want to turn off the anti-virus.
.jpg)
Let's try to turn on the lock on the client's machine.
.jpg)
Rules for moving computers
On the administration server, you can set relocation rules for client computers. For example, let's create a situation where Kaspersky Endpoint Security will be installed in a new PC. It's handy in the scenario, if there are new PC installations in the organization.
To automate the roaming of Kaspersky Endpoint Security, we set up roaming rules for computers. For which one, select the university "Non-separated computers" and select the item "Adjust the rules for moving computers in the administrative group" and create a new rule.
.jpg)
.jpg)
At the created rule, new manifestations of the PC will be added to the group "Workers of the station" from the specified range of IP address.
Let's create the task of automatically spitting out anti-virus protection for machines that do not have installations on them. For this select the group "Working stations" and go to the tab "Zavdannya". We are doing the task of installing an anti-virus protection with the "Negaino" layout.
Since then, my bachimo, that the client's computer was a source of contributions to the "Station Workers" group.
.jpg)
Let's go to the "Schedule" tab and it seems that the task after the installation is running.
.jpg)
I’m guessing that the situation was implemented on machines without anti-virus protection (if I wanted to demonstrate the installation on one of them, then, after that, I tested the anti-virus, to demonstrate this scenario) and, as you can see, the installation was installed on machines without anti-virus protection, the machine was anti-virus bula zahistom zvrushena. After the installation of anti-virus protection devices, the KES policy will be set to this client computer.
Call
Call in Kaspersky Endpoint Security more, less informative. For example, look at the link “About versions of Kaspersky Lab programs”.
.jpg)
At the svіtі, dosit report, vіdobrazhaєєєєєєєєєєєєєєєєєєєєєєє about installed programs "Kaspersky Lab". It can be seen on the links of agents, client solutions and servers installed. Calls can be seen and added. So you can look at the anti-virus zakhist camp for help from the “Computer Selection”, as it helps to manually sort computers with infected objects or with critical podia.
In conclusion, I would like to say that only a small part of the anti-virus complex of Kaspersky Lab was looked at. Manageable, actionally, є easily and intuitively understandable. Ale varto to respect the greatness of the interest of client systems for an hour by looking for viruses and potential threats, the interest of Wiklikan is given mainly through heuristic analysis, which means a lot of resources. The product is more comfortable in the administration and is suitable both in the middle AD and in the working group. This product has been installed by many of our clients and shows itself only in a good way.
All people, peace be with you!
Shanov's colleagues! Today I want to tell you about the Kaspersky Anti-Virus Administration System. Rich, I'll tell you, duzhe cicava.
For help, you can take control of all your computers in your organization in terms of allowing / blocking the launch of sites, allowing / blocking the launch of programs, including those for the most important categories (for example, you can block the launch of all browsers, crimes designated), allow / zaboroni broadband Internet whether yakogo obladnannya - fleshok, zhorstkih diskіv she Lots Other (napriklad, dwellers viklyuchiti zliv Informácie koristuvachami) takozh avtomatizuvati do updates klyuchіv for antivіrusa Kasperskogo, mіnіmіzuvati vitratu trafіku at onovlennі antivіrusіv (pіslya installation KSC i nalashtuvannya on Demba antivіrusіv, vstanovlenih on robochem stations, the stench will be updated by the server itself, and not by the Internet). To install KSC version 10, according to the words of the technical consultant of the Kaspersky laboratory in the Volga Federal District - Pavel Aleksandrov, you need to use Windows OS (not a language-based server) if you want 2-4 GB of RAM. Recently, the company "Intelligent Solutions" held a practical master class on laptops, where your faithful servant could get acquainted with this creation of the Kaspersky laboratory. Kaspersky Security Center 10, as Pavlo said, hopes to be cost-free for those who have a corporate license for KES (Kaspersky Endpoint Security) tools available from the GIST at kav.tatar.ru. And also, for your goodness, colleagues, I will publish video lessons kindly given by Igor Oleksandrovich, manager of the company NovaInTech -> Submission to video lessons on Youtube website. As soon as I watch the video you are running out of food, then I, with pleasure, will help you in Skype (lisischko).
P.S. You can work your own server for managing Kaspersky Anti-Virus under the TsITovsky KSC, I won’t tell you if I don’t work - I didn’t become one myself, but it’s described on the site kav.tatar.ru
Note1: The list of retrieving files is not updated on the server, continue to create a new task "Inventory", until the checkbox is checked in the "Additional parameters" - "Call that link" - Inform server administration "About running programs" in Anti-Utilities.
Note4: Hour after hour on computers under KSC everything starts to freeze. The dispatcher has already shown how the system can be attacked by the "Kaspersky Security Center Vulnerability Assessment & Patch Management Component" process (the vapm.exe file is called). The analysis of the problem showed that at the time of the system's troubles, the task "Search for inconsistencies and necessary updates" was completed, the transfer of this task to manual launch and the problem was eliminated. So, є variant zі znyattyam ticks "launch missed task" in the schedule of tasks (without shifting the launch to manual mode), but I didn’t choose this variant, on the basis of the decision about the inconvenience for us of this function. UPD: it has not passed the first year since the start of the task and I will switch the mode to manual launch, like її, again, by launching the same trigger. There is no time to disassemble. Having seen the order "A search for inconsistencies and necessary updates", you can add it to the day.
 The more the measure, the more the system administrator (or the IT department) is able to automate the management of software products. Antivirus software is not to be blamed for this plan.
The more the measure, the more the system administrator (or the IT department) is able to automate the management of software products. Antivirus software is not to be blamed for this plan.
A lot of anti-virus makers can help in their arsenal for the remote administration, today there is a mova about similar solutions from Kaspersky Lab.
Vzagali, Kaspersky Security Center - dosit serious addendum, describe which one in one article is definitely not possible. For this reason, in this article, only a little laryngeal speech is considered.
You can take advantage of Kaspersky Security Center. The product itself is built from the server, which will be necessary to fire up, the administration console, which can be installed on another computer for the remote administration server, the web console as an alternative to the powerful administration agent, which can be installed on the client computer anti-virus software with a server.
The server itself needs to be upgraded only on operating systems of the Windows family. Moreover, the presence of the server edition is neobov'yazkovo. Supported systems in XP and more, but only in Professional / Enterprise / Ultimate editions. You can find a complete list of supported systems on the site.
Of course, a server for your work requires MS SQL or MySQL (it is possible to remove it). As there is no ready-made database server at hand, the installer of Kaspersky Security Center itself installs MS SQL Express, which is sufficient for most organizations.
Also, for the development of the server, we will download and launch the installation file (I recommend downloading the latest distribution kit). As a test stand, we have a computer with the Windows Server 2012 R2 operating system.

You can select the menu manually, in which we can immediately select the item "Install Kaspersky Security Center 10".
When the installation starts, you will be prompted to accept the license agreement, as well as select the type of installation. For the shortest control over the installation process, a vibrating installation is essential.

Even though there are mobile attachments, for managing them, you can install an ocremic component.

Tell me about your measurements. This paragraph, however, does not carry any important primordial force.

Then the installer asks the s-p_d of some kind of koristuvach to start the administration server service. You can show up as an explicit koristuvach with administrator rights or allow the installation program to create a new one.

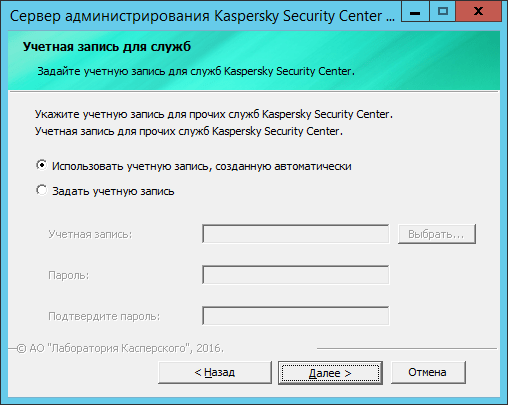
Coming soon, you will choose the data base server. As it was already said, there are two options here - MS SQL or MySQL. If you don't have a ready-made server, Kaspersky Security Center can easily run MS SQL Express.


At some point during the installation process, you may get a small surprise because your system does not have the .NET Framework 3.5 SP 1 installed.

Windows Server .NET Framework 3.5 SP 1 is expected to be a component, and it needs to be enabled. If you do not have a server operating system, then you need to go to the Microsoft website and download the installation program.
Let's look at the option to enable the component in Windows Server. For this, select Server Manager and select the item “Add role for this function”.

The master will start, in which it is necessary for us to indicate that we are choosing to install roles or components.
 Master of adding roles and features in Windows Server
Master of adding roles and features in Windows Server Select our server and skip select roles. .NET Framework 3.5 Functions is known to the list of components and marked with a tick.

 Adding a Component to Windows Server
Adding a Component to Windows Server Then let's turn around before installing Kaspersky Security Center without interruption.
We need to select the SQL authentication mode. Tse mozhe buti yak okrema oblіkovy record, so it is in-line.

The Kaspersky Security Center server requires a folder to which client computers could be downloaded to process updates and installation packages. You can create a new folder or specify the correct one.

Vkazuєmo port, for which we will connect to the administration server.

Specify the server address in the measure. If the server has a static IP address, you can fuse with it. But still, it’s better to designate a server for im'ya.

The rest before installation - select the necessary plugins. The modules allow you to manage various anti-virus products of Kaspersky Lab. It's all right, as you have the whole "zoo" version. Modules can also be installed later.

Now the installation process is no longer needed. Somewhere on the plug-in, you need to accept the environment.

Installation of Kaspersky Security Center is completed.

Now let's go through the mail server setup. The administration console, which is installed at once behind the server, looks like an upcoming rank:
 Administration Console of Kaspersky Security Center
Administration Console of Kaspersky Security Center The console can be installed and fixed. І navit it is necessary, so you don't go once on the server for routine activities.
The left column of the server has been overhauled. While there, only our schoyno creations server. If you administrate a server server, then simply click Add Server Admin.
Otzhe, click on the well-created server, and the Master of the Cob Builder will start. You will be asked to activate the program for additional code or a key. Vtіm, zrobiti tse it is possible and pіznіshe.

In addition, the master asks you to become a part of the Kaspersky Security Network program. In fact, there is only one spy on your computers that manages the Kaspersky Lab data about those resources you visit and despoil. Motivate the creations as a basic knowledge. In my opinion, for a kіntsovogo koristuvach, there is a sense of participation in such a program of doubts.
You will also be asked to send us screenshots to confirm the type of the Kaspersky Security Center server. Tsey krok can be skipped.

After all these changes, the server should take over the rest of the versions of the firmware update. Nadalі it is possible to fix it like a dzherelo update on the servers of the Kaspersky Lab in the Internet, and the host server, as in your mirezhі їх kіlka.

After downloading the update and testing the merezhі, the master will be notified about the successful completion and prompting to start the master of the throating at the working stations.

Let's talk about the throatiness of a zahist at work stations.
The gateway is closed, so there is no possibility to install it directly between the administration server and the client computer. For example, the Administration Server is included in the corporate dimension, and the client computer is not included in it.
Yak insert
To install the Admin Agent locally in the gateway mode:
- Run the installation file on the add-on, which will be the gateway for the day.
For locking, the installation file is expanded:
\\<Адрес сервера администрирования>\KLSHARE\Packages\NetAgent_10.4.343.
- Get to know the minds of the licensed court and establish an ensign I accept the license terms.
- Select installation folder.

- Ask Server Addresses and appoint an ensign Allow the Administration Agent to open the UDP port.

- miss the croc Proxy server configuration.
- wrap Vykoristovuvaty as a gateway z'ednan in the demilitarized zone.

- wrap Remove from Admin Server.

- Set tags to zastosovuєte їх. Learn more about tag tags in the article How to tag tags in Kaspersky Security Center 10.

- miss the croc Additional parameters.
- set an ensign Run the program in the installation process.

- press insert.

How to set up
- Open Kaspersky Security Center 10.
- Open context menu of a node Kerirovanie outbuildings and press create → group.

- Set the name of the new group and press OK.

- Vіdkryte authority vuzla administration server.
- Go to retail agents update and appoint an ensign Assign agent updates automatically.Press Add.

- For the dropdown menu, press the fields Add the gateway z'ednan, which is located in the demilitarized zone, for the address.

- Enter the address of the call gateway and press OK.

- Select a set of attachments that are connected to these gateways. press OK.

When using a black scan, the Admin Server will reveal the data by the IP address of the gateway and place it in Undivided outbuildings.
- Add the z'ednan gateway to the group outbuildings set on short 3.
- Vіdkryte authority vuzla administration server and go to branch agents update. press Add.
- The dropdown menu has fields Priest, which will win the role of an update agent press Add attachment from the group. Add a gateway to the group outrageousI will add and press OK. Repeat block 8.
- Select donations gateway z'ednan and open yoga authority.

- Go to retail Gateway. set an ensign Gateway z'ednanі Initiate the creation of a connection behind the gateway from the side of the Administration Server. Ask Gateway addresses for remote outbuildings, For example, abc-lab.kaspersky.com. press OK.

You can create an Admin Agent policy for the gateway. When folding on a croc Merezha raise an ensign Wicoristy UDP port.

Meta Robot.
This laboratory work is assigned to the installation of the server for managing the anti-virus protection of the Security Center.
Front view.
Before proceeding with the installation, it is necessary to sign out from the wild script of the anti-virus infection. Two main scenarios propagated by Security Center retailers:
- - throating anti-virus infection inside the organization;
- - spreading the anti-virus protection against the organization-client (to be victorious by organizations, acting as ssrvis-nroviders). Well, the scheme can be victorious within the organization, but there may be a sprinkling of remote subdivisions, computer systems of those administrators independently in the headquarters of the head office.
In these laboratory robots, the first scenario will be implemented. If you plan to create another one, then you will also need to install and configure the Web-Console component. And here it is necessary to say about the architecture of the Security Center. Wine includes the following components:
- 1. Administration server, which is the function of centralized collection of information about the establishment in the organization of the LC programs and their management.
- 2. administrative agent zdіysnyuє vzaєmodіyu mіzh server administration and LC programs installed on the computer. Є version of the Agent for different operating systems - Windows, Novell and Unix.
- 3. administration console provide a coronary interface for server management. The administration console is visible in the view of the extension component to Microsoft Management
Console (MMS). It allows you to connect to the Administration Server either locally or remotely, locally or via the Internet.
4. Kaspersky Security Center Web Console is recognized for the control of the anti-virus protection of the organization-client, which is under the control of the Kaspersky Security Center. We will not discuss this component within the framework of this laboratory workshop.
- 1. Installing and configuring the Server and Administration Console.
- 2. A group of administrators created and assigned client computers to them.
- 3. Remote installation on client computers of the Administration Agent and anti-virus programs of the LC.
- 4. Updating signature bases of LC programs on client computers.
- 5. Raising awareness about the possibility of anti-virus infection.
- 6. Starting the task of rechecking for Windows and rechecking the work and reporting about the subs on client computers.
- 7. Analysis of calls.
- 8. Implementation of automatic installation of anti-virus programs on new computers in the company.
In this laboratory robot, the first stage will be looked at. On fig. 5.35 shows a diagram of a laboratory stand, which imitates a measure, which is protected (also described earlier in Table 5.4). Lab meta - install the server and the Security Center administration console on the AVServ server.
Mal. 5.35.
Table 5.5
Validity in versions of the distribution package of Kaspersky Security Center 9.0
|
component |
povna |
|
|
version |
version |
|
|
Administration Server distribution kit |
||
|
Distribution package of Kaspersky Endpoint Security for Windows |
||
|
Distribution of the Administration Agent |
||
|
Microsoft SQL 2005 Server Express Edition |
||
|
Microsoft .NET Framework 2.0 SP1 |
||
|
Microsoft Data Access Component 2.8 |
||
|
Microsoft Windows Installer 3.1 |
||
|
Kaspersky Security Center System Health Validator |
The Security Center distribution package can be obtained at http://www.kaspersky.com/downloads-security-center. If so, you can choose the version of the downloaded distribution kit - Lite or completely. At the table 5.5 reinstatement of the release of distributions for version 9.0, as it was awarded during the preparation of descriptions of laboratory robots. For laboratory testing, a new version will be needed, so at the same time as installing the administration server, the MS SQL Server 2005 Express DBMS will be installed, as it will be tested for collecting data about the anti-virus protection camp.
Description of the robot.
After the preparation is completed, we launch the Security Center installation program on the AVServ server. After the next installment, the path for saving the files needed in the installation process will be powered up, it will appear one more time during the installment window and the next one with a license agreement, as it is necessary to accept for the continuation of the installation process.
When choosing the type of installation, the item “Vibration” is significant, which allows you to get to know in detail about the change in the installation of the component and installation of installations.
If you select the “Standard” option, then as a result of the work of the wizard, the Admin Server will be installed together with the server version of the Admin Agent, the Admin Console, available in the distribution kit of the program management plug-in and Microsoft SQL Server 2005 Express Edition (which was previously not installed).
The next step is to select the server components to be installed (Fig. 5.36). We need to install the Administration Server, and we will leave the badge on this item.
Cisco NAC technology, which allows you to override the security of a mobile device or computer that connects to your home, we will not be victorious.
Also, within the framework of the laboratory workshop, it is not planned to spread the anti-virus infection on mobile devices (such as smartphones), so the designation of the components can not be set at once.

Vibranium expansion merges into the setting of the value of a number of parameters that determine the anti-virus protection of the robot (the stink of re-exploration in Table 5.6). These settings can be remembered, if necessary, after the server installation.
It will also be necessary to specify an oblique record, in the name of which the administration server will be launched, or wait until a new record is created (Fig. 5.37).
Older versions of Windows (for example, when installed on Windows Server 2003) may have the System Record option present this week. For whatever reason, this record is the responsibility of the mother of the administrator's rights, which will be necessary for the creation of data bases, as well as for the remote work of the server.
Table 5.6
Parameters that are installed in the fallow in the size of the border
|
Parameter / number of computers |
100-1000 |
1000-5000 |
more |
|
|
Display in the console tree of the node of the associated and virtual servers for administration and all parameters associated with the associated and virtual Servers |
Daily |
Daily |
present |
present |
|
fermentation of distributions Bezpeka in the years of power of the Server and the group of administration |
Daily |
Daily |
present |
present |
|
Creation of the policy of the Administration Agent for the help of the master of the cob |
Daily |
Daily |
present |
present |
|
Delayed the launch of the update task on client computers by the order of the day |
Daily |
in the interval of 5 minutes |
in the interval of 10 minutes |
in the interval of 10 minutes |

Mal. 5.37.
An offensive croc is a selection of a victorious database server (Fig. 5.38). To collect data, Security Center 9.0 can hack Microsoft SQL Server (versions 2005, 2008, 2008 R2, including Express 2005, 2008 editions) or MySQL Enterprise. On fig. 5.38, a shown for selecting the type of DBMS. If you are contacting a MySQL server, you will need to specify the port number to connect to.
If you want to select a basic instance of MS SQL Server, you will need to specify its name and the name of the data base (for locking, it is called KAV). Our laboratory robots will have a recommended configuration that transfers the installation of MS SQL Server 2005 Express together with the installation of the Security Center (Fig. 5.38, b).

Mal. 5.38.
If you choose SQL Server as a victorious DBMS, you must specify the authentication mode, which will be victorious when working with it. Here we have to fix the lock - the Microsoft Windows authentication mode (Fig. 5.39).
In order to save installation packages and update every day, the administration server will select a folder that hopes for global access. You can specify an existing folder or create a new one. Іm'ya zagalnogo resource for zamovchuvannyam KY8NAKE.

Mal. 5.39.
It is also hoped that port numbers can be assigned to connect to the Security Center server. TCP port 14000 is used behind the lock, and TCP port 13000 is used for the connection protected by the additional SSL protocol. The cream was created more, for transferring to the server information about the computer's mimicing, the UDP port 13000 is set.
Given the need to specify a method for identifying the administration server. You can either use IP addresses, DNS names or NetBIOS. In the case of a virtual network of organizations, for the laboratory workshop, a Windows domain and a present DNS server, we will have to win the domain names (Fig. 5.40).

Mal. 5.40.
The next step allows you to select and install plug-ins for managing anti-virus programs of the LC. Looking ahead, we can say that the product Kaspersky Endpoint Security 8 for Windows, a plug-in for everything we need, will be very popular (Fig. 5.41).

Mal. 5.41.
Once selected, the programs and components will be installed on the server. Upon completion of the installation, the administration console will be launched, or, if you unchecked the box for the rest of the installation wizard, launch it from the Start menu -> Programs -> Kaspersky Security Center.
Task 1.
Before the description, please complete the installation of the administration server on the AVServ virtual machine.
When you start the console, the server settings are changed. On the first page, you can specify activation codes or files of license keys for anti-virus products of the LC. If you have a "corporate" key on a computer bank, with default settings, the key will be automatically expanded by the server on client computers.

Mal. 5.42.
You can also take a look at the Kaspersky Security Network (KSN), a remote service for accessing the Kaspersky Lab's knowledge base about the reputation of files, Internet resources and software security.
Offensive crock - setting parameters for notifying the administrator of the anti-virus protection by e-mail. You need to specify the mail address, smtp-ssrvsr and, if necessary, parameters for authorization on the server (Fig. 5.42). Since the laboratory does not have a valid mail server, you can skip this part and try to fix it later.
In order to access the Internet through a proxy server, you need to specify some parameters. After passing through this stage, the standard policies, group tasks and administrative tasks will be automatically created. The stench will be examined in greater detail in the upcoming laboratory robots.

Mal. 5.43.
Offensive crock - automatic launch of the advancement update. As soon as the engagement started successfully, you can, without checking the completion, press the “Dalі” button and after the completion of the work of the master of the cob setup, go to the main window of the Administration Console (Fig. 5.43). There, it is guilty that there is one computer in the measure (together with the administration server on the AVScrv computer, the installations and the administration agent), for which there is an anti-virus protection. It is rated as a critical podia.
Task 2.
Witness the postal server setup.
Alternatively, the administration console can be installed from the Console folder on the distribution disk by running the Setup program. If a distribution kit is downloaded from the Internet, then it is necessary to enter a folder for saving distribution files on the top of the installation. Behind the lock is the folder C: KSC9 ussianConsole.

Mal. 5.44.
Task 3.
Install the Security Center administration console on the Stationl .labs.local virtual machine. Change the connectivity to the AVServ.labs.local server. For this, the console needs to specify its address or name (Fig. 5.44), and also wait for the server certificate to be withdrawn (Fig. 5.45).

Mal. 5.45.

Mal. 5.46.
In order to connect not far away, turn over, chi are not blocked on the AVScrv server, port, twist to connect to the Security Center server (div. Vishche). The setting can be changed through the Control Panel: System and Security -> Windows Firewall -> Allow the program to run through the Windows Firewall. Vіdpovіdnі allow settings vinnі buti prsutnіmi, div. Rice. 5.46 (the names of the rules have been removed as in the previous version of the product - Kaspersky Administration Kit).