Zharoznizhyuchі zasobi for children is recognized as a pediatrician. Allegedly, there are situations of inconvenient help for feverish women, if the children are in need of giving innocently. Todi dad take on the versatility and constipation of fever-lowering drugs. How can you give children a breast? How can you beat the temperature of older children? What are the best ones?
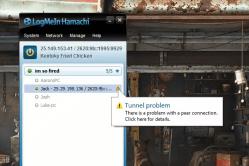
Those who are on the Internet with viruses are no wonder today. Bagato koristuvachіv sprymayut situations, tied with їkh injected on the system, or special data, myyako, I wonder if you’re curious about your fingers, albeit just until quietly, leave in the system without a cipher in the middle. Yak vilykuvati and deciphering the data, which are saved on a hard disk, most of the wicked ones do not know. To that end, the contingent is "led" on the vimogi, as the malevolent people are hanging out. Ale let’s wonder if it’s possible to develop such a contamination or prevent penetration into the system.
What kind of virus encryption?
A threat to this type of vicious standard and non-standard algorithms for encrypting files, which will increase the change and block access. For example, to open a text encryption file for reading or editing, as it is itself and to create multimedia content (graphics, video or audio), it will be absolutely uncomfortable for a virus to enter it. Navigate the standard copy or change objects that appear inaccessible.
The software itself is filled with viruses є in this way, which is encrypted in such a rank, so that it’s not possible to update the system. Make sure to use these advanced programs to create powerful copies and keep the system even worse, so the virus-encrypting files will not be seen very quickly. Deinstalling the main program, or just seeing the main virus, the coristuvach will not be allowed to get dirty, not even if it seems about the updated encrypted information.
How does a threat penetrate the system?
As a rule, contaminate a certain type of good organization on a large commercial structure, and you can get into a computer through postal programs, if a spider has opened a document in an electronic post, say, before (Commercial propositions with investments from the total dzherel - the first way for the virus).

Because, since the virus-encryption machine is on the machine, it is possible to have access to the local grid, the building adapts and in it, the power copies are not only in the cut-out, but on the administrative thermal data, which are not available firewall chi brandmauer.
In some cases, you can get in the way of getting into the computer systems of ordinary koristuvachіv, as for the great rakhunka it is interesting not to become wicked. At the time of the establishment of a program, it is received from the main Internet resources. Bagato koristuvachiv at the start of the pre-installation to prevent the anti-virus system from being changed, and in the process of installation it does not exaggerate the position of the installation of additional PZ, panels or plug-ins for browsers, but it’s possible to be called.
Diseases of viruses and trochas of history
In the main contaminated type, the most insecure virus-encryptor No_more_ransom is classified as encrypting tools or blocking access to them. As a matter of fact, all such high-quality programs should be up to the category of healthy ones. In other words, the evil-minded people are trying to decipher the information in the city for deciphering the information, but without the cob programs, the process would be unhappy. Chastkovo so won і.

Ale, if you dig into history, you can remember that one of the most recent viruses of the type, however, didn’t play it for pennies, but the I Love You applet, which encrypted the core of the music file in the multimedia systems. Decryption of files sent to the encryption virus at that time was ill-advised. Infection itself from the current threat can be combated elementary.

Along with the development of the viruses themselves, or the encryption algorithms, which can be victorious, it isn’t easy to use. Why are there no middle-sized viruses - here you і XTBL, і CBF, і Breaking_Bad, that [email protected], І shche kupa of any guide.
Technique for pouring on files of koristuvach
The first time a large number of attacks were used against RSA-1024 algorithms based on AES encryption using the same bit, the same encryption virus No_more_ransom, based on RS48 decryption technologies, based on RS48 encryption technology.
Problems of decryption vikoristovuvanikh algorithms
The reason is that the fortuitous system of decryption in front of such a problem appeared to be powerless. Decryption of files sent to the encryption virus on the basis of AES256 can still be accepted, and it is practically impossible for all vendors to use their hands for clearing up the key security. The price, before the speech, was officially confirmed by the employees of Kaspersky Lab and the Eset company.

In the most primitive version of koristuvachev, having called in to the service of the driver, the encryption file and its original will be sent to the encryption service for verifying and carrying out further operations for the encryption algorithm and updating methods. Ale, as a rule, a great result is not given. Ale virus-cipher deciphering the files can and itself, as you get involved, for the mind, but the victim will wait with the minds of the evil-minded and pay the singing bag in a penny equivalent. Protect such a setting of food wiklikє zakonі sumnіvi. The first axis to the chomu.
Virus-encryption: how will it be encrypted?
It’s possible to wait for the payment, hackers activate decryption through the remote access to their virus, which is to sit at the system, or through a supplementary applet, as long as the virus is visible. Viglyadaє tse bіlsh nіzh sumnіvno.
I would like to be aware of the fact that in the Internet there are mostly fake posts about those, who, moving, consuming money, have been rallied, and the data have been successfully updated. It's all nonsense! And rightly so - de guarantee, when the virus-encryption device is paid for, the system will not be activated again? The intelligence of the psychology of evil-doers is not important: having paid once, you will pay a new name. And if there is a particularly important information on the standard of specific commercial, scientific and technical outlets, the owners of such information are ready to pay for the price, the abi files are overpriced and safe.
First zasib for usunennya load
Such a virus-encryption behind its nature. Yak vil_kuvati that decipher the files? So there is no way, as there are no others, as you may not want to help. Ale can try.
It is permissible that the system has a cipher virus. Yak vilykuvati infected files? First, I went through the destruction of the scanned system without storing the technology of S.M.A.R.T.

Bazhano does not use a standard scanner, which has already missed a threat, but rather has a portable utility. The optimal option is to install the Kaspersky Rescue Disk from the disk, as you can start up to the ear of the operating system.
Altogether less than half of the right, splinters with such a rank can be used to deprive the virus itself. And from the decoder it will be more foldable. Ale about tse trochas zgodom.
Є One more category, for example, there are encrypted viruses. As soon as you decipher the information, it will be said ok, but when you stop thinking about it, the smell can be brought up in the system, in the eyes of the officially installed programs that do not know how
In a wide variety of ways, the program of components has been distributed, and it will be seen as standard. However, it is necessary to pay respect to those who do not see the standard Windows uninstaller and I haven’t seen all the files by the programs. Zokrema, the ransom encryption virus Building folders in the root directories of the systems (link the Csrss directories, de є one-change the csrss.exe file). In the main roztashuvannya folder Windows, System32 or directories of koristuvach (Users on the system disk) are selected.

In addition, the encryption virus No_more_ransom will prescribe in the register of vlasnі keys from the viewer on the basis of an official client Server Runtime Subsystem service, so that it is possible to introduce into Oman, some of the server service is responsible for receiving requests for reasons. The key itself is located in the daddy Run, which can be accessed through the HKLM key. Zrozumіlo, I will see such keys, I will hand over them.
It will be simpler, you can quickly use the utilities to read iObit Uninstaller, as it will automatically send out the surplus files and keys to the reestr. Ale tse the simplest, how you can grow.
Solution, promoted by anti-virus PZ retailers
Decryption of the encryption virus, as it can be used, can be carried out for the additional help of special utilities, if for the obviousness of the technology with the key 2048 or 3072 bits on them especially Blame the presence of til virus, as it has been seen to the full).

Probably it’s possible. Use the RectorDecryptor and ShadowExplorer software. Yak to vvazhaєtsya, from where nothing short was opened. A problem may arise from the fact that when you try to get a decoder, the guarantee that the files will not be seen will not be visible. So, if you don’t get confused about the virus from the ear, if you try to decipher it, you will be doomed to failure.
In addition to the visible encrypted information, it can be death - the whole system will appear unremarkable. In addition, the current virus-encryption device for the building is not only on the data, but on the hard disk of the computer, or on the files in the grocery store. And then the decision to update the information is dumb. Before that, as it appeared, the services were lacking in an effective way to get used to it (the same one in Windows 10 OneDrive, which is fed directly from the operating system).
Cardinal solution of the problem
As it seems, most of the modern methods do not give a positive result when infected with certain viruses. Apparently, if the original is sent to the file, it can be submitted for examination before the anti-virus laboratory. True, even more earnestly, those who are ordinary koristuvach will be opening the backup copies of the data, as if they are saved on a hard disk, they can conceive of a flood of awkward code. And about those, well, that you will not find any inappropriateness, you copy information on a known note, do not go astray.
In such a rank, for a cardinal solution of the problem of visnovok, one should ask for oneself: outside the format of the Winchester and all the logical distributions from the visible information. What about robiti? To get a donation, if you don’t want to donate, the virus or your self-protected copy will be activated in the system again.
For those who do not want to pick up the Windows systems themselves (rely on the formatting of virtual distributions, you will see a fence when you try to access the system disk). More beautifully, you can use optical media to download LiveCD files, or install distributions, for example, the Media Creation Tool for Windows 10.

Before starting the formatting for clearing the virus from the system, you can try to update the system components through the command row (sfc / scannow), but in the plan, decrypting and unlocking the system components cannot be detected. To that format c: - Alone is the correct decision, befitting you tse chi ni. Only this way and it is possible to add some kind of threat. It's a pity, inakshe - niyak! To navigate the liking with standard methods, how to use more anti-virus packages, to appear powerless.
Replace pislyamov
At the plans of the visitor, you can ask for it, you can say only those that are the only one and the same universal solution, so that such a kind of threat for the current day isn’t obvious.
It’s unreasonable, why did the creation of algorithms based on 1024-, 2048- and 3072-bit encryption pass over quietly, why should we be sure to deal with such technologies? Even on the current day, the most promising and the best ones will use the AES256 algorithm. Respect! 256! The system is not suitable for every virus, as it appears, and changes are not suitable. What are you talking about trying to decipher their keys?
Tim doesn’t mensch, you can simply add it to the system. The simplest option would have to reconcile all incoming information with attachments in Outlook, Thunderbird programs and other mail-order clients with antivirus immediately after rejecting and, in any case, not opening the investment before reconnecting. It is also a matter of respectfully reading the proposition that a supplementary PZ was installed during the installation of certain programs (make the stench written in a different font, or disguise it for the standard type of Flash Player update, or whatever). Components of multimedia are best viewed through the official site. It’s just like that, and it’s possible to overshoot the penetration of such threats to the system. The inheritance can be absolutely non-communicable, as it is vrahuvati, which is viral to the type of mittto spread out in the local hedge. And for companies, such a turnover can become a real crash of all repairs.
On the contrary, the system administrator is not guilty of sitting idle. The program will help you get the better of such a situation. The same firewall (mіzhmerezhevy screen) is not guilty of being programmed, but "zalіznim" (obviously, with a supportive PZ on board). First, it’s easy to save money on anti-virus packages. It's better to buy a licensed package, and not install primitive programs, as you will not be able to get away from a real watch from a real person behind the words of a developer.
And as soon as a threat has penetrated into the system, the last one is guilty of including the vision of the virus itself, and only then try to decipher the data. In ideals - outside the formatting (respect, not for cleansing the snake, but on top of that, because of the updates, for example, by replacing the existing file system, zapping sectors and records).
Modern technologies allow hackers to consistently fully understand the methods of mining one hundred percent of the earliest koristuvachіv. As a rule, for cihs the goals are victorious through the program of security, which gets into the computer. It is especially not safe to use encryption viruses. The threat of a polyag is in the fact that the virus duzhe shvidko rozpovsyudzhutsya, encrypting files (koristuvach simply cannot see a document). And if it’s easy to finish it, then it’s better to decipher the data.
Robiti, if virus encrypted files on a computer
Knowing the attacks of the cipher can be skinny, you are not insured to find the criminals, which are worth the effort of the anti-virus program. File encryption Trojan horses are presented with a different code, which may not be used by the antivirus. Hackers find it easy to attack in some other way of a great company, as they did not tell about the necessary information retrieval. Once you have entered the encryption program online, you need to see a number of entries.
The main signs of the infection are the main robot of the computer and the change in the name of the documents (you can check the work table).
- Restart the computer, zupiniti encryption. For an hour, do not confirm the launch of unknown programs.
- Launch antivirus, if you are not aware of the encryption attack.
- Update information in any kind of files to help you with new copies. In order to know їх, display the "Power" of the encrypted document. Tsei way of working with encrypted data from the expansion of Vault, about information on the portal.
- Add a utility to the last version to fight against encrypted viruses. Nayeffective proponation of "Kaspersky Lab".
Viruses-ciphers in 2016: put it on
When fighting against a virus attack, it is important to be smart, as the code often changes when a new attacker is added to the anti-virus. It’s obvious that the program will take an hour, if the dealer doesn’t update the base. We bully found the most insecure virus-ciphers for the last hour.
Ishtar Ransomware
Ishtar is a cipher, like a vimag for a koristuvach penny. Virus buv of the note of 2016 rock, infecting the majesty of the number of computers from Russia and Russia. Extend for additional email-applications, in which to go to the attachments of documents (installers, documents too). Infected by the Ishtar cipher, they inherit the prefix "ISHTAR". The process is running a test document, which means that it should be returned for rejecting the password. The malefactors will be able to pay for a new fee of 3000 to 15000 rubles.
I don't care for the Ishtar virus at the one who doesn't have a decoder on this day, which is supposed to help bi koristuvach. Companies that are busy with the anti-virus protection gate will take an hour to decipher the entire code. The infection can be deprived of the most important information (which is especially important) on the border of the nose, checking the way of utilization, building up encryption of documents. It is recommended to reinstall the operating system.
Neitrino
The cipher Neitrino appeared in the open spaces of Merezhi in 2015. The principle of attack is similar to those of the same category. Change the name of folders and files, adding "Neitrino" or "Neutrino". Deciphering the virus is important to assume - not all representatives of anti-virus companies will undertake the task, if they use the even folding code. Deyaky karystuvachi can help to update a new copy. To click the right button for encrypting the document, go to "Power", tab "Front versions", click "Update". We will not be busy with the quick and easy-to-use utilities from Kaspersky Lab.
Wallet or .wallet.
The virus encryption Wallet appeared for 2016 rock. In the process of infection, the name of the tribute to "Im'ya. wallet "abo podibne. Both and a large number of viruses-encryption agents, who use the system through the attachment in the electronic sheets, as the wicked ones are used. Oskilki the threat of a winnickl recently, anti-virus programs do not support it. When I write a cipher, I will send a message to the shakhrai. In Danish hour, the anti-virus software developers started to work over the encryption code of the virus-encryption device [email protected] Koristuvacham, who know the attacks, become deprived of chekati. As important as it is, it is recommended to save it for the new accumulation by cleaning the system.
Enigma
The Enigma encryption virus has started to infect the computers of the Russian clerks for the first time in April 2016. The model of encryption AES-RSA will be victorious, as this year will be used by a large number of viruses-vimagachiv. On the computer, the virus penetrates for the help of the script, such as launching the coristuvach, having opened the files from the adult electronic sheet. Dose a non-universal way to fight with the Enigma encryption tool. You can ask for additional help on the official website of the retailer if you have a license for antivirus. There was also a small "loophole" - Windows UAC. Iakshko koristuvach natisne "Hi" at vіknі, as it appears in the process of being infected with a virus, you can then update the information for additional copies.
Granit
The new virus-cipher Granit has appeared in the Merezhi Vosseni 2016 rock. Infection is seen for such a scenario: a startup installer that infects and encrypts all data on a PC, as well as connected accumulators. Fighting from the virus foldably. For the sake of visualization, you can use the special Kaspersky utilities to speed up the code; You can, in addition, update the previous version of the tribute. Outside, deciphering can be done by a specialist, who is a great dosvid, but a servant is dear.
Tyson
There was a lot of room for buv. Є Expansions of the existing no_more_ransom encryption tool, about which you can read on our website. Consume on personal computers from electronic mail. The attack was overwhelmed by corporate PCs. Virus of a text document with instructions for unblocking, pay "wikup". The Tyson cipher didn’t show up, so there’s no key to unlock it. One way to update information is to turn the front version, as long as the stench did not recognize the virus. You can, viciously, risky, having transformed a penny into the instructions of the evil men of the rakhunok, ale dumb guarantors, how you can deny the password.
Spora
By the ear of 2017, the rock is low koristuvachiv became a victim of the new encryption Spora. Behind the principle of robotics, one does not strongly recognize oneself from one's brothers-in-arms, but we can also boast of professional visitors: the instructions are clearer and more beautiful. The Spora virus-encryption device was created in Movi C, and I used RSA and AES to encrypt the victim's tribute. The attack was conceived, as a rule, by computers, on which the accounting program 1C was actively vikorystovutsya. Virus, looking like a simple rakhunku in the .pdf format, the message of the pratsivniki companies of launching yogo. Likuvannya is not known yet.
1C.Drop.1
Tsey virus-encryption for 1C came into force in 2016, destroying the robot bagatokh accountant. It was developed specially for computers, on which vikoristovuєtsya program for securing 1C. Play for the additional file in the electronic sheet to the PC, proponate the program to the owner. Yaku without pushing the button, the file is encrypted. Above the deciphering tools, the Dr.Web faxes have not yet been solved. This is due to the folding code, which can be found in some modifications. With the help of 1C.Drop.1, we have become less robust and more important documents archiving on a regular basis.
da_vinci_code
A new cipher with an unknown name. Z'avivsya virus attachments 2016 rock. From the forerunners, it will be shown by changing the code and using the strong encryption mode. da_vinci_code infects the computer of a zavdyaki to a vikonavch addon (reach out to the electronic sheet), which is a self-launching koristuvach. The cipher "da Vinci" (da vinci code) is copied to the system directory and registry, automatically starting when Windows is turned on. The skin victim's computer will be given a unique ID (additional help to correct the password). It is practically unwise to decipher the data. It is possible to pay pennies to the evil-minded, but not the guarantor of the rejection of the password.
[email protected] / [email protected]
Two e-mail addresses, which are often supported by cipher viruses in 2016. The stench itself serves as the ring of the victim for the evil one. Addresses were added to the latest types of viruses: da_vinci_code, no_more_ransom and so far. In the region, it is not recommended to call, and also give pennies to the shahrays. Coristas are great zalishayutsya without passwords. In such a rank, showing off, the ciphers of the evil-minded people, bringing the deaths.
Breaking Bad
Appearing on the cob 2015 rock, ale actively broadened the leash for the rock. The principle of infection is identical to those of ciphers: installation of the file from the electronic sheet, encryption of the tribute. Get an anti-virus, call it up, do not work with the Breaking Bad virus. This code cannot be overlooked by Windows UAC, so it can be updated to the front version of documents. The decoder has not yet been presented by the Zhodna Company, which has developed antivirus software.
XTBL
In addition to the extensions, the cipher, as if having made some troubles to the koristuvacha. Having consumed on the PC, the virus for a little chillin changes the extension of the files to .xtbl. A document is being created that has a malevolent character vimagak koshtiv. The XTBL virus cannot protect the files for updating the system, but you can turn important documents. The virus itself can be seen with programs, ale deciphering the documents even more smoothly. Yaksho is a licensed antivirus, speed up with technical support, adding data to the infected data.
Kukaracha
Cipher "Cucaracha" Virus with the name given to the file of the corystuvach for the additional RSA-2048 algorithm, which is very flexible. Kaspersky Anti-Virus has designated Trojan-Ransom.Win32.Scatter.lb. Kukaracha can be seen from a computer, so that the infected does not know the documents. Protein infected on the current year is practically uncomfortable to decipher (even a tedious algorithm).
Yak pratsyuk virus-encryption
Isnu bezlich encryption, ale the stink of praying for a similar principle.
- Vluchennya to a personal computer. As a rule, zavdyak attached file to the electronic sheet. Installed from his own insight himself koristuvach, having shown the document.
- Infected files. Enciphering is possible for all types of files (stale as a virus). A textual document is being created that has a contact with malicious people.
- All. Koristuvach can not get access to the document.
Help fight from popular laboratories
A wide expansion of encryption devices, which are the most unsafe threats for these clerks, has become a shipment for many anti-virus laboratories. Kozhna is a popular company, which has given its programs programs to help them struggle with ciphers. In addition, they are rich in additional help from the decryption of documents in a secure system.
Kaspersky and encryption viruses
One of the most recent anti-virus laboratories in Russia, which promoted this year's found for the fight against viruses-vimagachi. The first transition for the encryption virus will be installed in Kaspersky Endpoint Security 10 with the remaining updates. Anti-virus simply does not miss a threat to the computer (frankly, the new version may not be zupinite). To decipher the information, the roster presents at once a collection of non-standard utilities:, XoristDecryptor, RakhniDecryptor and Ransomware Decryptor. Smell add a shukati virus and choose a password.
Dr. Web and encryption
The laboratory recommends that you use an anti-virus program, the main feature of which has become the backup of files. Schedule with copies of documents also stolen from unauthorized access by malicious persons. Vlassniks of the licensed product Dr. Web, there is a functionality available for additional help on technical support. Of course, there is no reason to suspect a prototype type of threat.
ESET Nod 32 and encryption machines
Ostoron was not lost to the company; In addition, the laboratory has recently released a blanket-free utility with up-to-date databases - Eset Crysis Decryptor. The retailers declare that there is more help in the fight against the new cryptographers.
It will remain an hour to spur the splash of activity of the new generation of high-profile programs. The stench appeared to end up a long time ago (6 - 8 rock_v that), ale the tempi їkhny vprovadzhennya reached their maximum at once. All parts can be nailed to those who have encrypted files.
At the same time, it’s not just primitive schools of thought, for example (I’ll see a blue screen), but a series of programs aimed at specific, as a rule, accounting dues. Stink to encrypt all files that are visible, which are located between accessibility, including data from 1C accounting, docx, xlsx, jpg, doc, xls, pdf, zip.
Especially nezglyanutyh viruses
Vona polyagaє in that, when the RSA key is stuck, which binds to a specific computer of a koristuvach, that is a universal decoder ( decryptor) Відсутнє. Viruses, activated in one of the computers, may not work in the first.
There is also a need for the fact that there is more fate in the Internet distribution of alarm programs (bilders), so that they allow the development of such a virus to appeal to kulkhackers (specialties that I take into my mind as hackers, but I do not.
Nina came up with the necessary modifications.
Sposib vprovadzhennya dannyh shkidlivikh programs
Dealing with viruses is carried out in a straightforward manner, call it, at the accounting department of the enterprise. A selection of e-mails to see frames, accountants from such databases, such as, for example, hh.ru. Let the sheets be pulled out. Smell most often take revenge on the prohannya schodo taken on the singing posadu. Before such a sheet with a resume, all in the middle is a real document with an implanted OLE-object (pdf-file with a virus).
In situations where the accounting professionals immediately launched the whole document, to re-enroll it, it was also displayed: the virus was renamed and encrypted, and then it was self-quarantined.
Such a sheet, beckon, is adequately written and sent from a non-mailbox (іm'ya submitted to a signature). The vacancy must be supplied from the professional activity of the company, through which you will not be able to find out.
Not licensed "Kaspersky" (anti-virus program), or "Virus Total" (online service for converting a deposit on a virus) can not secure a computer from a wide variety of problems. In some cases, anti-virus programs when scanned to see that the investment has Gen: Variant.Zusy.71505.

Yak uniqueness infected with cim virus?
Slide to revise the skin otrimaniy file. Especially respect comes to Word documents, as they may be zaprovadzheni pdf.
Options for "infected" leaves
Їx to finish the bagato. Nyposhirenіshі options, like a virus encrypting files, presented below. All types of e-mail must have the following documents:
- Depending on the process of looking at the ship's call filed for a specific organization (the list will be able to reconsider the data for an additional transition for the meaning of the order).
- Sheet from the Supreme Arbitration Court of the Russian Federation about the contraction of the Borg.
- As a result of the improvement of the foreign trade from Oschadbank.
- Regarding the fixation of the rules of the road collapse.
- A sheet from the Collection Agency for the maximum possible payment line.
About file encryption
Once the infected appears in the root papacy of the C disk. In all directories, files of the SHO_ROBITI.txt, CONTACT.txt type will be changed with the enclosed text. There they will inform you about the encryption of your files, you need to know about the extra cryptographic algorithms. And so it’s about the lack of efficiency in the storage of third-party utilities, so how can you bring the files to the residual waste, well, at your own house, before it’s uncomfortable to decipher them.
It is recommended to run the computer off the stand. The new one has been given the hour to take the given key (call me 2 dobi). The exact date is spelled out, if it were to be ignored.
For example, I need an e-mail. It also says that the koristuvach is guilty of giving his ID, and that be it from the lower one, you can bring the key to the elimination, but itself:

How to encrypt files encrypted by a virus?
This kind of encryption is even more difficult: the file is assigned the same extension, yak perfect, nochance and ін.
There is another way, as to update a file encrypted by a virus, albeit it’s not necessary to go to all viruses, it’s still necessary to use the downloaded exe all at once from a complex, challenging program, so that it’s not easy to achieve a difficult journey on your own.
Passing a virus to the introduction of a special code is an insignificant change, so the file is at the moment already a decoder (the code is like, bi-moving, malicious messages will not be needed). The essence of this method is to fit empty commands into the penetrated virus (the very moment the code is entered). The result is a fast program to start decrypting files and changing files by itself.
The skin environment has its own special encryption function, it cannot be encrypted through a third-party executor (file in exe format), otherwise it is possible to try and use the function, for which all WinAPIs are needed.

files: what robiti?
To carry out the decryption procedure, you need:

Yak uniknuti vtrati tribute through razlyanute shkidlive PZ?
For the nobility, in a situation where the virus has encrypted files, it takes an hour for the process to decrypt. An important point є those who have a great awkward software program that are safe, so that they can save some of the files, as they quickly know the computer (turn the plug from the socket, plug in the laptop, plug in the laptop, number of files in previous extensions.
Once again, after the admission, the smut - there is no backup copying, but not in the folder, not on the knowledgeable nose, insertions into the computer, since the modification is given to the virus to get to the whole thing. Varto zberigati backup on your computer, on Windows, which is not always connected to the computer, and in the dark.
All documents that arrive at the mail from unidentified individuals (in the case of a resume, invoice, Decide from the Supreme Arbitration Court of the Russian Federation to pay and on.). You do not need to run it on your computer (for these purposes, you can see a netbook, which does not take revenge on important tributes).

Shkіdliva program * [email protected]: ways usunennya
In a situation, if the virus is used for encrypting the files cbf, doc, jpg, etc., there are three options for the development of the pod:
- The easiest way to get rid of it is to see all the infected files (which is understandable, since the data is not particularly important).
- Go to laboratory anti-virus programs, for example, Dr. WEB Send to the distributors of the infected files in one go from the key for decryption, which is located on the computer as KEY.PRIVATE.
- Nayvitratn_shy sposib. Win transfer - payment of sums for decrypting infected files. As a rule, the partiality of the service servant in the fringes is 200 - 500 dollars. USA. It’s quite acceptable in the situation, if the virus encrypted the files of the great company, in the current day of the Suttau information, and the program can be very slow in a few seconds to create a colossal school. At the same time, payment is the best option for updating infected files.
In some effective and additional option. Yaksho virus encrypted files ( [email protected] _com or іnshe shkіdlive PZ), you can do it for a few days.

RectorDecryptor deciphering program
Yaksho virus encrypted jpg, doc, cbf files, but a special program can help. For a whole lot of information, you need to go to auto-mailing and enable everything except antivirus. It will be necessary to re-enable the computer. Take a look at all files, see them. In the field, the name "Team" is indicated for the rooting of a specific file (respect to come up with varto programs, but do not miss the signature: virobnik is not a danny).
We need to clear the browser caches, time folders (for the entire CCleaner program).
Before you start decrypting, you need to sign up for the assigned program. Then you can run the button "Read the change", having changed the files and expanded them. In the current versions of the central program, you can use the "View" button to remove the infections. All files will be encrypted.
When the utility is done, it will automatically reconcile all computer data, including files, which are located on the supplied stitching disk, that is decrypted. The whole process of renewal can be trivial for a few years (it’s hard to pay off a robot and a computer’s speed code).
The results will all be encrypted in the same director, de noces were known from the collection. On completion, you will be deprived of seeing all explicit files from the extensions, for which you can tick the box "View encrypted files for successful decryption" by pressing the button "Change override parameters". However, it’s better not to put it, because once the files have been decrypted, you can smell the stench, and then you will get a lot of new ones.
Otzhe, if the virus encrypted the doc, cbf, jpg files, then it’s not necessary to follow up with the payment code. Perhaps, I don’t know.
Nuances of visualization of encrypted files
When trying to copy all the generated files for the addition of a standard joke and a little more visual, you can freeze and trust your computer's robots. The connection with the cim for the given procedure is speedy with a special one. When launching, it is necessary to enter the following:<диск>:\*.<расширение зараженного файла>"/ F / s.
Obov'yazkovo require such files, like "Read-me.txt", for which in the same command row it should mean: del "<диск>:\*.<имя файла>"/ F / s.
This rank can mean that if the virus has changed and encrypted the files, then it’s not right to buy a key from malicious users, it’s a good idea to try to solve problems independently. Better than putting a penny into the app with special programs for decrypting encoded files.
Nasamkinets varto nagadati, but in the tsy statty the food was seen besides, as deciphering the files, encrypted by the virus.
Today's computers and laptops are getting more and more stuck with the help of high-speed programs, such as receiving files with encrypted copies. Vlasne, tse virus. One of the most unsecured ones in the series is the XTBL encryption machine. Who is also a shkidnik, how do you use a corystuvach in your computer and how can you update the information?
It is an XTBL encryption machine and you can take it to the computer
I have seen files on my computer or in my laptop with the same name, which may be expanded. Win is hostile to all versions of Windows. It is practically unrealistic to unscramble some files on its own, even the program is in a hybrid mode, for any key driver is simply uncomfortable.
Infected files are stored in system directories. Records are added to the Windows registry, which automatically launch the virus when the OS skin starts.
Practically all types of files are encrypted - graphics, texts, archives, postage, video, musical and in. Windows is getting sick of pratsyuvati.
Yak tse dіє? Windows launches an XTBL encryptor from a scan of all logical drives. The students are turned on to the smudges and grooves, rostasovani on the computers. As a result, files are grouped for extensions and then encrypted. In such a rank, all the valuable information, as it is spaced out in the folders of the koristuvach, becomes inaccessible.
 Axis taku a picture to change a picture of a file
Axis taku a picture to change a picture of a file
When the XTBL encoder is injected, the file expands. Now I will call the pictogram of an empty sheet and I will name it from the end.xtbl to replace the image with the text in Word. In addition, on the work table there appears to be a kind of instructions for updating the encrypted information, which allows you to pay for unlocking. It’s not a good thing, like blackmail from a vikupu.
 You can also hang out at the work desk of your computer
You can also hang out at the work desk of your computer
Expansion of the XTBL encryption device, call it via e-mail. The list contains attachments for files or documents infected with a virus. Shakhrai privablyuє koristuvacha with a barvy title. All are afraid in order to be sent, in which to go about those who, for example, played a million, bulo vidkrito. Do not react to such an occasion, because it’s a great risky, so the virus will come back to your OS.
Chi є ability to update information
You can try to decipher the information by speeding up with special utilities. However, there is no guarantee that you can get around the virus and update the files.
At this time, the XTBL encryption machine is a complete threat to all computers from the installed Windows operating system. Navigate the known leaders in the fight against viruses - Dr.Web and Kaspersky Lab - is not 100% virgin food.
Virus and update of encrypted files
Є Some people see viruses, they get encrypted and locked files or update them in front of the front copies.
Reinventing an infected computer
As soon as you are spared to grab an ear, appear on your computer files with .xtbl extensions, and the process of a forgiven infection is really interrupted.

Kaspersky Virus Removal Tool for XTBL encryption
All of the other programs go into operation in the operating system, before they are launched in safe mode with the option of pre-setting the driver. At the same time, the virus seems to be simpler, only the smallest number of system processes required to start Windows are enabled.
To lock the safe mode for Window XP, 7 hours before the system starts and continuously press the F8 key and when the menu appears, select the new item. In case of Windows 8, 10, restart the OS by pressing the Shift key. During the launch process, it will be displayed promptly, so that the required option of a bake-free installation can be vibrated.
 Vibration of the non-fired mode due to the interlocking of the net drivers
Vibration of the non-fired mode due to the interlocking of the net drivers
The Kaspersky Virus Removal Tool program miraculously detects the XTBL encryption tool and sees the type of virus. Launch the rewiring of the computer by pressing the open button to write the programs. When the scan is complete, you can see the files.
 Launching the conversion of the computer for the XTBL encryption in Windows OS from the more visible virus
Launching the conversion of the computer for the XTBL encryption in Windows OS from the more visible virus
Dr.Web CureIt!
The conversion algorithm that is seen to the virus is practically impossible to see from the previous version. Scan all logical drives for additional utilities. For the whole of it, it is enough to get rid of commands by sending programs to launch. After finishing the process, you can get rid of the infected files by pressing the button "Changecode".
 Knowing Script Files for Windows Scanning
Knowing Script Files for Windows Scanning
Malwarebytes Anti-malware
The program will ask you to step by step change your computer to the presence of high-quality codes and to know them.
- Install and run the Anti-malware utility.
- Viber at the bottom of the window is the item "Launch a changeover".
- Check the end of the process and mark the checkboxes from the infected files.
- See vibran.
 Vyavlennya vyavlenikh pіd hour of revision of shkіdlivnyh files in XTBL-encoder
Vyavlennya vyavlenikh pіd hour of revision of shkіdlivnyh files in XTBL-encoder
Online script-decoder from Dr.Web
On the official website of Dr.Web, there is a tab with a change in the file decryption script at the sidebar. Slid vrahovuvati, as fast as the decoder in the online mode can deprive you of karystuvachi, on the computers of any installation of the anti-virus rozrobnik.
 Read the instructions, memorize everything you need to press the button "Required"
Read the instructions, memorize everything you need to press the button "Required"
Utilita-decoder RectorDecryptor from Kaspersky Lab
Kaspersky Lab will handle encryption of files. On the official site, you can add the RectorDecryptor.exe utility for Windows Vista, 7, 8 by following the menu "Pidtrimka - Likuvannya and decryption of files - RectorDecryptor - Yak decrypt files". Run the program, change it, so that you see the encrypted files, vibrate the item.
 Conversion and decryption of files infected with XTBL encryption
Conversion and decryption of files infected with XTBL encryption
Updating encrypted files from backup
When fixing from Windows 7, you can try to update files from backups.

ShadowExplorer for updating encrypted files
The program is portable, so you can add it to your account.

QPhotoRec
The program is specially designed for updating software and files. Vikoristovuchi is prompted by the algorithms, utilities know that all the information is consumed until the final turn.
The QPhotoRec program is kosteless.
It’s a pity, є only the English version of QPhotoRec, a little awkwardly, the interface is intuitively intelligent.
- Run the program.
- Designate logical drives from encrypted information.
- Press the File Formats button and OK.
- Vibrate for the help of the Browse button, which is installed in the lower part of the display window, at the same time saving files and launching the update procedure by pressing Search.
 QPhotoRec updated files, seen by the XTBL-encryptor and replaced by the authoritative copy
QPhotoRec updated files, seen by the XTBL-encryptor and replaced by the authoritative copy
Yak deciphering files - video
What does not slid robiti
- Nicholas do not be robust, for those who do not have a whole lot of fun. It’s better to ask a specialist from the service center, or to bring the computer there.
- Do not display any email messages from an unidentified vendor.
- In the case of a zhodniy, it is impossible to follow the lead of the evil-blackmailers, in the meantime, they will overrule them. The result is tse, shvidshe for everything, not to give.
- Do not manually change the extended encrypted files and do not have to wait and reinstall Windows. You can, give in to know the decision, how to correct the situation.
Prevention
Try to get a new attacker from the penetration of the XTBL encryptor and other viruses into your computer. Prior to such programs should be:
- Malwarebytes Anti-Ransomware;
- BitDefender Anti-Ransomware;
- WinAntiRansom;
- CryptoPrevent.
Unimportant to those who all stink є English, it's easy to finish with such utilities. Launch the program and vibrate the system in the installations.
 Launching programs and vibir rіvnya zahistu
Launching programs and vibir rіvnya zahistu
If you happen to be stuck with a virus-vimagach, which encrypted files on a computer, then, obviously, you can't get angry. Try the method of updating the updated information by the way. Most often it gives a positive result. Do not confuse the XTBL encoder with unreconfigured programs from unauthorized vendors. You can even better manage the situation. Whenever possible, install one of the programs on the PC to detect the robotic virus, and then carry out the planned scanning of Windows for the manifestation of complex processes.
“Vibachte, scho they pounded, ale ... your files are encrypted. Then you can cut off the key for decryption, and then transfer the pennies to a hamman ... Your danny will be irrevocable. You have 3 years, an hour of pishov. " It’s not hot. Virus-encryption - the threat is more than real.
Let's talk today, that they are shkidliv programs-ciphers, that they have expanded into the rest of the rock, that they will be able to get rid of an infected person, as if they were a computer and would probably want to get involved, as well as how they would be taken out of them.
Everything is encrypted!
Virus-encryptor (encryptor, cryptor) is a special type of shkidlivyh program-vimagachiv, whose activity field in the encrypted files of the clerk and the subtle vimogi of the vikupiti with decryption. Sumi wikupu can be repaired here for $ 200 and dozens and hundreds of thousands of green papirs can be reached.
For some reason, only Windows-based computers have become aware of the attacks of the malicious class. The current habitat has expanded to, well, it was stolen by Linux, Mac and Android. In addition, the type of versatility of the encryptors is gradually growing - one by one there are new items, such as how to make the light. So, the winners of the "shhreshuvannyu" classic Trojan-cipher of the hedgehog (shkіdlivaya programs, how to expand with hems without the active participation of koristuvachіv).
Petya and Bad Rabbit weren't the least of the WannaCry songs. If you bring the "cipher business" to the owners of non-falsification, then you can be singing, but the stench will not stop.

The grandfathers are more ciphering, as they especially beat the light in the last 3-5 years, using strong cryptographic algorithms, which are ill-fooled by brute-forcing keys, or by any other means. The only way to update a dan is to speed up with the original key, which can be used to buy the evil ones. However, to find a pererahuvannya him the necessary sum is not a guarantor of the key. Zlochintsi do not have time to open up their secrets and spend potential gains. What kind of sense of viconuvati obitsyanki, what are the pennies in them?
Holes rozpovsyudzhennya viruses-encryptors
The main way of getting shkіdlivostі on the computer of private koristuvachіv and organіzatsіy - electronic mail, more precisely, to the end of the file sheets and data.
The application of such a list of signs for "corporate clients":

- "Terminovo to repay borg for a loan."
- "Pozovna petition filed pending trial."
- "Pay a fine / deposit / tribute".
- "Dorahuvannya utility bills".
- "Oops, ceti in the photo?"
- "Lina asked for a term" to send "etc.
Wait a minute, only the knowledge of koristuvach is put to such a sheet with alertness. Most of all, do not be overlooked, as a result of your investment, you can start a great program with your own hands. Until speech, unaffected by the shouts of the antivirus.
It is also for the extended encryption operators to actively use the following methods:
- Social framing (linking from oblivious records of known and unfamiliar people).
- Shkidliv and infected web resources.
- Banner advertising.
- Rossilannya through messengers from evil accounts.
- Website builders and cracks.
- Site for grown-ups.
- Stores for additional content.
Providers of viruses-encryptors are not often used to provide high-quality programs, springs, display advertisements and Trojan-backdoors. Remaining, vikoristovuyuchi in the system and the PZ, additionally help the inhabitants of the village to correct the access to the infected annex. Launching a cipher in such vipads do not wait an hour to start with the potentially unsafe actions of a koristuvach. Once the backdoor is in the system, the malefactor can penetrate the attachment, be it a mit, and start encryption.
For the infection of computers in organisations (even the stench can be seen more, lower in home-made koristuvachiv), special methods are developed. For example, the Petya Trojan penetrated the attachment through the software update module MEDoc.

Ciphers with the functions of hedgehogs, as they said, are expanded by hems, the Internet is growing, through the urgency of the protocols. I can get infected with them, do not shy away from anything. I do not have a problem with running Windows OS, but it is very easy to see some new bugs.
They are evil, such as WannaCry, exploiting the urgency of 0-day (zero day), that is, I don’t know about which vendors of systems. It’s a pity, it’s a pity, it’s a bit of a problem, but you’ll eat up to the number of sufferers, which doesn’t reach 1%. For what? The fact is that, with a shkidlive program, you cannot immediately infect all infested cars. First and foremost, new victims, system dealers will come up with new updates.
Yak walk the cipher on an infected computer
The process of encryption, as a rule, is not repaired, but if the signs become obvious, the data are already clear: at that hour, the scrambled encrypted everything it could reach. Some of them can be mentioned, as at the files at the time of the change of the father.
This appears in the files of a new, and in some other extension, for which the stench ceases to appear, I will turn up the case for the legacy of the attack of the encryptor. Until the speech, expanded, how to get rid of the hidden objects, start to give in to the identification of the malware.
Butt, which can be expanded encrypted files :. xtbl, .kraken, .cesar, .da_vinci_code, [email protected] _com, .crypted000007, .no_more_ransom, .decoder GlobeImposter v2, .ukrain, .rn etc.
Variants of the masa, and even tomorrow there will be new ones, so that everything is especially meaningful is not important. For the type of infection, it is sufficient to develop a sprat from a wider sound system.

Some of the symptoms that can be posed on a cob of encryption are:
- Appearing on the screen for a fraction of a second, the screen of the command row. Most of the time, it is normal to see the system when the system is installed and the program is in place.
- Power up UAC for launching as programs, as you didn’t get to it.
- Rapid rewiring of the computer with the help of a simulated robot and system utilization of disk rewiring (there may be some options). Before the hour of reconsideration, the encryption process will take place.
For the successful completion of the awesome operation on the screen, there will be new threats to the visitor.
Vimagachi encrypt the significant part of files of a koristuvach: photographs, music, videos, text documents, archives, mail, databases, files with extended programs, etc. the computer has stopped pratsyuvati. Deyak_virusi shut down the old-fashioned recordings of disks and razdіlіv.
For encryption from the system, as a rule, all the latest copies of the update point are seen.
Yak vilikuvati computer from cipher
It is easy to see from an infected system and a shitty program - more of them are easy to cope with, even all antiviruses. Ale! Naivno vvazhati, shho letting the fault lead to the solution of the problem: seeing the virus chi ni, and the files are all encrypted. In addition, for a number of people, I’ll expedite the decryption, as long as it’s possible.
The correct order is on the cob of encryption
- Yak tilki vi remembered the signs of encryption, secretly turn on the computer's life to the onslaught of the buttonsPower for 3-4 seconds... Tse allow uryatuvati hocha b part of the files.
- Create an enforced disk or a USB flash drive with antivirus software on your computer. For example, Kaspersky Rescue Disk 18, DrWeb LiveDisk, ESET NOD32 LiveCD etc.
- Boot the infected machine from the disk and scan the system. See if you know viruses from being saved in quarantine (for vipadoks, as the stench is needed for decryption). Tilki pislya tsyogo you can lock the computer from the hard disk.
- Try to update encrypted files from copies of the system using other systems, or with the help of third-party ones.
Robiti, if the files are encrypted
- Don't waste your hope. On the websites of anti-virus products rozers, there are no scraps of utility-decoders for other types of malware. Zokrema, here are selected utilities from Avastі Kaspersky Labs.
- Having found the type of encoder, download the following utility, obov'yazkovo growth copies shkojenikh filesі try їх encryption. Once you are successful, decipher the sieve.
Iaksho files are not encrypted
Even though the utility didn’t help it, it didn’t help, but it didn’t help you, because you suffered from a virus, and from what left you aren’t.
You can change it into a whole vipad:
- If you are using a paid anti-virus product, you will be sent to the service. Send a few copies of the complete files to the laboratory and check the details. For the obviousness of the technical possibilities, I can help you.
Before speech, Dr.Web- one of nebagatokh laboratories, yak additional help is not deprived of its koristuvacham, but all those who suffer. It is possible to send the file to decrypt the file on the third side.
- As soon as the files were transformed hopelessly, the stink could give you great value, it’s overwhelming to be able to check it out, but it’s hard to know. More often than not, you can update, replace the system and files in the standard, so that you can turn on the hard drive. Visual files in great tributes, reinstallation of the operating system and new updates may amuse you good chance When generating keys for encryption and decryption, it is most often the case that unique identification of the system and copy of the virus is obtained.
Paying a wikup is not an option, there is a possibility that if you take out the key, it will not go to zero. So what a financial business.
Yak to pursue this type of school
If you do not want to repeat it, please, like skinny from reading feelings hundreds of times. So, set up a good antivirus, do not push for a little bit, it’s very important. However, as it showed life, charming pilgrims, as to give you a 100% guarantee of security, this year is not.
A single divine method for the sake of such zdirniks - backup copyіnshі physical nosії, sprouting at hmarnі servants. Backup, backup, backup ...